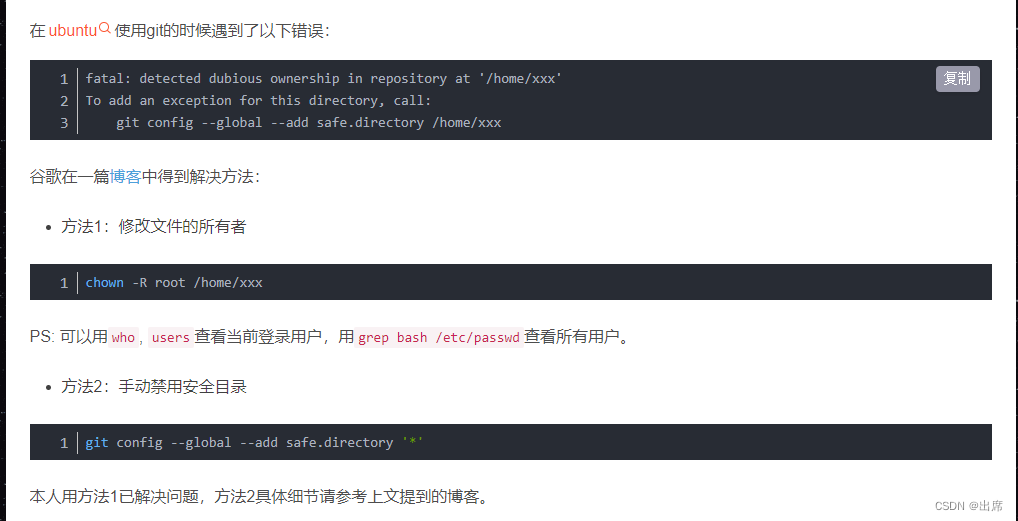
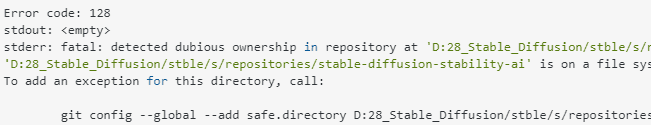
Detected Dubious Ownership In Repository At
Managing ownership and access rights in software repositories is crucial for maintaining the integrity and security of codebases. However, there are instances where dubious ownership can arise, posing potential risks and complications for repository management. This article will delve into the concept of dubious ownership, the signs to detect it, techniques for investigating ownership legitimacy, challenges faced in identifying dubious ownership, its impacts on a repository and its users, and strategies for handling such issues.
II. Understanding the Concept of Dubious Ownership
Dubious ownership refers to instances where the ownership of a repository is questionable or suspicious. It could involve situations where unauthorized users gain control over a codebase, or when legitimate owners become inactive or abandon their responsibilities. Dubious ownership can obstruct the smooth collaboration, version control, and maintenance of a repository, potentially leading to code vulnerabilities, unauthorized changes, or loss of important data.
III. Detecting Signs of Dubious Ownership in a Repository
Several signs may indicate the presence of dubious ownership in a repository. These signs include:
1. Unusual User Behaviors: Frequent changes in ownership, management, or access permissions without any apparent reasons might suggest dubious ownership.
2. Anomalies in Commit History: Unexplained or suspicious commits made by unfamiliar users, especially if they involve critical code alterations, could raise concerns about dubious ownership.
3. Abandoned or Inactive Ownership: A repository with no active owners or contributors for a considerable period may indicate that ownership is in question.
4. Unauthorized Access: Unintentional or unauthorized sharing of repository credentials can grant dubious ownership to malicious users.
IV. Key Indicators of Potentially Dubious Ownership
To identify potentially dubious ownership, look for the following key indicators:
1. Ownership Transfer Anomalies: Frequent, abrupt, or unauthorized transfers of repository ownership can indicate dubious ownership.
2. Unexpected Changes in Collaborator List: Sudden removal of trusted collaborators or addition of unknown individuals may be a sign of dubious ownership.
3. Inconsistencies in User Contributions: Significant discrepancies in the frequency, quality, or types of contributions made by certain users can raise doubts about their ownership legitimacy.
V. Techniques for Investigating Ownership Legitimacy
To investigate ownership legitimacy, consider the following techniques:
1. Examine Commit History: Analyze the commit history for patterns that indicate dubious ownership, such as unusual user activity, inappropriate modifications, or unauthorized code merges.
2. Verify Collaborator Activity: Evaluate the activity level, consistency, and quality of contributions made by repository collaborators to determine if they are actively involved or merely placeholders for dubious ownership.
3. Contact Previous Owners: Reach out to previous owners or contributors to verify ownership transfers, repository history, and possible concerns related to dubious ownership.
VI. Challenges in Identifying Dubious Ownership
Identifying dubious ownership can present several challenges, including:
1. Lack of Historical Data: In some cases, repository history may not provide sufficient information on ownership transfers or changes, making it difficult to determine ownership legitimacy.
2. Anonymous or Pseudonymous Users: Users operating under pseudonyms or anonymous identities can complicate ownership verification.
3. Varying Collaboration Platforms: Repositories can be hosted on different platforms, each with its own authentication and access control mechanisms, making it challenging to gather comprehensive ownership information.
VII. Impact of Dubious Ownership on a Repository and Its Users
Dubious ownership can have severe consequences for a repository and its users:
1. Security Risks: Unauthorized ownership can lead to the introduction of malicious code, unauthorized commits, and increased vulnerability to security threats.
2. Code Integrity Compromised: Dubious ownership may result in unregulated code modifications, causing instability, loss of functionality, and difficulties in tracking changes.
3. Collaboration Disrupted: Ownership disputes, inconsistency in access permissions, or unauthorized ownership transfers can disrupt collaboration among developers, causing delays, confusion, and conflicts.
VIII. Strategies and Best Practices for Handling Detected Dubious Ownership
When dubious ownership is detected, it is crucial to follow established strategies and best practices, including:
1. Prompt Communication: Initiate discussions with collaborators to investigate ownership legitimacy, assess the situation, and gain a comprehensive understanding of the issues at hand.
2. Evaluate Supporting Evidence: Gather relevant data, such as commit history, user contributions, ownership transfer records, or corroborating statements, to substantiate claims of dubious ownership.
3. Transfer Ownership Responsibly: If dubious ownership is confirmed, initiate a responsible and transparent transfer of ownership to trustworthy individuals or organizations to ensure the long-term stability and security of the repository.
IX. Ensuring Trustworthiness and Transparency in Repository Ownership Management
To prevent or address dubious ownership issues, it is essential to implement practices that promote trustworthiness and transparency in repository ownership management:
1. Regular Ownership Reviews: Periodically review ownership and access rights, ensuring only trusted individuals have appropriate access and regularly verify their participation and activity.
2. Implement Two-Factor Authentication: Enforce the use of two-factor authentication for repository access to prevent unauthorized ownership transfers.
3. Document Ownership Transfers: Maintain a centralized record of ownership transfers, including relevant details such as the reasons for the transfer, involved parties, and supporting evidence.
4. Regular Backups: Regularly back up repositories to prevent data loss or unauthorized modifications that may occur due to dubious ownership.
By prioritizing trustworthiness, transparency, and effective ownership management, repositories can safeguard against dubious ownership and maintain the integrity and security of their codebases.
Git Fatal: Detected Dubious Ownership In Repository
Keywords searched by users: detected dubious ownership in repository at Detected dubious ownership in repository, Is owned by but the current user is git, error: cannot open .git/fetch_head: permission denied, Git delete remote repository, Failed to push to the remote repository see the output window for more details, Permission denied (publickey fatal Could not read from remote repository), Git add safe directory recursively, error: remote origin already exists.
Categories: Top 17 Detected Dubious Ownership In Repository At
See more here: nhanvietluanvan.com
Detected Dubious Ownership In Repository
Introduction:
In the world of software development, collaboration is key. The use of online source code repositories enables developers to work together on projects, contributing and reviewing code to ensure its quality and adherence to best practices. These repositories, such as GitHub, Bitbucket, and GitLab, have revolutionized the way software is built. However, with this convenience comes some inherent risks, one of which is the detection of dubious ownership in a repository.
What is Detected Dubious Ownership?
Detected dubious ownership refers to the identification of suspicious or unauthorized code within a repository, indicating potential security and legal risks. It can occur in multiple scenarios, including:
1. Malicious Contributions: Developers with malicious intent may attempt to inject code into a repository, compromising the security and integrity of the software. This could lead to unauthorized access, data breaches, or other cyber-attacks.
2. Intellectual Property Infringement: Developers unintentionally using or including copyrighted code or other intellectual property without appropriate permission or licensing can lead to legal disputes and liabilities.
3. Breach of Trust: The presence of dubious ownership signals a breach of trust within the collaborative community, undermining the overall credibility of the repository and potentially damaging the reputation of its contributors.
Detecting Dubious Ownership:
Several techniques and tools can be utilized to detect dubious ownership within a repository. These include:
1. Code Review: Manual code reviews by experienced developers can help identify suspicious code contributions. Through careful examination, they can spot discrepancies or inconsistencies that may signal unauthorized or malicious code.
2. Code Analysis Tools: Automated code analysis tools, such as linters and static analyzers, can scan the repository for potential security vulnerabilities or intellectual property infringements. These tools analyze the codebase and compare it against known patterns or standards to identify any deviations.
3. Security Scanners: Specialized security scanning tools can assess the code repository for specific vulnerabilities and threats, including backdoors, injection attacks, or other malicious code components.
Dealing with Dubious Ownership:
When dubious ownership is detected, it is crucial to handle the situation promptly and effectively. The following steps can be taken:
1. Verify Authenticity: Before taking any action, verify the detection of dubious ownership. Confirm the legitimacy of the concern by conducting thorough investigations and reviews.
2. Communication: Notify the repository owner and contributors about the identified dubious ownership. Prompt and transparent communication is essential to mitigate the risks and collaboratively address the issue.
3. Removal and Remediation: Remove the identified dubious code from the repository immediately. Depending on the severity of the issue, consider rolling back to a trusted version or rewriting the affected code to ensure no remnants remain.
4. Legal Considerations: In case of intellectual property infringement, consult legal experts to assess the possible consequences and liabilities. Seek permissions or proper licensing if necessary to avoid legal disputes.
Frequently Asked Questions:
Q1. How often does dubious ownership occur in repositories?
A1. The occurrence of dubious ownership varies, depending on the size and popularity of the repository, the level of code review, and the security measures in place. While it is difficult to provide an exact frequency, detecting dubious ownership should always be a part of code review processes to ensure the integrity of the repository.
Q2. Can code analysis tools guarantee the detection of all dubious ownership?
A2. No, code analysis tools cannot guarantee the detection of all dubious ownership. They primarily rely on predefined patterns and heuristics, which may not cover all possible scenarios. Manual code review, combined with automated tools, provides a more comprehensive approach to identifying dubious ownership.
Q3. How can developers protect themselves from dubious ownership?
A3. Developers can take proactive measures to minimize the risk of dubious ownership by:
– Utilizing strong authentication mechanisms to prevent unauthorized access to their repositories.
– Regularly reviewing pull requests and contributions, paying close attention to potential code discrepancies.
– Employing automated code analysis tools and security scanning tools to identify any vulnerabilities or suspicious code.
– Following any licensing requirements and ensuring proper attribution of open-source code.
Conclusion:
Detecting dubious ownership in a code repository is essential to thwart potential security risks and legal liabilities. The collaborative nature of software development necessitates a thorough and continuous review of code contributions. By implementing proper security measures, conducting diligent code reviews, and utilizing automated tools, developers can mitigate the risks associated with dubious ownership. It is imperative to address any concerns promptly, ensuring the integrity of the repository and maintaining trust within the developer community.
Is Owned By But The Current User Is Git
When working with the Git version control system, you might come across the message “Is owned by but the current user is git.” This situation can be quite puzzling, especially for beginners. In this article, we will delve into this error message, exploring its causes, possible solutions, and provide answers to some frequently asked questions.
To begin, let’s understand the meaning behind the error message. The phrase “Is owned by” indicates that the mentioned file or directory is currently owned by a different user on the system. This ownership is typically determined by the file’s permissions or the user who created the file. On the other hand, “the current user is git” implies that the current user executing the Git command is the git user.
There are a few common scenarios where you might encounter this error:
1. File ownership issue: If a file or directory is owned by a user other than the one running the Git command, you are likely to encounter this error. This can occur when someone else initially creates the file or when file permissions change unexpectedly.
2. Misconfigured user: If your Git configuration is incorrectly set up, the command might be executed by the git user rather than your own user account. This misconfiguration can lead to file ownership conflicts.
Now that we have a grasp of the error, let’s discuss potential solutions to resolve “Is owned by but the current user is git” error:
1. Change file ownership: To rectify this issue, you can change the ownership of the file to the current user running the Git command. Utilize the “chown” command in the terminal, followed by the desired user and file path. For example: `sudo chown youruser:youruser file.txt`. Replace “youruser” with your actual username and “file.txt” with the respective file path.
2. Adjust user configuration: In case your Git configuration is causing the command to execute as the git user, you can modify the user configuration. Use the following commands to check and modify the user configuration:
“`
$ git config user.name
$ git config user.email
$ git config –global user.name yourname
$ git config –global user.email [email protected]
“`
Ensure that you are setting the correct user name and email associated with your account.
3. Permission fixes: Occasionally, incorrect file permissions can cause this error. Verify and correct the permissions for the file or directory using the “chmod” command. For instance: `chmod u+rwx file.txt` grants read, write, and execute permissions to the file’s owner.
Frequently Asked Questions:
Q1. Why did I encounter this error after switching to a different computer?
A1. The error arises because the file or directory you are trying to interact with was created or owned by a different user on your old computer. You need to adjust the ownership on the new machine.
Q2. Can I run Git commands as the git user?
A2. While it is possible to configure Git to execute commands as the git user, it is generally recommended to use your own user account when interacting with Git repositories. Running commands as the git user might lead to unexpected issues related to file ownership.
Q3. Are there any potential risks in changing file ownership?
A3. Changing file ownership might not be ideal if multiple users rely on the file simultaneously. Ensure you consider the broader context before modifying ownership.
Q4. What if I encounter permission denied errors while attempting to change file ownership or permissions?
A4. Changing file ownership or permissions often requires administrative privileges. Prefix your commands with “sudo” to gain the necessary elevated privileges.
In summary, the “Is owned by but the current user is git” error occurs when a file or directory is owned by a different user than the one running the Git command. To resolve this error, you can change the file ownership, adjust your user configuration, or fix file permissions. Remember to exercise caution when modifying ownership and permissions to avoid unintended consequences. Happy Git-ing!
Images related to the topic detected dubious ownership in repository at

Found 35 images related to detected dubious ownership in repository at theme




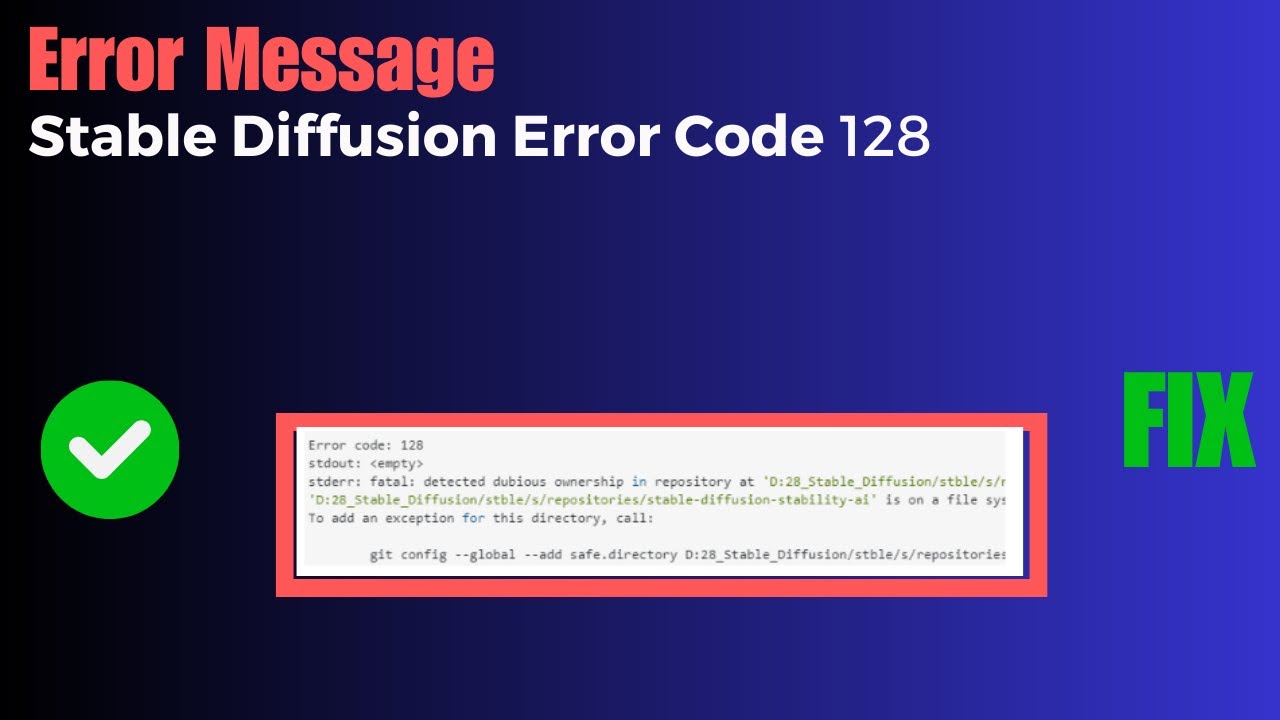
![Git] fatal: detected dubious ownership in repository at is owned by Git] Fatal: Detected Dubious Ownership In Repository At Is Owned By](https://blog.kakaocdn.net/dn/DC86k/btr2FgluLj8/fIDIhCecLkxQNwn5ziKFdK/img.png)




![Duda] fatal: detected dubious ownership in repository | Git y GitHub: controle y comparta su código | Solucionado Duda] Fatal: Detected Dubious Ownership In Repository | Git Y Github: Controle Y Comparta Su Código | Solucionado](https://cdn1.gnarususercontent.com.br/6/530409/a28e7aa4-767e-48f1-a2f6-48a7e2c44803.jpg)




















![git]操作時にdetected dubious ownership in repositoryが発生するようになった - Qiita Git]操作時にDetected Dubious Ownership In Repositoryが発生するようになった - Qiita](https://qiita-user-contents.imgix.net/https%3A%2F%2Fcdn.qiita.com%2Fassets%2Fpublic%2Farticle-ogp-background-9f5428127621718a910c8b63951390ad.png?ixlib=rb-4.0.0&w=1200&mark64=aHR0cHM6Ly9xaWl0YS11c2VyLWNvbnRlbnRzLmltZ2l4Lm5ldC9-dGV4dD9peGxpYj1yYi00LjAuMCZ3PTkxNiZ0eHQ9JTVCZ2l0JTVEJUU2JTkzJThEJUU0JUJEJTlDJUU2JTk5JTgyJUUzJTgxJUFCZGV0ZWN0ZWQlMjBkdWJpb3VzJTIwb3duZXJzaGlwJTIwaW4lMjByZXBvc2l0b3J5JUUzJTgxJThDJUU3JTk5JUJBJUU3JTk0JTlGJUUzJTgxJTk5JUUzJTgyJThCJUUzJTgyJTg4JUUzJTgxJTg2JUUzJTgxJUFCJUUzJTgxJUFBJUUzJTgxJUEzJUUzJTgxJTlGJnR4dC1jb2xvcj0lMjMyMTIxMjEmdHh0LWZvbnQ9SGlyYWdpbm8lMjBTYW5zJTIwVzYmdHh0LXNpemU9NTYmdHh0LWNsaXA9ZWxsaXBzaXMmdHh0LWFsaWduPWxlZnQlMkN0b3Amcz03YmQ5ZDQ2YTI0OTAzYjJmMjI2OTk1MGU5ZmZlMTQ3YQ&mark-x=142&mark-y=112&blend64=aHR0cHM6Ly9xaWl0YS11c2VyLWNvbnRlbnRzLmltZ2l4Lm5ldC9-dGV4dD9peGxpYj1yYi00LjAuMCZ3PTYxNiZ0eHQ9JTQwbmVrb3RvdW1hMDExNCZ0eHQtY29sb3I9JTIzMjEyMTIxJnR4dC1mb250PUhpcmFnaW5vJTIwU2FucyUyMFc2JnR4dC1zaXplPTM2JnR4dC1hbGlnbj1sZWZ0JTJDdG9wJnM9ZjEzZTlmYzhjMjc2MWEzZWYzMGM1YzVhN2QzOWFlY2Y&blend-x=142&blend-y=491&blend-mode=normal&s=25cf35682e8b2af5a65e82267be899b7)
![Git] fatal: detected dubious ownership in repository at is owned by Git] Fatal: Detected Dubious Ownership In Repository At Is Owned By](https://img1.daumcdn.net/thumb/C176x176/?fname=https://blog.kakaocdn.net/dn/bkDR44/btr0gBM2hi8/ztNe9FdEVK7dtkgVj6xTKk/img.png)
Article link: detected dubious ownership in repository at.
Learn more about the topic detected dubious ownership in repository at.
- git submodule update failed with ‘fatal: detected dubious …
- Git detect dubious ownership in repository | by Dennis – Medium
- Git command returns fatal error about the repository being …
- Git “fatal: detected dubious ownership in repository”
- Little Git Tricks: Fix a Dubious Ownership of a Repository
- Detected dubious ownership in repository with Jenkins upgrade
- Git can not create new branch – detected dubious ownership …
See more: nhanvietluanvan.com/luat-hoc