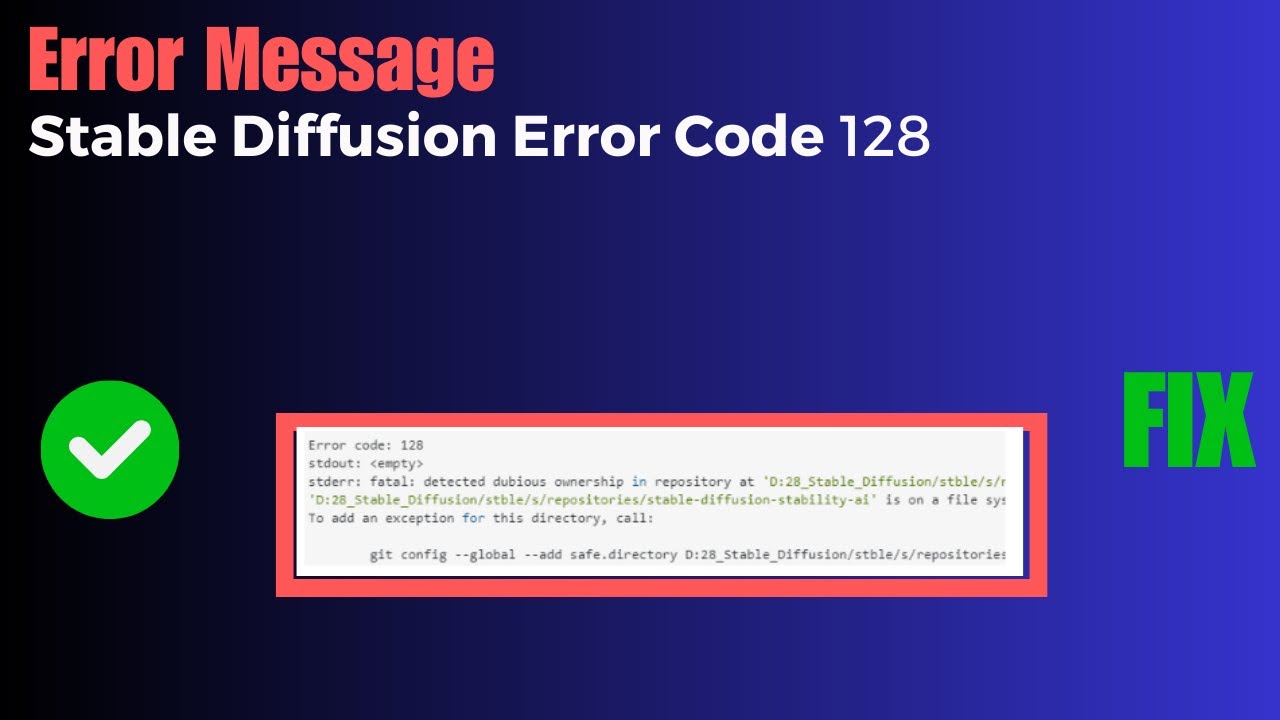
Detected Dubious Ownership In Repository
Introduction
The detection of dubious ownership in a repository is a crucial aspect of maintaining the integrity and security of a codebase. Dubious ownership refers to a situation where the ownership of a repository is compromised or unauthorized individuals gain access to it. This article aims to explore the concept of dubious ownership, its importance, common indicators, potential consequences, strategies for detection, steps to take when detected, and preventive measures.
What is Dubious Ownership?
Dubious ownership in a repository occurs when an unauthorized person gains control or access to the repository, leading to potential security threats and data breaches. It can be a result of various factors, including compromised user accounts, improper access controls, insecure connections, or inadequate permissions.
Why is it Important to Detect Dubious Ownership in a Repository?
Detecting dubious ownership is crucial for maintaining the security and integrity of a repository. Here are some key reasons why it is important:
1. Protecting Intellectual Property: Unauthorized access to a repository can lead to the theft or misuse of valuable source code, algorithms, or designs, potentially causing financial losses to the organization.
2. Preventing Malicious Activity: Dubious ownership can provide opportunities for cybercriminals to introduce malicious code, injecting vulnerabilities or backdoors into the repository. This can lead to various malicious activities, such as data breaches or unauthorized access to sensitive information.
3. Maintaining Code Quality: Detecting dubious ownership helps ensure that only authorized individuals with the necessary expertise can contribute to the codebase. Unauthorized access may result in improper modifications, leading to poor code quality and potential system failures.
4. Maintaining Compliance: Depending on the industry and regulations, organizations may need to demonstrate compliance with certain security standards. Detecting and addressing dubious ownership helps meet these requirements.
Common Indicators of Dubious Ownership
Identifying indicators of dubious ownership can greatly assist in detecting potential security compromises. Some common indicators include:
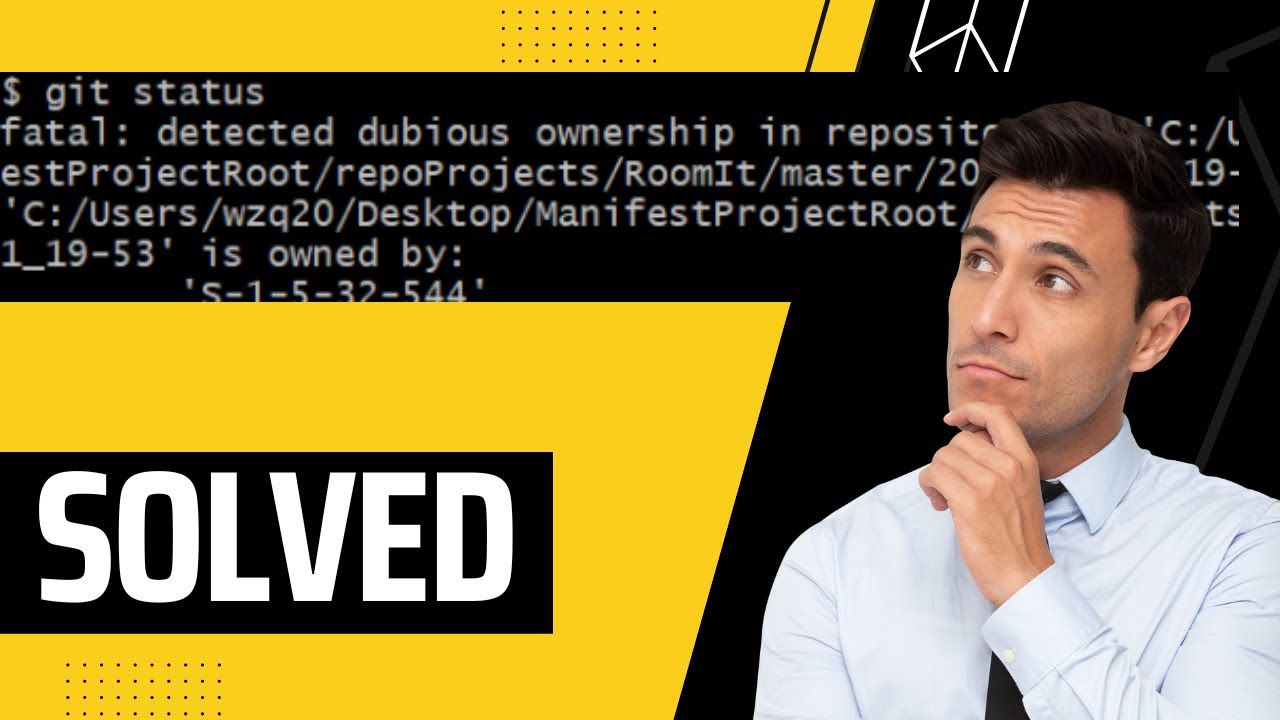
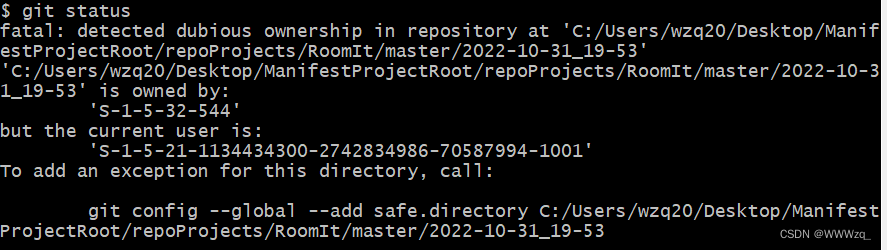
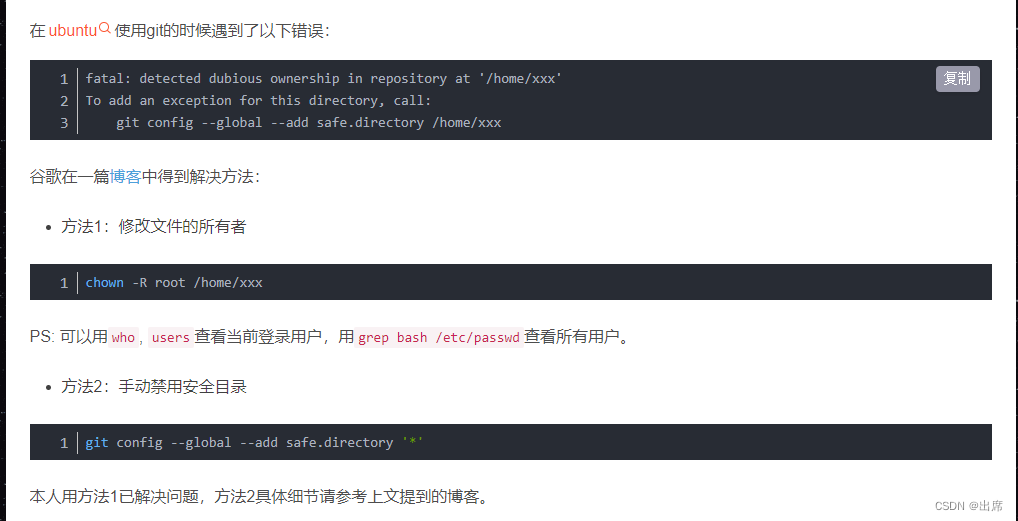
1. Detected Dubious Ownership in Repository at: This message may appear when accessing the repository’s logs or while attempting to perform certain actions, indicating a possible unauthorized presence.
2. “Is owned by but the current user is git”: This error message suggests that the repository is owned by a different user than the one attempting to access, which could indicate unauthorized access or control.
3. Git Config: Unauthorized changes to the repository’s configuration files, such as user credentials or remote repository settings, may indicate dubious ownership.
4. Unsafe Repository: Repositories lacking proper access controls, including weak or default passwords, inadequate encryption, or outdated software versions, are prone to dubious ownership.
5. Permission Denied (publickey fatal Could not read from remote repository): This error indicates that the SSH key required for authorized access is not available, potentially due to unauthorized changes or misconfiguration.
The Potential Consequences of Dubious Ownership
Dubious ownership can have severe consequences for both individuals and organizations. Some potential consequences include:
1. Loss of Intellectual Property: Unauthorized access to proprietary source code or sensitive information can result in the theft or loss of valuable intellectual property, leading to financial damages and loss of competitiveness.
2. Data Breaches: Dubious ownership provides an opportunity for adversaries to access sensitive data, compromising the privacy and security of both individuals and organizations.
3. Malware Injection: Unauthorized individuals can introduce malicious code, leading to further attacks, system vulnerabilities, and potential disruptions.
4. Reputational Damage: If a repository under dubious ownership is discovered and subsequently linked to a security breach, an organization’s reputation may be tarnished, eroding trust from partners, clients, and customers.
Strategies for Detecting Dubious Ownership
To effectively detect dubious ownership in a repository, consider employing the following strategies:
1. Monitor Access Logs: Regularly review access logs to identify any suspicious or unauthorized activity, such as unusual login attempts or access from unfamiliar IP addresses.
2. Implement Multi-Factor Authentication (MFA): Enforce strong authentication mechanisms, such as MFA, to ensure that only authorized individuals can access the repository.
3. Conduct Regular Audits: Perform periodic audits of user accounts, permissions, and access controls to ensure that only authorized users have the necessary privileges.
4. Employ Intrusion Detection Systems (IDS): Utilize IDS tools to detect and prevent unauthorized access attempts or suspicious activities within the repository.
5. Implement Security Policies: Establish and enforce clear security policies regarding repository access, usage guidelines, and responsibilities to minimize the risk of dubious ownership.
Steps to Take When Dubious Ownership is Detected
If dubious ownership is detected in a repository, it is crucial to take immediate action to mitigate the potential risks. Here are some recommended steps:
1. Temporarily Disable Access: Temporarily suspend access to the compromised repository to prevent further unauthorized activities.
2. Notify Relevant Parties: Inform key stakeholders, such as the IT department, security personnel, and the repository’s users, about the detected dubious ownership, providing them with necessary details.
3. Investigate the Incident: Conduct a thorough investigation to determine the extent of the compromise, the potential impact, and the underlying cause of the dubious ownership.
4. Remove Unauthorized Access: Identify and remove any unauthorized user accounts, SSH keys, or other credentials from the repository to regain control and prevent further compromise.
5. Restore from a Trusted Backup: If necessary, restore the repository from a trusted backup to ensure that all unauthorized modifications are eliminated.
Preventing Dubious Ownership in Repositories
While detection and response are essential, it is equally important to proactively prevent dubious ownership. Consider the following preventive measures:
1. Implement Secure Authentication Mechanisms: Utilize strong authentication methods, including MFA and secure password policies, to reduce the risk of unauthorized access.
2. Regularly Update Software: Keep all repository software and dependencies up to date, including the underlying operating system, Git server, and related plugins, to ensure the latest security patches are applied.
3. Limit Access Permissions: Apply the principle of least privilege, granting users only the necessary permissions to minimize the potential attack surface.
4. Educate Users: Train repository users on best practices for security, including the identification of phishing attempts, secure password management, and the reporting of suspicious activities.
5. Conduct Penetration Testing: Periodically engage in penetration testing exercises to identify potential vulnerabilities and loopholes in the repository’s security defenses.
FAQs
Q1. Can dubious ownership lead to legal consequences?
A1. Yes, unauthorized access to a repository, resulting in theft or misuse of proprietary information, can lead to legal consequences, such as intellectual property theft or violation of data protection laws.
Q2. How often should access logs be reviewed?
A2. It is recommended to review access logs regularly, ideally in real-time or at least on a daily or weekly basis, to catch any suspicious activities in a timely manner.
Q3. What should I do if my repository is compromised?
A3. If your repository is compromised, follow the steps mentioned earlier: temporarily disable access, notify relevant parties, investigate the incident, remove unauthorized access, and restore from a trusted backup if necessary.
Q4. Can preventive measures guarantee 100% security?
A4. While adopting preventive measures significantly reduces the risk, it cannot guarantee absolute security. A holistic approach that includes detection, response, and ongoing security assessments is essential.
Conclusion
The detection of dubious ownership in a repository is essential for maintaining the security, integrity, and reputation of an organization. By understanding the importance of detecting and preventing dubious ownership, recognizing common indicators, and implementing effective strategies, organizations can enhance their defenses and minimize the risk of unauthorized access. Remember, staying vigilant, regularly updating security measures, and educating repository users are crucial components of a robust security framework.
Git Fatal: Detected Dubious Ownership In Repository
Keywords searched by users: detected dubious ownership in repository Detected dubious ownership in repository at, Is owned by but the current user is git, Git config, Unsafe repository, Permission denied (publickey fatal Could not read from remote repository), Failed to push to the remote repository see the output window for more details, Git connect to remote repository, error: remote origin already exists.
Categories: Top 71 Detected Dubious Ownership In Repository
See more here: nhanvietluanvan.com
Detected Dubious Ownership In Repository At
Introduction:
In today’s fast-paced technological era, the open-source community thrives on collaboration, sharing, and transparency. However, occasionally, issues arise when dubious ownership is detected within a repository. Such instances can significantly impact the overall trust in a project and jeopardize the integrity of the entire open-source ecosystem. In this article, we will delve into the concept of detected dubious ownership in a repository, shed light on its implications, and address FAQs surrounding this critical issue.
Understanding Detected Dubious Ownership:
Detected dubious ownership refers to the identification of questionable individuals or organizations who claim ownership of a repository in the open-source environment. It entails discovering instances where the assigned ownership conflicts with the actual contributions or origins of a project. Such discrepancies may arise due to various factors, including intentional misrepresentation, unclear attributions, or unauthorized transfers of ownership.
Implications of Detected Dubious Ownership:
1. Misrepresentation of Contribution: Dubious ownership can create an inaccurate representation of an individual’s or organization’s contribution to a repository. This not only distorts the perception of the actual contributors but also undermines their well-deserved credibility and recognition within the community.
2. Legal and Licensing Issues: Detected dubious ownership may lead to legal complexities surrounding intellectual property rights and licensing obligations. It can raise concerns about compliance with licenses and the potential violation of copyright or other legal agreements.
3. Community Trust and Integrity: The open-source ecosystem thrives on trust and collaboration. When dubious ownership is detected, it can erode the trust of contributors and users in a repository. This loss of trust impacts the overall integrity of the project and may deter potential users from engaging with the codebase.
4. Project Governance and Decision-Making: Dubious ownership challenges the governance structure of a project. Inaccurate ownership claims can result in individuals exerting unauthorized influence or control over project decisions, potentially jeopardizing the project’s direction or impeding necessary improvements.
Detecting Dubious Ownership:
Identifying instances of dubious ownership in a repository typically requires a meticulous analysis of historical records, code contributions, and public discussions. Some common techniques used to detect dubious ownership include:
1. Analyzing Commit History: Studying the patterns of code contributions, commit activity, and the timeline of the repository can help uncover suspicious ownership claims. Inconsistencies in the commit authorship or instances of a sudden spike in ownership transfers may indicate potential red flags.
2. Investigating Code Contributions: Scrutinizing the code contributions of individuals or organizations claiming ownership is key to uncovering dubious ownership. Examining code quality, depth of expertise, and the nature of contributions can provide insights into the legitimacy of ownership.
3. Community Engagement Research: Actively monitoring mailing lists, public forums, and interaction patterns within the community can reveal discrepancies and conflicting claims of ownership. Be on the lookout for instances where ownership is asserted without any supporting evidence or documentation.
Frequently Asked Questions (FAQs):
Q1. How can I protect my repository from dubious ownership claims?
A1. To safeguard your repository, maintain thorough and well-documented records of ownership. Employ version control tools and practices, such as GPG-signed commits, to establish a clear attribution trail. Additionally, engage with the community and encourage transparency to deter potential instances of dubious ownership.
Q2. What should I do if I suspect dubious ownership in a repository I contribute to?
A2. If you have concerns about dubious ownership, first carefully gather evidence to support your suspicions. Once you have substantial findings, reach out to the project maintainers, the community leadership, or relevant platform administrators to report your concerns. It is crucial to maintain open communication and gather support from other contributors.
Q3. Can detected dubious ownership be legally contested?
A3. The legal implications of detected dubious ownership can vary, and seeking legal advice tailored to your jurisdiction is essential. Depending on the severity of the issue, it may be necessary to consider consulting legal experts who specialize in intellectual property rights or open-source licensing.
Q4. How can the community prevent future instances of dubious ownership?
A4. Promoting a culture of transparency and accountability within the open-source community is vital in deterring dubious ownership claims. Establishing clear guidelines for code attribution, showcasing contributors’ profiles, and conducting periodic audits of ownership records can instill confidence among contributors and users.
Conclusion:
Detected dubious ownership in a repository can have significant repercussions on the open-source community. By understanding the implications and employing effective detection techniques, we can uphold the integrity and trustworthiness of the projects we collaborate on. By promoting transparency and encouraging accountability, we can ensure the continued success of the open-source ecosystem.
Is Owned By But The Current User Is Git
In the world of version control systems, Git has emerged as one of the most popular and widely used tools. It provides developers with the ability to track changes in their codebase, collaborate efficiently with others, and manage projects seamlessly. However, if you have ever encountered the message “is owned by but the current user is git,” you might be left wondering what it means and how to resolve it. In this article, we will dive into this topic in depth and provide a comprehensive understanding of this particular error message.
Understanding Ownership and Permissions in Git
To understand the “is owned by but the current user is git” message, we first need to grasp the concepts of ownership and permissions within Git. Git, like any other version control system, operates within a file system where each file and directory has an owner and a set of permissions. The owner is usually the user who created or owns the file, while the permissions dictate who can read, write, or execute the file.
When you initialize a Git repository or clone an existing one, the files and directories are assigned an owner based on the user who executed the Git command. By default, this owner is set to the current user performing the action, which often corresponds to your username on the system. However, in some cases, you may encounter situations where the owner of the files is different from the current user.
Resolving “Is Owned by but the Current User is git” Error
The “is owned by but the current user is git” error typically occurs when the files or directories in a Git repository have different owners. This disparity can arise when different users execute Git commands, such as cloning or pulling changes, on the same repository. In such cases, Git tries to preserve the ownership and permissions of the files, leading to a conflict if the current user does not match the file’s owner.
One common scenario where this error occurs is when performing Git operations on a remote server where the owner of the repository files and directories is set to a user named “git.” This practice is prevalent when using Git alongside other collaboration or deployment tools, such as GitLab or GitHub.
To resolve this error, you need to adjust the ownership of the affected files and directories to match the current user. The solution may vary depending on the operating system or file system you are using. On Unix-based systems (e.g., Linux or macOS), you can use the “chown” command to change the ownership.
For example, if your username is “john” and you encounter the error in a directory called “my_project,” you can change the ownership by executing:
“`
sudo chown -R john my_project
“`
This command recursively changes the ownership of the “my_project” directory and all its contents to the user “john.” On Windows, the process to change ownership may differ, but you can usually accomplish it through the file properties window or using the “icacls” command.
FAQs
Q: Can I ignore the “is owned by but the current user is git” error?
A: It is generally not advisable to ignore this error, as it may indicate a mismatch in ownership and can potentially lead to issues with accessing or modifying files within the Git repository. Resolving the error ensures proper functioning of Git.
Q: Can I set a default user for Git operations?
A: Yes, you can configure Git to use a specific user as the default for all operations. You can either globally set a default user through the “git config” command or set it locally within a specific repository.
Q: What other errors might be encountered when using Git?
A: Git is a powerful tool with numerous features, and users may encounter various error messages depending on their actions and configurations. Some common errors include merge conflicts, inadequate permissions, and issues with remote repositories.
Q: How can I avoid ownership conflicts in collaborative Git workflows?
A: To minimize ownership conflicts, it is recommended to establish a standard user or user group that owns the Git repository files. Ensure that all collaborators use the same user credentials when performing Git operations. Additionally, emphasizing communication and coordination among team members can help prevent conflicts.
In conclusion, the “is owned by but the current user is git” error message in Git highlights a discrepancy between the ownership of files and the current user executing Git commands. Resolving this error involves adjusting the ownership of affected files and directories to match the current user. By understanding ownership and permissions in Git, users can tackle such errors effectively and maintain a smooth version control workflow.
Git Config
Introduction:
Git, developed by Linus Torvalds, is a powerful version control system widely used in software development. With Git, developers can efficiently manage and track changes in their projects. One of the key aspects that contribute to Git’s flexibility is its extensive configuration options. In this article, we will delve deep into Git config, exploring its various functionalities, and providing insights on how to effectively configure Git to suit your specific needs.
Understanding Git Config:
Git config is a command-line tool that allows users to set and retrieve Git configuration variables. These variables control the behavior of Git, influencing everything from user-specific preferences to repository-specific settings. Git config offers three levels of configuration: system-level, user-level, and repository-level. This hierarchical structure ensures that configuration options can be defined globally, per user, or on a per-repository basis, enabling a versatile and customizable Git environment.
Configuring Git:
1. Configuring System-level Settings:
Git config options at the system level apply to all users on a machine. To set these variables, use the `git config –system` command. System-level configuration is stored in the `/etc/gitconfig` file. This file can be edited directly or through the `git config` command.
2. Configuring User-level Settings:
User-level configurations apply to a specific user account. These settings can be set using the `git config –global` command. User-level configuration is stored in the `~/.gitconfig` file. The `–global` flag ensures that the provided values will be applied globally across all repositories associated with the user.
3. Configuring Repository-level Settings:
Git config also allows configuring settings at a repository level, storing them in the `.git/config` file within the repository’s directory. To set repository-level configurations, use the `git config` command without the `–global` flag. These settings will only apply to the specific repository in which they are defined.
Commonly Used Git Config Settings:
1. User Information:
Git config allows users to set their name and email address, which are important for identifying the authorship of commits. Use the following commands to configure user information:
`$ git config –global user.name “Your Name”`
`$ git config –global user.email “[email protected]”`
2. Editor Preferences:
Git uses an editor to edit commit messages. Configure your preferred text editor using:
`$ git config –global core.editor “editor”`
3. Aliases:
Git aliases allow users to set up command shortcuts for frequently-used operations. Create an alias using the command:
`$ git config –global alias.[alias-name] [command]`
4. Merge and Diff Settings:
Git config offers options to set default merge and diff tools. These settings are valuable for resolving conflicts and viewing differences between files.
5. Ignore File Patterns:
Git allows users to specify files and patterns to be ignored during repository operations. To configure ignore patterns, modify the `.gitignore` file or use `git config`.
FAQs:
1. How can I check my current Git configuration?
To view the complete Git configuration, use the command:
`$ git config –list`
2. Can I have multiple Git configurations on the same machine?
Yes, Git allows configuring multiple environments using system-level, user-level, and repository-level configurations.
3. How can I remove a specific Git configuration option?
To remove a specific Git configuration option, use the following command:
`$ git config –global –unset [option]`
4. Can I override user-level configurations with repository-level settings?
Yes, repository-level settings override user-level settings, ensuring greater flexibility and customization for individual projects.
5. Can I track Git configuration changes within a repository?
Yes, by committing the `.gitconfig` file within a repository, you can track configuration changes as part of your version control.
Conclusion:
Git config provides an extensive range of configuration options to fine-tune your Git experience. With three levels of configuration available, Git empowers developers to tailor settings globally, per user, and per repository. Understanding and effectively utilizing Git config can significantly enhance productivity and streamline Git operations. Experiment with different settings to mold Git according to your preferences and enjoy the full potential of this versatile version control system.
Images related to the topic detected dubious ownership in repository

Found 32 images related to detected dubious ownership in repository theme



![git] fatal: detected dubious ownership in repository at Git] Fatal: Detected Dubious Ownership In Repository At](https://blog.kakaocdn.net/dn/cHDTWt/btrJV7aYUO3/WioPJiu4KPBtuaIULpZ0QK/img.png)



![git 에러] fatal: detected dubious ownership in repository at 해결 방법 Git 에러] Fatal: Detected Dubious Ownership In Repository At 해결 방법](https://blog.kakaocdn.net/dn/cQCWVD/btrXqDTLxmR/ZRlFCTaWajXuIFlvtHJk20/img.png)





![오류] fatal: detected dubious ownership in repository at '경로' 오류] Fatal: Detected Dubious Ownership In Repository At '경로'](https://velog.velcdn.com/images/ovzip/post/2edb4d06-ff5b-4837-a8cc-a72d17cc792d/image.png)








Article link: detected dubious ownership in repository.
Learn more about the topic detected dubious ownership in repository.