Server Not Found In Kerberos Database
The Kerberos authentication protocol is widely used in computer networks to provide secure communication between systems. It relies on a centralized database, known as the Kerberos database, to authenticate users and verify their access to resources. However, there are instances when the server is not found in the Kerberos database, resulting in authentication failures. In this article, we will explore the causes, impact, and troubleshooting techniques for such errors.
Explanation of the Kerberos Authentication Protocol
1. Overview of the Kerberos authentication system:
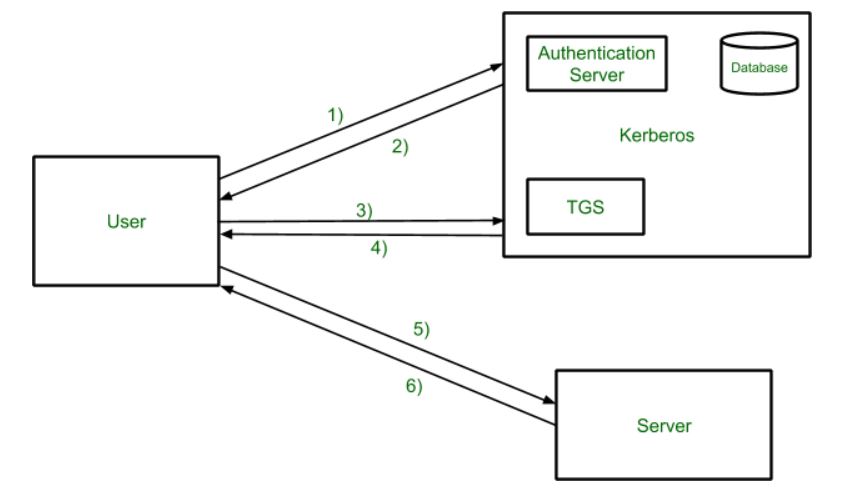
The Kerberos authentication protocol is designed to provide secure authentication in a networked environment. It uses a client-server model with a trusted third-party, called the Key Distribution Center (KDC), to facilitate the authentication process.
2. Components of the Kerberos infrastructure:
The key components of a Kerberos infrastructure include the KDC, which consists of an Authentication Server (AS) and a Ticket Granting Server (TGS), as well as the clients and servers that participate in the authentication process.
3. Role of the Kerberos database in the authentication process:
The Kerberos database stores the authentication credentials, such as usernames, passwords, and secret keys. It is used by the KDC to validate client requests and generate tickets that grant access to resources.
Understanding Server Not Found Errors
4. Common causes for “Server not found in Kerberos database” errors:
There are several reasons why a server might not be found in the Kerberos database. Some common causes include incorrect server configuration, misconfiguration of the KDC, expired server tickets, or synchronization issues between the KDC and the server.
5. Impact of server not being found on the authentication process:
When a server is not found in the Kerberos database, the authentication process fails. This can result in denied access to resources, disrupted services, and potential security risks.
6. Potential implications for the user and the network:
For users, a server not found error means they will not be able to access the desired resource or service. It can lead to frustration and productivity loss. From a network perspective, these errors can indicate configuration issues that need to be resolved to ensure a secure and efficient authentication process.
Investigating and Troubleshooting Server Not Found Errors
7. Steps to investigate the root cause of the error:
To identify the root cause of a server not found error, various steps can be taken. These include checking server configurations, verifying KDC settings, reviewing logs and error messages, and testing the communication between the server and the KDC.
8. Analyzing the Kerberos database for inconsistencies:
By examining the Kerberos database, inconsistencies or missing entries related to the server can be identified. This analysis can help pinpoint any issues with the server’s registration or synchronization with the KDC.
9. Resolving server not found errors: Actionable solutions and recommendations:
To resolve server not found errors, solutions may vary depending on the specific cause. These can include updating server configurations, refreshing or re-registering server tickets, re-syncing the server with the KDC, or contacting technical support for further assistance.
FAQs
Q1: What does “sspi provider: server not found in Kerberos database 851968 sqldriverconnect” mean?
A1: This error typically occurs in SQL Server environments and indicates that the server’s principal is not found in the Kerberos database. It suggests a misconfiguration or synchronization issue between the SQL Server and the KDC.
Q2: Why am I getting “client not found in Kerberos database” error?
A2: This error message suggests that the client’s principal is not found in the Kerberos database. This could be due to a misconfigured client or issues with the Kerberos database synchronization.
Q3: How can I locate the Kerberos database?
A3: The location of the Kerberos database depends on the specific implementation and operating system. In general, it is stored on the KDC server and can be found in the system’s configuration files or registry.
In conclusion, a server not found error in the Kerberos database can disrupt the authentication process and result in denied access to resources. By understanding the causes, impacts, and troubleshooting techniques associated with these errors, organizations can ensure a secure and reliable authentication infrastructure.
Nfs (With Kerberos) Mount Failing Due To \”Server Not Found In Kerberos Database\” Error
What Is Error 1765328377 In Kerberos?
Kerberos is a widely used authentication protocol that provides secure communication in a distributed environment. It is mainly used in computer networks to authenticate users and encrypts their communication to ensure data security. However, like any complex technology, Kerberos encounters errors and issues that need to be addressed. One such error is error 1765328377, also known as KDC_ERR_PREAUTH_FAILED. In this article, we will delve into the details of this error, understand its causes, and explore possible solutions.
Understanding Kerberos Authentication and Pre-Authentication:
Before diving into the specifics of error 1765328377, it is vital to have a basic understanding of how Kerberos authentication works. Kerberos employs a three-party system involving the client, the Key Distribution Center (KDC), and the service server. The KDC acts as the authentication server, responsible for granting tickets to clients, and authenticating them before accessing network services.
Kerberos incorporates pre-authentication as an additional security layer. When a client attempts to establish a connection with the KDC, it sends a request with an encrypted timestamp, known as the pre-authentication data. This data is used to prove the client’s legitimacy and ensures that only authorized entities can access the KDC.
Error 1765328377 – Causes and Solutions:
Error 1765328377, or KDC_ERR_PREAUTH_FAILED, occurs when the pre-authentication process fails to authenticate the client before granting it access. There can be several causes for this error. Let’s explore some of the common ones along with their potential solutions.
1. Inadequate Configuration:
Sometimes, error 1765328377 can be a result of incorrect configuration settings. Verify that the client and service servers have their clocks synchronized. A time difference between the client and the KDC could lead to authentication failure. Additionally, ensure that the KDC server and client have a proper shared secret key.
2. Invalid or Expired Ticket:
If the client’s ticket is expired or corrupted, it can result in pre-authentication failure. In such cases, the client needs to obtain a new ticket by requesting authentication again. Performing a manual ticket request by removing and re-adding the client to the Kerberos realm might resolve the issue.
3. Incorrect Encryption Type:
Mismatched encryption types between the client and the KDC can also trigger error 1765328377. Ensure that the encryption types used on the client and the KDC server are compatible. If not, update the settings accordingly to allow the correct encryption type.
4. Network Latency:
High network latency can disrupt the exchange of pre-authentication data between the client and the KDC. This can lead to errors such as 1765328377. To mitigate this issue, optimize your network infrastructure and ensure stable and low-latency connections between the client and the KDC server.
Frequently Asked Questions (FAQs):
Q1. How can I troubleshoot error 1765328377 in Kerberos?
A: Start by verifying the time synchronization between the client and the KDC. Check the configuration settings, encryption types, and shared secret keys. You can also recreate the client’s ticket or investigate any network latency issues.
Q2. Can an expired password cause error 1765328377?
A: No, an expired password usually triggers a different error, such as KDC_ERR_KEY_EXP or KDC_ERR_ETYPE_NOSUPP. However, it is essential to maintain up-to-date passwords for secure authentication.
Q3. Are there any tools available to troubleshoot Kerberos errors?
A: Yes, there are various tools like klist, kinit, ksetup, and Wireshark that can help diagnose and troubleshoot Kerberos-related issues. These tools provide insights into ticket information, key distribution, and network traffic.
Q4. Is error 1765328377 specific to a particular operating system?
A: No, error 1765328377 is not limited to a specific operating system. It can occur in any environment that employs the Kerberos authentication protocol.
Q5. Does error 1765328377 affect the overall system security?
A: It can impact the security to some extent as the pre-authentication process failed. However, it is crucial to understand the root cause of the error and apply proper fixes to maintain system security and integrity.
Conclusion:
Error 1765328377, or KDC_ERR_PREAUTH_FAILED, can arise in Kerberos authentication due to different reasons such as misconfiguration, invalid tickets, incompatible encryption types, or network latency issues. Troubleshooting this error involves analyzing and rectifying various aspects, including time synchronization, shared secret keys, encryption types, and network connectivity. By addressing these underlying causes and applying suitable solutions, administrators can ensure smooth and secure authentication within their Kerberos-based systems.
What Is Received Error From Kdc Client Not Found In Kerberos Database?
Kerberos is a widely used authentication protocol that provides secure communication on a network. In a Kerberos system, the Key Distribution Center (KDC) is responsible for managing and distributing the cryptographic keys used for authentication.
The “Received error from KDC client not found in Kerberos database” error message typically occurs when a client tries to authenticate itself to the KDC using a principal (a unique identifier) that is not present in the Kerberos database.
When a client attempts to authenticate, it sends a request to the KDC with its principal and a timestamp. The KDC then checks if the principal exists in its database and if the request is valid. If everything checks out, the KDC issues a ticket-granting ticket (TGT) to the client, allowing it to access network services.
However, if the KDC cannot find the principal in its database, it generates the “Received error from KDC client not found in Kerberos database” error message. This error could indicate a range of possible issues or misconfigurations within the Kerberos system.
Some potential causes include:
1. Principal not created: If the principal associated with the client’s request has not been created in the Kerberos database, the KDC will not be able to find it, resulting in the error.
2. Typographical errors: Typos or spelling mistakes in the client’s principal name or any associated configuration files can prevent the KDC from locating the principal in the database.
3. Database replication issues: In large-scale deployments where multiple KDC servers are used for redundancy, inconsistencies in the replication of the Kerberos database can lead to the error. If one KDC server has the principal while another does not, authentication requests may fail intermittently.
4. Expired or invalid principals: If the principal associated with the client’s request has expired or been deleted from the Kerberos database, the KDC will be unable to locate it, resulting in the error message. This issue may occur if the Kerberos administrator has revoked or removed the principal.
FAQs:
Q: How can I resolve the “Received error from KDC client not found in Kerberos database” error?
A: Here are a few steps to take for troubleshooting:
1. Verify the principal: Double-check that the principal being used by the client is correct and exists in the Kerberos database. Pay attention to any possible spelling mistakes or typographical errors.
2. Check database replication: If you have multiple KDC servers, ensure that the Kerberos database is replicating correctly across all servers. Address any replication issues to ensure consistency.
3. Examine principal expiration: Confirm that the principal associated with the client’s request is not expired or deleted from the Kerberos database. If necessary, recreate or renew the principal as per your organization’s policies.
4. Review configuration files: Check any configuration files related to Kerberos, such as krb5.conf, for any errors or misconfigurations. Correct any discrepancies found.
5. Consult Kerberos logs: Analyze the Kerberos logs on both the client and KDC-side to gain more insight into the error. Look for any specific error codes or additional hints that could pinpoint the issue.
Q: I get the error intermittently, what might be causing this?
A: If the error occurs sporadically, it could indicate a database replication issue. In a multi-server setup, ensure that all KDC servers are synchronized and replicating the Kerberos database correctly. Inconsistencies in the replication process can cause authentication failures intermittently. Address any replication issues and confirm the consistency of the Kerberos database.
Q: Can I fix the error by recreating the principal?
A: Recreating the principal can resolve the error if it was caused by the principal not being created or having been deleted from the Kerberos database. However, ensure that you understand the implications of deleting or recreating principals, as it may also impact any existing services or applications relying on them.
Q: Are there any other troubleshooting steps I can take?
A: In addition to the steps mentioned above, you can also try restarting the KDC servers and performing a flush of the Kerberos ticket cache on the client-side. Additionally, consult any available documentation or support resources related to your specific Kerberos implementation for further guidance.
In conclusion, the “Received error from KDC client not found in Kerberos database” indicates a failure to locate the client’s principal in the Kerberos database during an authentication request. Possible causes include missing or expired principals, typographical errors, or database replication issues. Troubleshooting steps involve verifying principal existence, checking replication, examining principal expiration, reviewing configuration files, and consulting Kerberos logs.
Keywords searched by users: server not found in kerberos database sspi provider: server not found in kerberos database 851968 sqldriverconnect, krb5kdc_err_s_principal_unknown 1765328377 server not found in kerberos database, kvno: server not found in kerberos database while getting credentials for, client not found in kerberos database, server principal not found, Server not found in Kerberos database, not found in kerberos database while getting initial credentials, kerberos database location
Categories: Top 91 Server Not Found In Kerberos Database
See more here: nhanvietluanvan.com
Sspi Provider: Server Not Found In Kerberos Database 851968 Sqldriverconnect
Introduction:
When working with SQL Server, one may occasionally encounter the error message “SSPI Provider: Server Not Found in Kerberos Database 851968 SQLDriverConnect.” This error typically occurs when attempting to establish a connection using Integrated Security and the Kerberos authentication protocol. In this article, we will delve into the intricacies of this error, explore its causes, and provide potential solutions to resolve it.
Understanding the Error:
The “SSPI Provider: Server Not Found in Kerberos Database 851968 SQLDriverConnect” error is related to the Server-based Security Support Provider Interface (SSPI) and the Kerberos authentication protocol. SSPI is a library that abstracts the complexities of different authentication methods, providing a unified interface for applications to authenticate users.
The error message indicates that the server’s Service Principal Name (SPN), used to uniquely identify a service instance, could not be found in the Kerberos database. This typically occurs when the SPN associated with the SQL Server instance is misconfigured or missing.
Causes:
1. Incorrect SPN Configuration: One of the common causes of this error is an incorrect or missing SPN. The SPN is essential for Kerberos authentication to function correctly. If the SPN associated with the SQL Server instance is not properly set up, the Kerberos database cannot find the server.
2. DNS Issues: Another potential cause is DNS-related problems. Kerberos relies on DNS to resolve SPNs to the corresponding server. If there are issues with DNS resolution or misconfigurations, the Kerberos database may fail to locate the server.
3. Active Directory Configuration: Improper configuration of Active Directory (AD) can also lead to this error. AD stores the SPN information used by the Kerberos database. In case AD is not set up correctly, the Kerberos database may not be able to identify the server.
Solutions:
1. Verify and Correct SPN Configuration: The first step in resolving this error is to ensure that the SPN associated with the SQL Server instance is correctly configured. Tools like the Microsoft Kerberos Configuration Manager for SQL Server can aid in checking the SPN settings. If any discrepancies are found, they can be corrected using the setspn command-line tool.
2. Check DNS Configuration: Thoroughly reviewing the DNS configuration is also crucial. Ensure that the SQL Server’s hostname and IP address are properly registered in DNS. Additionally, verify that the DNS server(s) used by the SQL Server can resolve the necessary records correctly.
3. Validate Active Directory Setup: Verify the settings of Active Directory to guarantee correct SPN registration. Ensure that the SQL Server service account has the necessary permissions to register SPNs. If required, review the delegation settings in Active Directory to ensure proper configuration.
4. Enable Kerberos Logging: Enabling Kerberos logging can provide additional information about the error. By enabling this feature, you can generate detailed log files that may help in pinpointing the issue. These logs can be reviewed using tools like Event Viewer.
FAQs:
Q1. Can this error occur with other authentication methods?
Yes, this error is specific to Kerberos authentication. If you are using a different authentication method, such as NTLM, you may encounter different error messages.
Q2. Can this error occur with other applications and services?
Although this article focuses on SQL Server, this error can occur with other applications and services that use Kerberos authentication. The underlying causes and solutions would generally remain the same.
Q3. Are there any prerequisites for using Kerberos authentication with SQL Server?
Yes, several prerequisites must be met for successful Kerberos authentication with SQL Server. These include configuring SPNs correctly, ensuring proper DNS resolution, and setting up Active Directory correctly.
Q4. Are there any alternatives to using Kerberos authentication?
Yes, if Kerberos authentication encounters persistent issues, you can consider using alternative authentication methods like NTLM. However, Kerberos is generally preferred due to its better security and performance characteristics.
Conclusion:
The “SSPI Provider: Server Not Found in Kerberos Database 851968 SQLDriverConnect” error can be a challenging issue to troubleshoot, but understanding its causes and potential solutions should help in resolving it effectively. By properly configuring the SPN, examining DNS settings, and reviewing Active Directory configurations, users can alleviate this error and establish successful connections using Kerberos authentication.
Krb5Kdc_Err_S_Principal_Unknown 1765328377 Server Not Found In Kerberos Database
Kerberos is a widely used authentication protocol that provides secure communication over a network. It is specifically designed to prevent eavesdropping, tampering, and forgery. However, like any other system, Kerberos is not immune to errors and issues. One of the common errors encountered by users is the “krb5kdc_err_s_principal_unknown: Server Not Found in Kerberos Database” error, which can lead to authentication failures and disrupt normal operations. In this article, we will delve into this error, analyze its causes, and explore possible solutions.
Understanding the Error:
When a system encounters the “krb5kdc_err_s_principal_unknown” error, it means that the Kerberos Key Distribution Center (KDC) cannot find the server’s principal in its database. A principal is an entity that is authenticated by Kerberos, usually represented by a username or a service account.
The error message “1765328377 server not found in Kerberos database” is an error code that corresponds to the “krb5kdc_err_s_principal_unknown” error. The error code helps identify the specific error and assists in troubleshooting the issue.
Causes of the Error:
There can be several reasons why the “krb5kdc_err_s_principal_unknown” error occurs:
1. Incorrect Configuration: The server’s principal might not be properly configured in the Kerberos database. This can occur if the principal’s name is misspelled or if the server’s keytab file, which contains the encrypted keys for the principal, is not properly created or configured.
2. Expired or Invalid Credentials: If the server’s principal has expired or if the credentials are invalid, the KDC will not be able to authenticate the server, resulting in the error.
3. Server Renaming or Reconfiguration: If the server has been renamed or reconfigured, it is possible that the principal’s name or configuration no longer matches what is in the Kerberos database, leading to the error.
4. DNS Resolution Issues: The error can also occur due to DNS resolution problems. If the server’s hostname cannot be resolved to an IP address, the KDC will not be able to locate the server’s principal in the database.
Troubleshooting and Solutions:
To resolve the “krb5kdc_err_s_principal_unknown” error, follow these troubleshooting steps:
1. Verify Principal Configuration: Ensure that the server’s principal in the Kerberos database is correctly configured. Check for any misspellings or errors in the principal’s name, keytab file, or other relevant configurations.
2. Renew or Refresh Credentials: If the server’s principal has expired or has invalid credentials, renew or refresh the credentials using the appropriate utilities provided by your operating system or Kerberos implementation.
3. Update Server Configuration: If the server has been renamed or reconfigured, update the principal’s name and configuration in the Kerberos database to match the new server configuration.
4. Check DNS Resolution: Ensure that the server’s hostname can be resolved to the correct IP address. If there are any DNS issues, resolve them by checking DNS records, updating DNS settings, or configuring host files as necessary.
FAQs:
Q1. Can this error affect other services using Kerberos authentication?
Yes, the “krb5kdc_err_s_principal_unknown” error can affect any service that relies on Kerberos for authentication. If the server’s principal cannot be found in the Kerberos database, authentication will fail, and access to the service may be denied.
Q2. How can I determine if the error is due to an incorrect principal configuration or expired credentials?
You can examine the error logs generated by the KDC or the application utilizing Kerberos authentication to determine the exact cause of the error. These logs should indicate whether the principal is not found or if the credentials are expired or invalid.
Q3. What steps can I take to prevent the “krb5kdc_err_s_principal_unknown” error from occurring?
To prevent this error, make sure that server configurations and principals are properly set up and maintained. Regularly update and renew credentials, ensure correct DNS resolution, and monitor the logs for any potential issues or warning signs.
Q4. Are there any security risks associated with this error?
While the “krb5kdc_err_s_principal_unknown” error itself does not pose immediate security risks, it could indicate underlying issues with the Kerberos infrastructure that may compromise the overall security of the authentication system. It is essential to promptly address and resolve this error to maintain a secure network environment.
In conclusion, the “krb5kdc_err_s_principal_unknown” error can cause authentication failures and disrupt normal operations in a Kerberos-based system. By understanding its causes and following the troubleshooting steps outlined in this article, you can effectively resolve the error and ensure a secure and reliable authentication framework.
Kvno: Server Not Found In Kerberos Database While Getting Credentials For
Kerberos is a widely used authentication protocol in computer networks, which provides secure authentication services by using encryption and keys. One common issue that users may encounter when using Kerberos is the “KVNO: Server not found in Kerberos database while getting credentials for KDC” error message. In this article, we will explore the causes of this error and provide solutions to fix it.
What does “KVNO: Server not found in Kerberos database while getting credentials for KDC” mean?
KVNO stands for Key Version Number, which is a unique identifier assigned to each key in the Kerberos database. When a client requests a service ticket, it contacts the Key Distribution Center (KDC) to authenticate and obtain a ticket-granting ticket (TGT). The KDC then verifies the client’s credentials and looks up the requested server in its Kerberos database.
The error message “KVNO: Server not found in Kerberos database while getting credentials for KDC” indicates that the requested server’s principal key is not found or does not exist in the Kerberos database. This issue prevents the client from obtaining a service ticket for the requested server, causing authentication failures.
Causes of the “KVNO: Server not found in Kerberos database while getting credentials for KDC” error:
1. Inconsistent or missing server principal entry: Each server in a Kerberos realm must have a corresponding principal entry in the KDC’s database. If the server’s principal is missing or does not match the client’s request, the KDC will be unable to find the server’s key and return the aforementioned error.
2. Incorrect server hostname or realm: The error may also occur if the client specifies an incorrect server hostname or realm when requesting a service ticket. The KDC relies on the provided information to locate the server’s principal entry, and any mismatch will result in the “server not found” error.
3. Network or DNS issues: Connectivity problems or misconfigurations in the network infrastructure may lead to the inability of the client to reach the KDC. If the client cannot establish a connection to the KDC or resolve the server’s hostname, the error will occur.
Solutions to fix the “KVNO: Server not found in Kerberos database while getting credentials for KDC” error:
1. Check and create server principal entry: Ensure that the server’s principal entry exists and matches the request. Verify the server hostname, realm, and principal name. If the entry is missing, create it using the Kerberos administration tools, such as kadmin or kadmin.local.
2. Verify client request parameters: Double-check the client’s request parameters, such as the server hostname, realm, and principal name. Ensure that they align with the server’s actual configuration and are correctly specified in the request. Make any necessary corrections to match the server’s details.
3. Check network connectivity and DNS resolution: Ensure that the client can reach the KDC and resolve the server’s hostname. Verify the network connection between the client and the KDC. Check DNS settings and confirm that the server’s hostname is correctly registered and resolvable from the client’s perspective. Troubleshoot any network or DNS issues encountered.
4. Restart Kerberos services: Restarting the Kerberos KDC and related services may resolve temporary issues or inconsistencies. Restart the KDC and any dependent services to ensure a clean state and potential recovery from transient errors.
5. Verify Keytab file: If the server’s keytab file is corrupted or contains incorrect entries, it can cause the “server not found” error. Verify the keytab file’s integrity and contents, ensuring it contains the correct server principal information. Recreate the keytab file if necessary, following the Kerberos documentation for your specific server implementation.
6. Seek assistance from system administrators: If the error persists despite following the above steps, it may be beneficial to involve system administrators or support personnel with expertise in Kerberos authentication. They can investigate the issue further, potentially involving advanced troubleshooting techniques and analyzing Kerberos-specific logs for deeper insights.
FAQs about “KVNO: Server not found in Kerberos database while getting credentials for KDC”:
Q: Can this error occur if the server’s key version in the Kerberos database is outdated?
A: No, this error specifically indicates that the server principal entry is not found in the Kerberos database, rather than referring to key version issues.
Q: Does this error occur only with specific Kerberos implementations?
A: No, this error can occur with any Kerberos implementation that adheres to the protocol standards. However, some implementations may have additional troubleshooting tools or commands that can aid in resolving the issue.
Q: Can I fix this error by modifying the client’s configuration file manually?
A: Modifying the client’s configuration file may help in correcting misconfigured parameters or realms. However, it is essential to double-check the changes made to ensure they align with the server’s actual configuration.
Q: Can a client still authenticate with other servers even if this error occurs for a specific server?
A: Yes, while this error prevents obtaining a service ticket for the specific server that triggered it, the client can still authenticate with other servers if their principal entries are correct and reachable.
In conclusion, the “KVNO: Server not found in Kerberos database while getting credentials for KDC” error occurs when the server’s principal entry cannot be located in the Kerberos database. This error can be addressed by verifying the server’s principal entry, checking client request parameters, ensuring network connectivity and DNS resolution, restarting Kerberos services, verifying the keytab file, and seeking expert assistance when needed.
Images related to the topic server not found in kerberos database

Found 50 images related to server not found in kerberos database theme









Article link: server not found in kerberos database.
Learn more about the topic server not found in kerberos database.
- Server Not Found in Kerberos Database: The Complete Guide
- Server Not Found in Kerberos database – active directory
- Cannot get Kerberos service ticket: KrbException: Server not …
- Server Not Found in Kerberos Database: 4 Ways to Fix It
- Kerberos SSO : Server not found in Kerberos database (-1765328377)
- Failure in kerberos_kinit_password: Client not found in Kerberos database
- Configuring Kerberos Authentication Protocol – DataSunrise
- 4.11. Getting Started with Kerberos – Linux Security Cookbook [Book]
- Solved: Getting “Server not found in Kerberos database” wh…
- Getting error “Server not found in Kerberos database” when …
- Servers Not Found in Kerberos Database – VMware Docs
- SSSD – Server not found in Kerberos database – Not ThinLinc
- Server Not Found In Kerberos Database Redhat
- Server not found in Kerberos database (4283729)
See more: nhanvietluanvan.com/luat-hoc