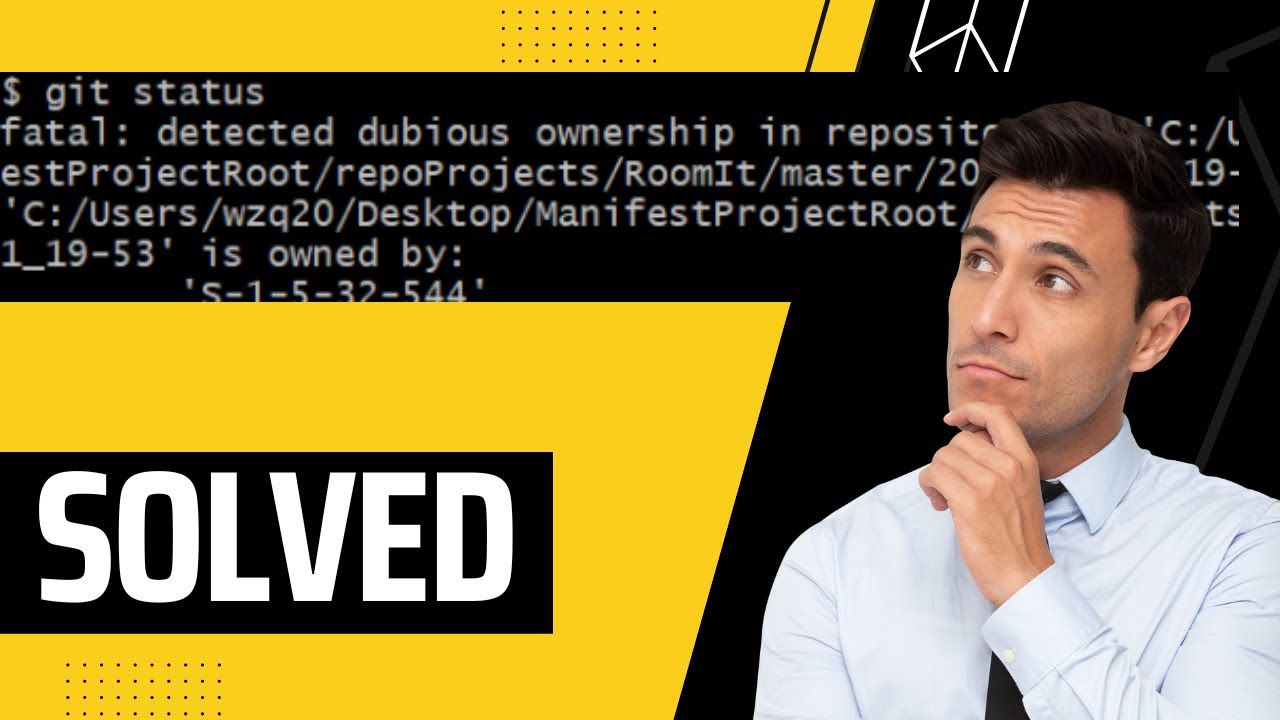
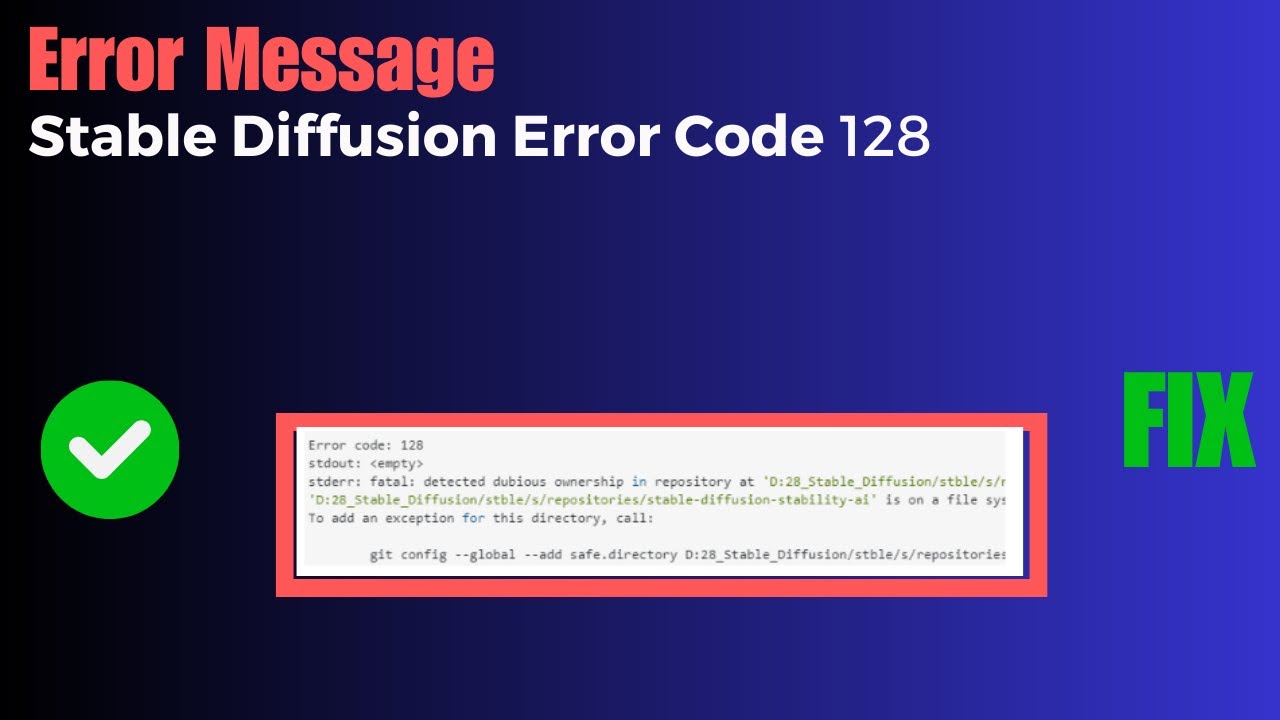
Fatal Detected Dubious Ownership In Repository At
I. Introduction
A. Definition of “fatal detected dubious ownership in repository”
The term “fatal detected dubious ownership in repository” refers to the identification and acknowledgement of ownership issues within a repository. These issues typically involve unauthorized contributors or maintainers, unresolved ownership conflicts, and cases of maintainers hijacking or stealing ownership of the repository. Detecting such ownership problems is crucial for the overall integrity and trustworthiness of the repository.
B. Explanation of the importance of detecting ownership issues in repositories
Detecting ownership issues in repositories is essential for maintaining a reliable and transparent development environment. Ownership problems can lead to various complications, including compromised credibility, misuse of resources, legal implications, and hindrance in collaborative workflows. By promptly addressing and resolving these issues, repositories can uphold their integrity and ensure the smooth functioning of software development projects.
II. Common Ownership Issues in Repositories
A. Identifying unauthorized contributors or maintainers
One common ownership issue involves unauthorized contributors or maintainers having access to the repository. This unauthorized access can lead to several risks, such as malicious code injection, unauthorized modifications, or compromise of sensitive data. Detecting and removing these unauthorized individuals is vital to prevent potential harm to the repository and its associated resources.
B. Unresolved ownership conflicts among contributors
Ownership conflicts can arise when multiple contributors believe they have rights or authority over a particular repository. These conflicts can cause delays, disputes, and disruptions in the development process. Resolving ownership conflicts requires clear communication, defined guidelines, and fair decision-making processes to avoid further complications and ensure the smooth progression of the project.
C. Maintainer hijacking or stealing ownership of the repository
In some cases, maintainers may attempt to hijack or steal ownership of a repository. This unethical behavior can disrupt collaboration, jeopardize the integrity of the project, and undermine the trustworthiness of the repository. Detecting and addressing such attempts is crucial to protect the rights of genuine contributors and maintain a secure development environment.
III. Risks and Consequences of Dubious Repository Ownership
A. Impact on the credibility and trustworthiness of the repository
When ownership issues in a repository go undetected or unresolved, it can significantly impact the credibility and trustworthiness of the project. Users and contributors may hesitate to rely on or collaborate with a repository that has questionable ownership, diminishing the repository’s overall value and reputation.
B. Potential misuse or abuse of repository resources by dubious owners
Dubious owners of a repository can exploit their position to misuse or abuse resources, such as injecting malicious code, tampering with critical files, or manipulating access controls. These actions can compromise the security and functionality of the repository, leading to significant consequences for both the project and the users.
C. Legal implications and challenges in resolving ownership disputes
Ownership disputes can escalate into legal battles, which can be time-consuming, costly, and detrimental to the progress of the project. Legal implications arising from dubious repository ownership issues can include intellectual property disputes, breach of contract allegations, or violations of licensing agreements. Promptly addressing ownership disputes through clear guidelines and effective communication can help mitigate legal challenges.
IV. Detecting Fatal Dubious Ownership
A. Utilizing version control systems to track ownership changes
Version control systems, such as Git, provide a comprehensive audit trail of ownership changes within a repository. By leveraging the functionalities of these systems, repositories can track and analyze ownership modifications, identify inconsistencies, and detect any unauthorized changes.
B. Analyzing commit history and contributor patterns for suspicious activity
Analyzing commit history and contributor patterns can help identify suspicious activities that may indicate dubious ownership. Anomalies in commit patterns or sudden changes in contributors’ behavior can trigger further investigation to ensure the repository’s ownership remains legitimate.
C. Monitoring access controls and permissions to prevent unauthorized changes
Strict monitoring of access controls and permissions is crucial to prevent unauthorized changes in a repository. Regularly reviewing and adjusting access privileges for contributors ensures that only trusted individuals can make modifications, minimizing the risk of dubious ownership issues.
V. Steps to Address Dubious Ownership Issues
A. Establishing clear ownership guidelines and policies for repositories
To address dubious ownership issues, repositories should establish clear ownership guidelines and policies. These guidelines should outline the rights and responsibilities of contributors, and provide a framework for resolving ownership disputes. By having well-defined guidelines, repositories can prevent ownership conflicts and navigate potential issues more effectively.
B. Conducting audits and reviews to identify and rectify ownership problems
Regular audits and reviews of a repository’s ownership structure can help identify and rectify ownership problems promptly. These audits should include comprehensive assessments of ownership metadata, such as contributor lists, commit logs, and permissions. Identifying and rectifying ownership problems in a timely manner maintains the repository’s integrity and trustworthiness.
C. Communicating with contributors to resolve ownership conflicts and concerns
Open communication with contributors is essential in resolving ownership conflicts and addressing any concerns related to dubious ownership. By fostering constructive dialogue and providing a platform for contributors to voice their opinions, repositories can facilitate the resolution of ownership disputes and maintain a harmonious development environment.
VI. Preventive Measures and Best Practices
A. Implementing strong authentication mechanisms to prevent unauthorized access
Preventing unauthorized access is a crucial measure to address dubious ownership issues. Implementing strong authentication mechanisms, such as two-factor authentication, ensures that only authorized individuals can access and make changes to the repository.
B. Regularly reviewing and updating ownership information for repositories
Repositories should regularly review and update ownership information to keep it accurate and up to date. Any changes in contributor roles and responsibilities should be promptly reflected in the ownership information to maintain transparency and avoid ownership disputes.
C. Encouraging collaboration and open communication among contributors
Promoting a culture of collaboration and open communication among contributors is vital in preventing ownership issues. By encouraging active participation, fostering trust, and providing opportunities for contributors to share their expertise, repositories can minimize the chances of ownership conflicts arising in the first place.
VII. Conclusion
A. Recap of the significance of detecting and addressing dubious ownership issues
Detecting and addressing dubious ownership issues is essential for maintaining the credibility, trustworthiness, and integrity of repositories. Ownership problems can have wide-ranging consequences, from compromised security to legal implications, and hinder the progress of software development projects. By implementing proper detection methods and establishing clear ownership guidelines, repositories can mitigate these risks and ensure a reliable and transparent development environment.
B. Emphasis on the continuous monitoring and improvement of repository ownership practices
Continuous monitoring and improvement of repository ownership practices are crucial to preventing and addressing ownership issues effectively. By staying vigilant and regularly reviewing ownership information, repositories can proactively identify and resolve ownership problems, fostering a trusted and collaborative software development community.
FAQs
1. What is “Detected dubious ownership in repository”?
“Detected dubious ownership in repository” refers to the identification of ownership issues within a repository, including unauthorized contributors or maintainers, ownership conflicts, and attempts to hijack or steal the repository’s ownership. It signifies the need to address these problems to maintain the integrity and trustworthiness of the repository.
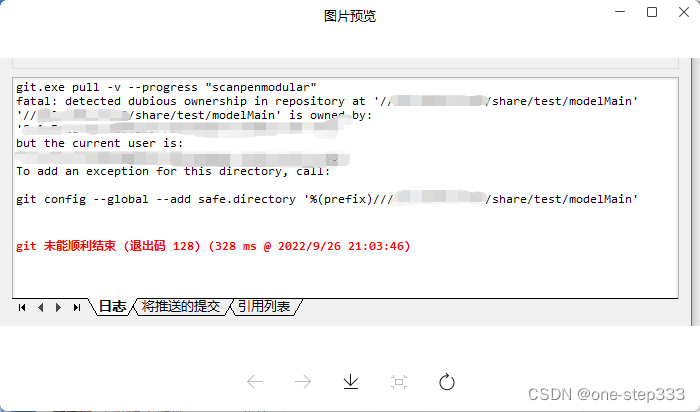
2. What does “Permission denied (publickey fatal Could not read from remote repository)” mean?
“Permission denied (publickey fatal Could not read from remote repository)” is an error message that commonly occurs when there is an issue with authentication or authorization when trying to access a remote repository. It indicates that the user does not have the necessary permissions or credentials to read from the remote repository.
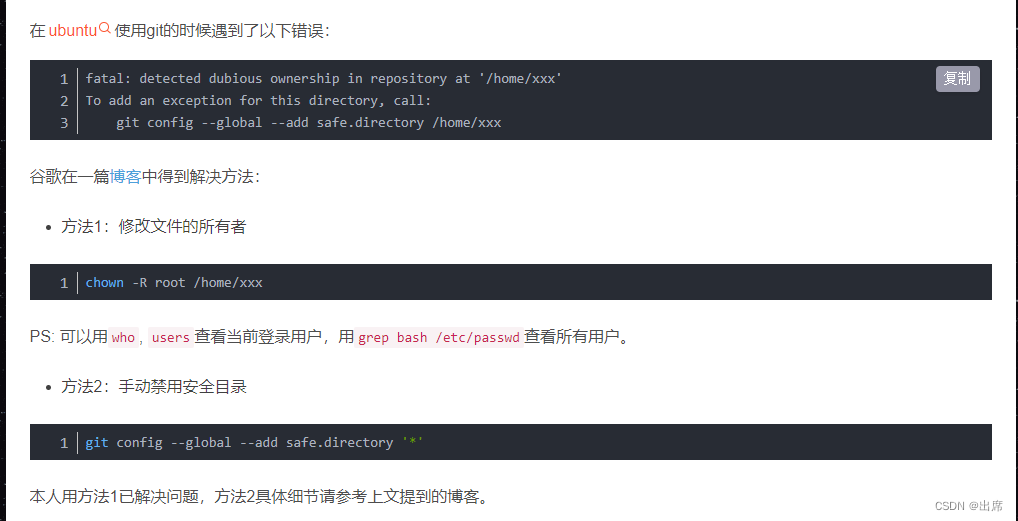
3. What does “Is owned by but the current user is git” mean?
“Is owned by but the current user is git” often appears as an error message when there is a mismatch between the repository’s owner and the current user trying to perform actions on the repository. It suggests that the repository is owned by another user, and the current user does not have the necessary privileges to make changes.
4. What does “error: remote origin already exists” mean?
“error: remote origin already exists” typically occurs when trying to add a remote repository in Git, but the remote origin already exists. It suggests that the repository has already been linked to a remote repository, and attempting to add it again results in an error.
5. How can I delete a remote repository in Git?
To delete a remote repository in Git, you can use the command “git remote rm
6. What should I do if I see the error “Failed to push to the remote repository, see the output window for more details”?
If you encounter the error “Failed to push to the remote repository, see the output window for more details,” it is advisable to check the output window for more specific error messages or information on why the push failed. This additional output can help identify the issue and guide you in resolving it.
7. How do I add a directory and its contents recursively in Git?
To add a directory and its contents recursively in Git, you can use the command “git add
8. How can I see the Git configuration settings?
To view the Git configuration settings, you can use the command “git config –list.” This command lists all the configuration settings currently in effect for your Git installation, including user details, aliases, and other customizations.
Git Fatal: Detected Dubious Ownership In Repository
Keywords searched by users: fatal detected dubious ownership in repository at Detected dubious ownership in repository, Permission denied (publickey fatal Could not read from remote repository), Is owned by but the current user is git, error: remote origin already exists., Git delete remote repository, Failed to push to the remote repository see the output window for more details, Git add safe directory recursively, Git config –list
Categories: Top 99 Fatal Detected Dubious Ownership In Repository At
See more here: nhanvietluanvan.com
Detected Dubious Ownership In Repository
Introduction (approximately 100 words):
In the world of software development, collaboration and sharing of code repositories are essential for fostering innovation and efficiency. However, recent instances have highlighted a concerning issue: detected dubious ownership in repositories. This alarming trend calls for careful examination and implementation of measures to safeguard the integrity and security of our codebase. This article aims to delve into this topic, shedding light on the risks associated with dubious ownership, exploring the potential motivations behind such actions, and providing actionable solutions to mitigate the threats.
I. Understanding Dubious Ownership in Repositories (approximately 200 words):
Dubious ownership in software repositories refers to instances where malicious individuals gain unauthorized access or control over repositories, either by hacking or exploiting weak security measures. This unauthorized acquisition grants them the power to modify, add, or delete code, often leading to severe consequences such as introducing vulnerabilities, injecting malware, or propagating unauthorized changes within the development ecosystem.
II. Risks Associated with Dubious Ownership (approximately 300 words):
1. Compromised Security: Dubious ownership enables attackers to infiltrate repositories, compromising the confidentiality, integrity, and availability of the code base. This can expose sensitive data, intellectual property, or even the entire development environment to unauthorized entities.
2. Breach of Trust: Dubious ownership undermines the trust among collaborators who rely on shared repositories. Illegitimate changes made to the code can shatter the trust built over time, leading to delays, confusion, and disputes within a project.
3. Legal Implications: Unlawful access to repositories can lead to serious legal consequences, including copyright infringement, theft of intellectual property, and violation of licensing agreements. These legal complications can have far-reaching financial and reputational repercussions for individuals and organizations involved.
4. Reputational Damage: Once a repository with dubious ownership is discovered, the reputation of the project, its developers, and contributors can suffer. Stakeholders may question the reliability of the project and its code quality, potentially leading to loss of credibility and diminished prospects for future collaborations.
III. Motivations Behind Dubious Ownership (approximately 200 words):
Understanding the motives behind dubious ownership can help in devising effective prevention strategies. Some common motivations may include:
1. Financial Gain: Malicious actors may aim to capitalize on proprietary code, steal valuable intellectual property, or even hold codebases for ransom.
2. Espionage: Competitors or adversaries may infiltrate repositories to gain access to sensitive information, strategies, or vulnerabilities, ultimately aiming to harm the targeted organization or software project.
3. Hacking Challenge: For some individuals, hacking into repositories is seen as a personal challenge or a demonstration of skill. These attackers may be driven solely by the thrill or recognition rather than any tangible gain.
IV. Preventive Measures and Best Practices (approximately 300 words):
To counter detected dubious ownership in repositories, a proactive approach with robust security measures and best practices is vital. Here are some recommended preventive measures:
1. Strong Authentication: Implement multi-factor authentication for repository access, ensuring that only authorized individuals can make changes, reducing the chances of unauthorized ownership.
2. Regular Auditing: Conduct periodic codebase audits to detect any suspicious activities, unauthorized changes, or unexpected ownership. Implementing automated tools to scan for unusual patterns or unknown contributors can help identify potential risks.
3. Access Control: Adopt granular access control mechanisms that grant permissions based on roles and responsibilities. Limit the number of users with repository administration rights, reducing the potential attack surface area.
4. Secure Development Practices: Educate and enforce secure coding practices within the development team. Encourage adherence to coding standards, review processes, and vulnerability assessments to minimize the risks of introducing vulnerabilities into the repository.
5. Continuous Security Monitoring: Implement centralized monitoring systems to detect any unauthorized access attempts or potential vulnerabilities. This enables prompt response and mitigation to mitigate the damage caused by detected dubious ownership.
FAQs (approximately 120 words):
1. What should I do if I suspect dubious ownership in a repository?
If you detect any signs or simply suspect dubious ownership, notify the repository’s owner or project administrators immediately. They can initiate an investigation, verify access logs, and take necessary steps to secure the repository and minimize potential damage.
2. Can open-source projects be targeted by dubious ownership?
Indeed, open-source projects are not immune to dubious ownership. In fact, they can be more vulnerable due to their collaborative nature. It is crucial for open-source communities to implement secure practices, governance models, and community-wide awareness to mitigate such risks.
3. How often should codebase audits be conducted?
The frequency of codebase audits may vary depending on the project’s size, complexity, and security requirements. However, a best practice is to conduct regular codebase audits at least once a quarter or whenever major changes occur within the project.
4. Are there any secure alternatives to popular repositories to mitigate risk?
Several secure repository hosting platforms exist that offer enhanced security features and measures. It is advisable to research and consider these alternatives, assessing their security protocols before migrating or hosting sensitive projects.
Conclusion (approximately 100 words):
Addressing detected dubious ownership in repositories is of paramount importance to protect codebases, developers’ trust, and project sustainability. Awareness of the risks, motivations, and preventive measures discussed in this article can empower software developers and organizations to strengthen their security posture, detect potential threats early, and respond swiftly to mitigate any damage or compromises. Together, the software development community can build a safer and more reliable environment for innovation and collaboration.
Permission Denied (Publickey Fatal Could Not Read From Remote Repository)
Introduction:
When using version control systems like Git, it is common to encounter errors that may hamper your ability to communicate with remote repositories. One such error is the “Permission denied (publickey, fatal: Could not read from remote repository)” message. In this article, we will dive deep into this error, discussing its potential causes, understanding its implications, and providing troubleshooting steps to resolve it.
Understanding the Error Message:
The error message “Permission denied (publickey, fatal: Could not read from remote repository)” is a common issue encountered while trying to connect and authenticate with a remote repository. This error specifically arises when your SSH key or the associated public key is not authorized to access the remote repository.
Implications of the Error:
This error prevents the user from performing any Git operations that require interaction with a remote repository. Without resolving this issue, you will be unable to fetch, pull, push, or clone repositories housed on platforms like GitHub, GitLab, or Bitbucket.
Possible Causes of the Error:
1. Authentication Issues: The most common cause of this error is a problem with your authentication credentials. This includes either an incorrect or missing SSH key.
2. Incorrect Repository URL: The error may also occur if the repository URL you are using is incorrect or inaccessible.
3. Repository Access Restrictions: Some repositories require proper access rights to perform certain operations. If your SSH key is not granted the necessary privileges, the error may occur.
4. SSH Agent Issues: Issues with the SSH agent running on your system can also lead to the permission denied error.
Troubleshooting Steps:
Here are some step-by-step solutions to troubleshoot and address the “Permission denied (publickey, fatal: Could not read from remote repository)” error:
1. Verify SSH Key: Ensure that your SSH key is correctly added to your SSH agent. Check if the key is available in the proper directory (~/.ssh/) and the correct permissions are set (600 or 400).
2. Generate and Add a New SSH Key: If you don’t have an SSH key, or the existing one is invalid, generate a new one. You can use the command “ssh-keygen” for this purpose. Then, add the new key to your SSH agent and the remote repository account settings.
3. Confirm Correct Remote URL: Check if the remote URL you are using is correct. Copy it directly from the repository and ensure there are no typos or unnecessary characters.
4. Grant Proper Access Rights: Confirm that your SSH key has the required permissions to access the repository. Consult the repository settings or contact the repository owner to verify or grant access.
5. Test SSH Connection: Determine if you can establish a connection with the remote repository’s SSH server using the following command: “ssh -T git@
6. Check SSH Agent Configuration: Ensure your SSH agent is running and properly configured. If not, restart the agent or refer to the documentation of your operating system to troubleshoot SSH agent issues.
Frequently Asked Questions (FAQs):
Q1: What is an SSH key?
A1: An SSH key, also known as a public-private key pair, is a cryptographic security feature used for authentication and secure communication between your local system and the remote repository server.
Q2: How can I determine if my SSH key is correctly added to the SSH agent?
A2: You can run the command “ssh-add -l” to list all the keys currently added to the SSH agent. If your key appears in the list, it indicates that it is correctly added.
Q3: Can the “Permission denied” error occur due to an internet connection issue?
A3: No, this error is unrelated to your internet connection, as it indicates an authentication problem between your system and the remote repository server.
Q4: If I regenerate my SSH key, will it affect my existing repositories?
A4: Regenerating your SSH key will not directly impact your existing repositories. However, you will need to replace the old key with the new one in the remote repository settings and any other systems where you use the old key.
Conclusion:
The “Permission denied (publickey, fatal: Could not read from remote repository)” error can hinder your ability to interact with remote repositories through Git. By understanding the causes and following the troubleshooting steps provided in this article, you should be able to resolve the issue and continue your collaboration seamlessly. Remember to double-check your SSH key and ensure it has appropriate access rights to the repositories.
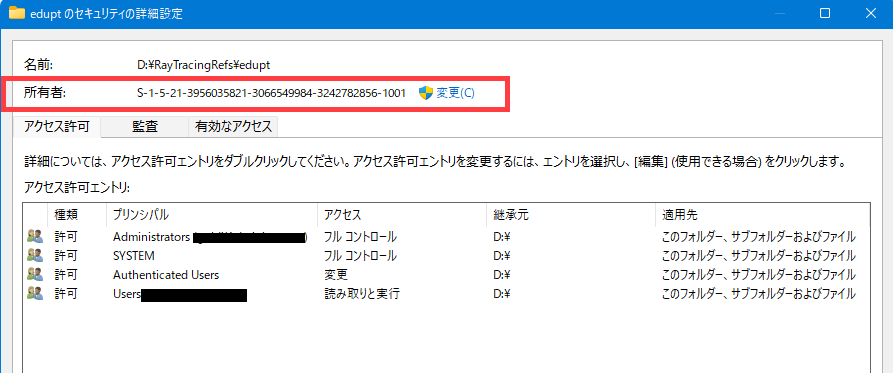
Is Owned By But The Current User Is Git
When working with version control systems, such as Git, you may come across the phrase “is owned by, but the current user is Git.” This message can appear when attempting to perform certain actions on a file or repository. In this article, we will explore the meaning behind this message, the reasons for encountering it, and how to address it properly.
Understanding Ownership in Version Control Systems
Ownership in version control systems refers to the user or account that has primary control over a particular file or repository. This ownership often determines the permissions and actions that can be performed on the file. In the context of Git, ownership can be associated with either a specific user or the system account named “Git.”
When a file or repository is owned by a user, that individual has full control over it. They can modify, delete, or grant access to others as they see fit. On the other hand, when a file or repository’s ownership is assigned to “Git,” it means that Git has control over it, typically as a part of the version control process.
Reasons for Encountering “Is Owned By, But the Current User is Git”
Encountering the message “is owned by, but the current user is Git” can happen for various reasons. Here are a few common scenarios:
1. Permission Issues: The message could occur if the executing user or the executing process does not have sufficient permissions to perform the requested operation on the file or repository. This might happen when attempting to modify, delete, or access a file that requires higher privileges than the current user or process possesses.
2. Conflicting Git Operations: Git performs some actions under the “Git” user account to maintain the integrity of the version control system. While these operations are usually transparent to users, conflicts between multiple actions can occur if, for example, a user’s operation is in progress while Git performs its own operation on the same file or repository.
3. Repository Corruption: In rare cases, the “is owned by, but the current user is Git” message can be a symptom of a corrupted repository. Corruption can occur due to hardware issues, software bugs, or manual interventions that inadvertently affect the repository’s integrity.
Addressing the Issue
Now that we understand the potential reasons for encountering the message, let’s delve into resolving this common problem. Here are a few troubleshooting steps to help you address the issue:
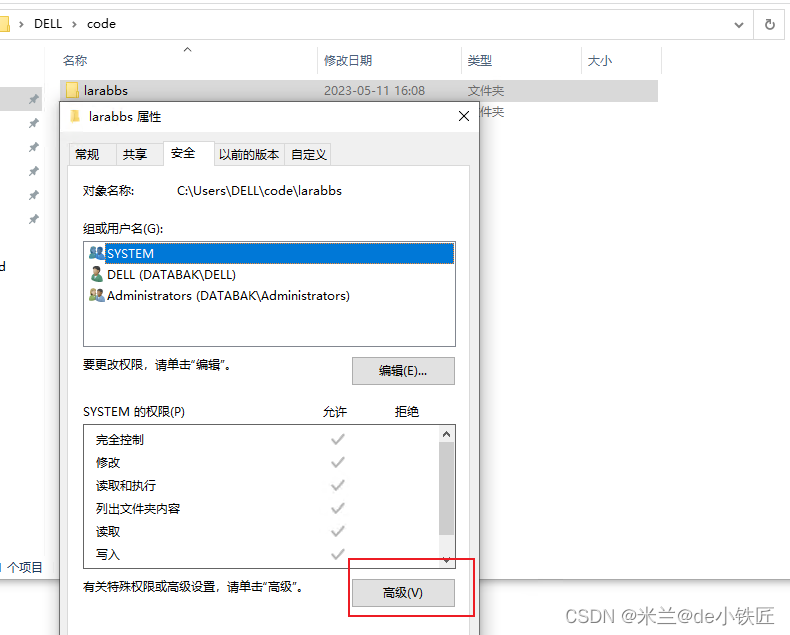
1. Check Permissions: Verify that you have the necessary permissions to perform the action on the file or repository. If not, consult the owner or administrator to grant you the required access rights.
2. Retry the Action: In some cases, the message may appear temporarily due to concurrent actions. Simply retrying the operation after a few moments might resolve the issue, as Git completes its own processes.
3. Review Concurrent Git Operations: If the action involves Git, it is possible that a concurrent Git operation is conflicting with your action. Wait for any ongoing Git processes to complete before retrying the intended action.
4. Clean Repository Cache: Git relies on a local repository cache to improve performance. Corrupted or inconsistent cache data can lead to issues. Cleaning the repository cache using the `git clean` command, followed by a fresh clone or update, can help resolve the problem.
5. Repository Restoration: In situations where corruption is suspected, it might be necessary to restore the repository from a backup or a previous stable state. This process involves replacing the existing repository with a known working copy.
Frequently Asked Questions
Q: Can this issue occur in other version control systems?
A: While the exact error message may differ, similar issues can occur in other version control systems when there are conflicts related to file ownership or insufficient permissions.
Q: Why does Git perform actions under its own user account?
A: Git needs to maintain the integrity of the repository and perform certain operations outside the scope of individual users. By utilizing its own user account, it ensures these actions are isolated and consistent.
Q: What if the issue persists even after trying the suggested solutions?
A: If the problem persists, it could indicate a more complex issue. Seeking assistance from technical support or consulting online forums specialized in Git-related problems may help to diagnose and resolve the issue.
Q: How can I prevent encountering this error in the future?
A: Ensuring proper permissions and regularly maintaining your Git repositories can minimize the chances of encountering this error. Implementing best practices, such as assigning appropriate permissions and regularly backing up repositories, can also reduce the likelihood of encountering ownership-related issues.
In conclusion, encountering the message “is owned by, but the current user is Git” can be attributed to permission conflicts, concurrent Git operations, or repository corruption. Resolving the issue typically involves checking permissions, retrying actions, managing concurrent operations, cleaning the repository cache, or performing a restore. By following the troubleshooting steps outlined in this article, you should be able to address and mitigate this common Git issue effectively.
Images related to the topic fatal detected dubious ownership in repository at

Found 25 images related to fatal detected dubious ownership in repository at theme

![Git] fatal: detected dubious ownership in repository at is owned by Git] Fatal: Detected Dubious Ownership In Repository At Is Owned By](https://blog.kakaocdn.net/dn/DC86k/btr2FgluLj8/fIDIhCecLkxQNwn5ziKFdK/img.png)
















Article link: fatal detected dubious ownership in repository at.
Learn more about the topic fatal detected dubious ownership in repository at.
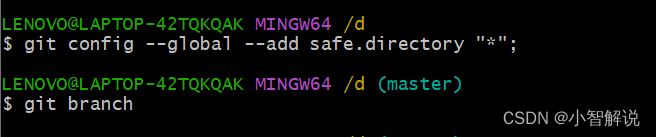
- git submodule update failed with ‘fatal: detected dubious …
- Git detect dubious ownership in repository | by Dennis – Medium
- Git “fatal: detected dubious ownership in repository”
- Little Git Tricks: Fix a Dubious Ownership of a Repository
- Detected dubious ownership in repository with Jenkins upgrade
See more: nhanvietluanvan.com/luat-hoc