Botocore.Exceptions.Nocredentialserror: Unable To Locate Credentials
Introduction
The botocore.exceptions.nocredentialserror is an error that occurs when attempting to run AWS services without proper credentials. This error indicates that the system is unable to locate the necessary credentials to authenticate and authorize access to AWS services. In this article, we will explore the symptoms, causes, common scenarios, affected AWS services, solutions, troubleshooting steps, preventive measures, and additional resources related to this error.
Symptoms of botocore.exceptions.nocredentialserror
When encountering the botocore.exceptions.nocredentialserror, users may experience the following symptoms:
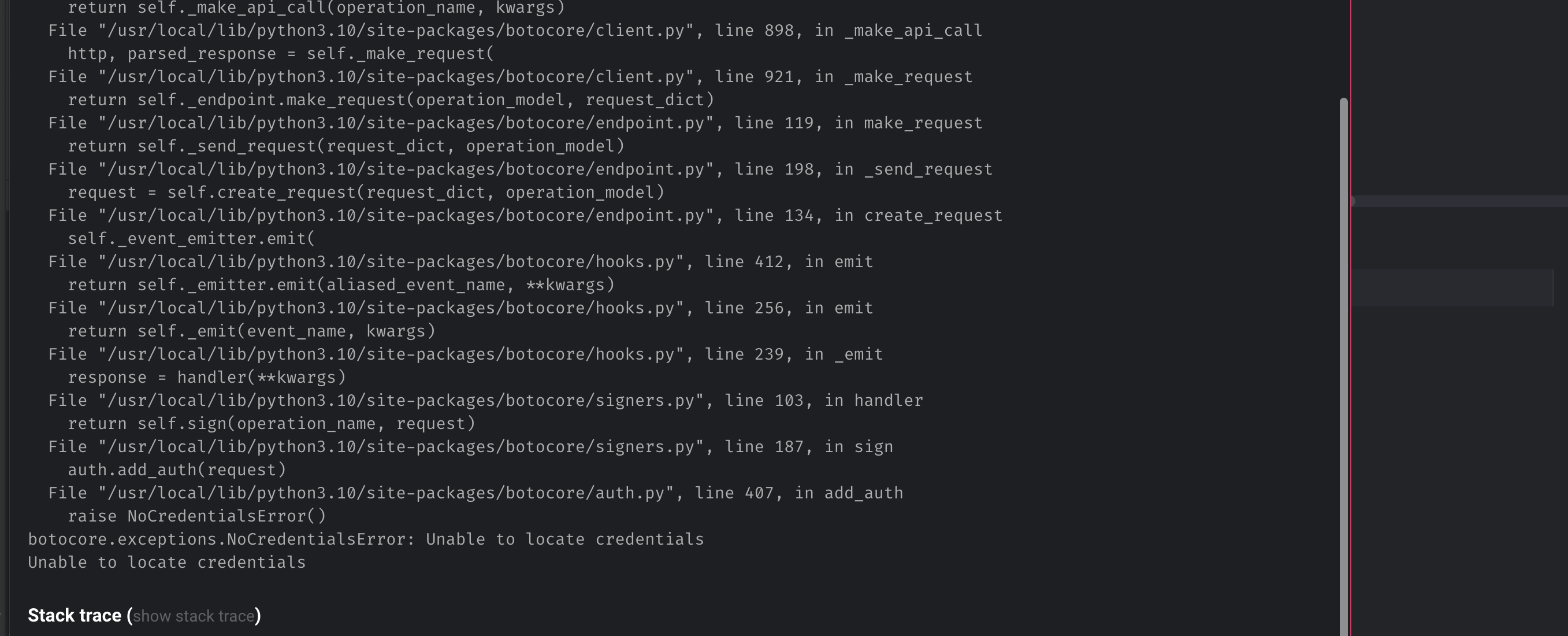
1. Error message: The primary symptom is the error message itself, which typically states “botocore.exceptions.nocredentialserror: Unable to locate credentials.” This error message clearly indicates that the system is unable to locate the required credentials.
2. Failed AWS service access: As a result of the missing or invalid credentials, users will be unable to access AWS services, such as EC2, S3, or DynamoDB.
3. Permission denial: Without valid credentials, AWS services will deny access, resulting in permission denial errors when attempting to execute specific AWS commands.
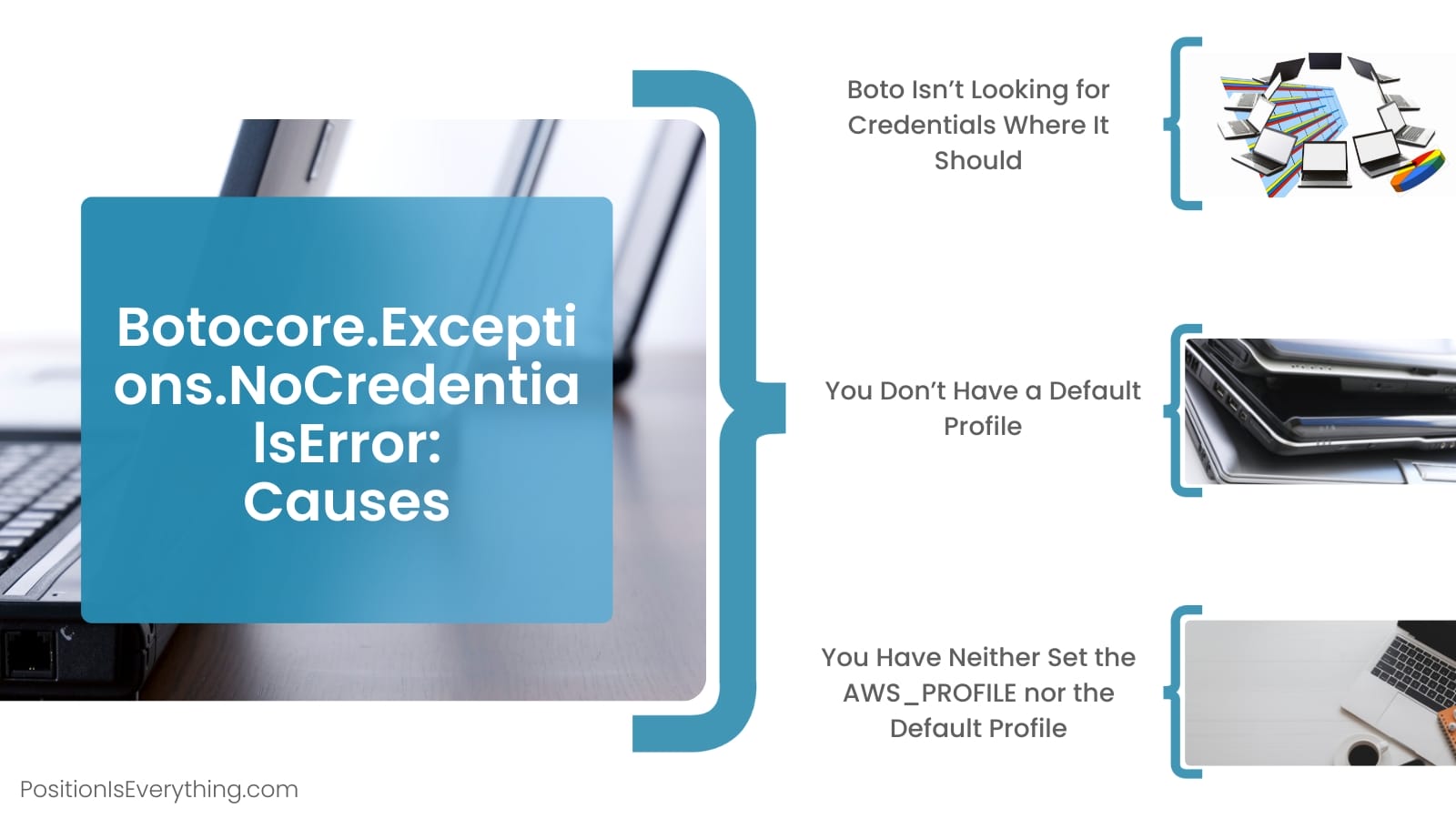
Causes of botocore.exceptions.nocredentialserror
The botocore.exceptions.nocredentialserror can occur due to various reasons, including:
1. Missing or invalid AWS credentials: One of the primary causes is the absence or misconfiguration of AWS credentials. These credentials include an Access Key and a Secret Access Key, which are required for authentication and authorization purposes.
2. Incorrect configuration file or profile: The configuration file used by AWS CLI or SDKs, such as boto3, may contain errors or incorrect profile settings, leading to the nocredentialserror.
3. Temporary token expiration: In some cases, if the temporary security token obtained via AWS Security Token Service (STS) has expired, the system may fail to locate valid credentials, resulting in the error.
Common Scenarios Leading to botocore.exceptions.nocredentialserror
There are several common scenarios that often lead to the botocore.exceptions.nocredentialserror, including:
1. Fresh AWS account setup: When setting up a new AWS account, users may forget to configure and provide the necessary credentials, resulting in the nocredentialserror when attempting to access AWS services.
2. Incorrect credential configuration: Users who manually configure their AWS credentials may make mistakes, such as typing incorrect characters or omitting essential information. These errors can lead to the inability of the system to locate the credentials.
3. Expired or revoked credentials: AWS credentials, including Access Key or Temporary Security Token, are subject to expiration or revocation. If the credentials have expired or been revoked, the system will fail to locate valid credentials, triggering the nocredentialserror.
AWS services affected by botocore.exceptions.nocredentialserror
The botocore.exceptions.nocredentialserror can impact various AWS services, some of which include:
1. Amazon S3 (Simple Storage Service): Users will be unable to perform operations such as listing buckets, uploading or downloading files, or managing S3 objects.
2. Amazon EC2 (Elastic Compute Cloud): The error will prevent users from launching, terminating, or managing EC2 instances.
3. Amazon DynamoDB: Access to DynamoDB resources, such as tables or queries, will be denied due to the missing credentials.
Solutions for Resolving botocore.exceptions.nocredentialserror
To resolve the botocore.exceptions.nocredentialserror, follow these solutions:
1. Install boto3 Python3: Ensure that you have installed the boto3 library for Python3, which is the AWS SDK for Python. This library is necessary for accessing AWS services programmatically.
2. Configure AWS credentials: Use the AWS CLI or run “aws configure” command to configure your AWS credentials, including the Access Key and Secret Access Key. Provide the required information accurately.
3. Check AWS configuration files: Verify the configuration files used by AWS CLI or SDKs, such as .aws/credentials and .aws/config. Ensure that these files are correctly formatted and contain the necessary profiles and settings.
4. Temporary token renewal: If you are using temporary security tokens obtained via AWS Security Token Service (STS), check if the token has expired. If it has, acquire a new token.
Troubleshooting Steps for botocore.exceptions.nocredentialserror
If you are still facing the botocore.exceptions.nocredentialserror, follow these troubleshooting steps:
1. Verify IAM user permissions: Ensure that the IAM user associated with the credentials has the necessary permissions to access the AWS services you are attempting to use. Check the IAM policies and permissions carefully.
2. Check AWS region settings: Confirm that you have specified the correct AWS region in your AWS configuration files or in your Python code. Incorrect region settings can cause credential-related errors.
3. Validate network connectivity: Make sure your system has an active internet connection and can communicate with the AWS services. Network issues can impact the retrieval of credentials or the execution of AWS commands.
Preventive Measures to Avoid botocore.exceptions.nocredentialserror
To prevent encountering botocore.exceptions.nocredentialserror in the future, consider implementing the following measures:
1. Regularly review and update credentials: Periodically review your AWS credentials, including Access Key, Secret Access Key, and temporary security tokens. Renew or update these credentials as needed to avoid any potential expiry or revocation issues.
2. Consistently configure credentials: Whenever setting up or configuring AWS credentials, double-check the input to ensure accuracy. Typos or missing characters can cause immediate or future credential-related errors.
3. Utilize AWS Identity and Access Management (IAM): Leverage IAM to create and manage user accounts with appropriate permissions. Assign IAM roles and policies to control access to AWS resources effectively.
4. Test AWS service access: Before relying on AWS services in production, perform thorough testing to verify that your credentials are correctly configured and can successfully access the desired AWS services.
Additional Resources for Further Information on botocore.exceptions.nocredentialserror
For further information on the botocore.exceptions.nocredentialserror and related topics, refer to the following resources:
1. AWS documentation: The official AWS documentation provides detailed information on AWS CLI, SDKs, and management of AWS credentials.
2. Boto3 documentation: Explore the Boto3 documentation for comprehensive guidance on using the AWS SDK for Python and resolving common issues.
3. AWS CLI User Guide: Refer to the AWS Command Line Interface User Guide for step-by-step instructions on configuring and managing AWS CLI credentials.
Conclusion
The botocore.exceptions.nocredentialserror is an error that occurs when the system is unable to locate the necessary credentials to authenticate and authorize access to AWS services. By following the solutions, troubleshooting steps, and preventive measures outlined in this article, users can effectively resolve and avoid this error, ensuring smooth access and utilization of AWS services.
How To Setup Boto3 And Aws Credentials On Windows 10 | Aws Command Line Configuration | Aws Cli
Why Is Python S3 Unable To Locate Credentials?
Python S3, a popular Python library used for working with Amazon S3 storage, offers a convenient way to interact with S3 buckets and objects. However, it can sometimes pose challenges when it comes to locating the necessary credentials for authentication. This article aims to delve into the reasons behind this issue and provides possible solutions to resolve it.
When using Python S3, it is essential to provide valid AWS credentials to ensure secure and authorized access to S3 resources. These credentials typically consist of an access key ID and a secret access key, which are generated in the AWS Management Console. However, even with valid credentials, S3 may still encounter difficulties locating them. Let’s explore some of the potential causes for this problem:
1. Incorrectly Configured Environment Variables:
One common reason for Python S3 being unable to locate credentials is the incorrect configuration of environment variables. Python S3 looks for credentials in the environment variables `AWS_ACCESS_KEY_ID` and `AWS_SECRET_ACCESS_KEY`. Ensure that these variables are correctly set, and that the values provided match the ones generated in the AWS Management Console.
2. Misconfigured AWS CLI or SDK:
If you are using AWS CLI (Command Line Interface) or an SDK (Software Development Kit) alongside Python S3, incorrect configurations within these tools can also lead to the inability to locate credentials. Verify that both AWS CLI and SDK are correctly set up and configured, and ensure that any profiles or configuration files contain accurate credential information.
3. Invalid Credential Path:
Python S3 provides the ability to define the location of the credential file explicitly. By default, it searches for credentials in the file located at `~/.aws/credentials` on Unix-based systems or `%UserProfile%\.aws\credentials` on Windows. If the credentials file is not present in the specified path or has been moved or renamed, Python S3 will fail to locate the credentials. Double-check the presence and location of the credentials file and adjust the path accordingly if necessary.
4. Temporary Credential Expiration:
AWS issues temporary credentials in scenarios where long-term access is not required. These temporary credentials have an expiration time, and if the time limit is exceeded, Python S3 may fail to find valid credentials. Examine the credential expiration time and ensure that you are using updated and valid credentials.
5. Insufficient IAM Role Permissions:
If you are using IAM (Identity and Access Management) roles to manage access to S3, it is crucial to verify that the associated IAM role has the necessary permissions. Insufficient permissions can prevent Python S3 from locating the credentials required to access S3 resources, resulting in authentication failures. Review and update the IAM role’s policies to ensure that it has the appropriate permissions for S3 access.
To overcome these challenges and enable Python S3 to locate credentials successfully, consider applying the following solutions:
1. Check Credential Configuration:
First, verify that the environment variables `AWS_ACCESS_KEY_ID` and `AWS_SECRET_ACCESS_KEY` are correctly set and match the generated credentials in the AWS Management Console. Use the `printenv` command (Unix-based systems) or `echo %AWS_ACCESS_KEY_ID% %AWS_SECRET_ACCESS_KEY%` command (Windows) to ensure the values are correctly assigned.
2. Verify AWS CLI and SDK Configuration:
Confirm that the AWS CLI and SDK are properly configured, paying attention to profiles and configuration files where credentials may be stored. Review the configuration files and ensure that they contain accurate credential information.
3. Adjust Credential Path:
If the credential file’s location has been changed or renamed, modify the Python S3 code to point to the correct file path explicitly. Alternatively, you can move the credentials file back to the default location for seamless authentication.
4. Refresh Expired Credentials:
If the credentials expire, generate new ones from the AWS Management Console and update the Python S3 code with the new access key ID and secret access key. Additionally, consider enabling long-term access options if the scenario allows.
5. Review IAM Role Permissions:
Examine the IAM role associated with the Python S3 authentication credentials and make sure it has the necessary permissions to access S3 resources. Update the IAM role’s policies accordingly if any permission gaps are identified.
FAQs:
Q: Can I use different credentials for different AWS accounts with Python S3?
A: Yes, Python S3 supports using different credentials for different AWS accounts by defining separate profiles in the AWS configuration files. Each profile can have its own access key ID and secret access key.
Q: Why does Python S3 use environment variables for authentication?
A: Python S3 uses environment variables for authentication to provide flexibility and security. The use of environment variables allows users to store and manage credentials outside of the code, reducing the risk of accidentally exposing sensitive information.
Q: How can I securely store AWS credentials for Python S3?
A: It is recommended to avoid hardcoding AWS credentials directly into the code. Instead, consider storing credentials in environment variables, AWS CLI profiles, or using other secure methods such as AWS Secrets Manager or environment-specific configuration files.
Q: What should I do if none of the suggested solutions work?
A: If you are still unable to resolve the issue, consider seeking support from the AWS community forums or contacting AWS support directly for specialized assistance in troubleshooting Python S3 credential issues.
In conclusion, Python S3 may encounter difficulties locating credentials due to various configuration and permissions issues. By correctly configuring environment variables, validating CLI and SDK configurations, adjusting the credential path, refreshing expired credentials, and reviewing IAM role permissions, users can overcome this challenge and ensure successful authentication with S3 resources using Python S3.
Why Is Download From S3 Unable To Locate Credentials?
Amazon S3 (Simple Storage Service) is a popular cloud storage service provided by Amazon Web Services (AWS). It offers a highly scalable, reliable, and cost-effective way to store and retrieve data. However, sometimes users may encounter an error message stating that their download from S3 is unable to locate credentials. In this article, we will explore the possible causes of this issue and discuss potential solutions.
1. Invalid or Expired Credentials: The most common reason for this error is invalid or expired credentials. When you access data from Amazon S3, you need to provide authentication credentials that grant you access to your resources. These credentials typically consist of an Access Key ID and a Secret Access Key. If either of these credentials is incorrect or has expired, you will encounter the “unable to locate credentials” error.
Solution: To resolve this issue, you need to ensure that you have valid and active credentials. Visit the IAM (Identity and Access Management) console in your AWS account and verify that the Access Key ID and Secret Access Key you are using are correct. If the credentials have expired, you can create new ones and update your application or tool with the new credentials.
2. Misconfigured AWS CLI Profile: Another common reason behind the “unable to locate credentials” error is a misconfigured AWS CLI (Command Line Interface) profile. The AWS CLI allows you to interact with AWS services via the command line. If you are using the AWS CLI to download from S3 and your profile is misconfigured or missing credentials, you will encounter this error.
Solution: Verify that your AWS CLI profile is correctly configured with the correct Access Key ID and Secret Access Key. You can use the “aws configure” command to set up your profile or update the existing one. Make sure that the default profile or the specified profile in your downloading command has valid credentials.
3. Instance Role Misconfiguration: When running your applications on an Amazon EC2 (Elastic Compute Cloud) instance, you can assign an IAM role to it. This role provides the necessary permissions to access other AWS services, such as S3. If the instance role attached to your EC2 instance lacks the required permissions for S3, you may encounter the “unable to locate credentials” error.
Solution: To resolve this issue, review and modify the permissions associated with the IAM role attached to your EC2 instance. Ensure that the necessary permissions, such as s3:GetObject, s3:ListBucket, or any other S3 operations required for your application, are granted to the role. Additionally, you may need to restart your EC2 instance or relaunch the application to apply the changes.
4. Network Connectivity Issues: At times, network connectivity problems can contribute to the “unable to locate credentials” error. If your application or tool is unable to establish a connection to AWS services due to firewall restrictions, network configuration issues, or proxy settings, the credentials cannot be validated, resulting in the error.
Solution: Troubleshoot your network connectivity settings and firewall configurations. Ensure that your application or tool has the required outbound network access to connect to the AWS services. Check if any proxy settings need to be configured to access external resources.
5. Regional Configuration Issues: Amazon S3 is available in different AWS regions worldwide. When you access S3, you need to specify the correct endpoint corresponding to the region where your S3 bucket resides. If you mistakenly use an endpoint for a different region or configure it incorrectly, you may experience the “unable to locate credentials” error.
Solution: Double-check the regional configuration of your application or tool. Make sure that the endpoint used to access S3 points to the correct AWS region where your bucket is located. Update your endpoint configurations if needed.
FAQs:
Q1. How can I locate my AWS credentials?
A1. You can find your AWS Access Key ID and Secret Access Key by logging into the AWS Management Console and navigating to the IAM service. In the IAM console, select “Users” and then click on your username. Under the “Security credentials” tab, you will find your credentials.
Q2. Can I use an existing IAM user’s credentials to download from S3?
A2. Yes, you can use the Access Key ID and Secret Access Key of an existing IAM user to download from S3. Ensure that the IAM user has the necessary permissions to access the S3 bucket.
Q3. Why do my credentials expire?
A3. For security reasons, AWS credentials have an expiration period. By default, Access Key IDs and Secret Access Keys are valid for 90 days. After this period, you will need to generate new credentials.
Q4. How can I set up an IAM role for EC2 instances?
A4. To set up an IAM role for EC2 instances, go to the IAM service in the AWS Management Console. Create a new IAM role or choose an existing one. Assign the required permissions for S3 access to the role. Finally, attach the role to your EC2 instance through the EC2 console.
Q5. What should I do if none of the above solutions resolve the issue?
A5. If you have tried all the recommended solutions and are still unable to locate credentials, consider reaching out to AWS Support for further assistance. Provide them with detailed information about your setup and the steps you have taken to troubleshoot the issue.
In conclusion, the “unable to locate credentials” error when downloading from S3 can be caused by various factors, including invalid or expired credentials, misconfigured profiles, instance role misconfigurations, network connectivity issues, or regional configuration problems. By following the suggested solutions and troubleshooting steps, users can resolve this error and resume their downloads from Amazon S3 seamlessly.
Keywords searched by users: botocore.exceptions.nocredentialserror: unable to locate credentials Install boto3 python3, AWS credentials, Unable to locate credentials you can configure credentials by running aws configure, Boto3, Boto3 exceptions, Generate_presigned_url boto3, S3boto, Setup credentials aws
Categories: Top 23 Botocore.Exceptions.Nocredentialserror: Unable To Locate Credentials
See more here: nhanvietluanvan.com
Install Boto3 Python3
Boto3 is the Amazon Web Services (AWS) Software Development Kit (SDK) for Python. It allows Python developers to create and manage AWS services, such as Amazon S3, Amazon EC2, and DynamoDB, among others, using Python code. In this article, we will explore how to install Boto3 for Python3 and provide a step-by-step guide to get you started. Additionally, we will address some frequently asked questions (FAQs) related to the installation process.
Before we dive into the installation process, it is important to note that Boto3 requires Python version 3.3 or higher. Thus, ensure you have the appropriate version installed on your system. If not, download and install the latest stable version of Python from the official Python website (https://www.python.org/downloads/) before proceeding.
Now, let’s proceed with the installation process:
Step 1: Check Python Version
Begin by confirming the Python version installed on your system. Open the terminal or command prompt and type the following command:
“`
python3 –version
“`
This command will display the Python version. If the version displayed is 3.3 or higher, you are good to go. Otherwise, follow the instructions given on the Python website to upgrade your Python installation.
Step 2: Install Boto3
To install Boto3, you need to use the Python package installer, pip, which is typically included with Python. Open your terminal or command prompt and run the following command to install Boto3:
“`
pip3 install boto3
“`
The pip3 command ensures that we are installing the package for Python3. If everything goes well, Boto3 should be successfully installed on your system.
Step 3: Verify the Installation
To verify if Boto3 has been installed correctly, you can use the following command:
“`
python3 -c “import boto3”
“`
If the installation was successful, this command will not produce any output. However, if an error is shown, it implies that Boto3 was not installed correctly, and you should revisit the installation steps.
Congratulations! You have successfully installed Boto3 for Python3. Now, let’s address some FAQs related to the installation process:
FAQs:
Q1: Can I install Boto3 using pip if I have both Python2 and Python3 installed on my system?
A1: Yes, you can install Boto3 for Python3 using pip3 while having both Python2 and Python3 on your system. The pip3 command ensures that the package is installed specifically for Python3.
Q2: Can I install Boto3 in a virtual environment?
A2: Absolutely! In fact, it is often recommended to install Boto3 within a virtual environment to keep your project dependencies separate. First, activate your virtual environment, and then run the pip3 install command mentioned earlier. Boto3 will be installed within that virtual environment only.
Q3: What if I encounter a permission denied error while using pip3 install?
A3: If you encounter a permission denied error while using the pip3 install command, it means you do not have the necessary permissions to install packages globally. In such cases, you can use the `–user` flag to install Boto3 locally to your user directory. The command will look like this:
“`
pip3 install –user boto3
“`
Q4: How do I upgrade Boto3 to the latest version?
A4: To upgrade Boto3 to the latest version, you can use the following command:
“`
pip3 install –upgrade boto3
“`
This command will install the latest available version of Boto3, replacing your existing installation, if any.
Q5: Are there any additional dependencies required for using Boto3?
A5: Boto3 has some additional dependencies beyond the Python standard library. These dependencies include Botocore, which is the low-level interface to the AWS API, as well as required third-party libraries like requests and dateutil. Luckily, when you install Boto3, these dependencies are automatically installed as well.
In conclusion, installing Boto3 for Python3 is a simple process that involves using the pip3 package manager. By following the step-by-step guide provided in this article, you can successfully install Boto3 and start leveraging the vast array of AWS services using Python.
Aws Credentials
Introduction:
As more and more businesses and developers migrate their infrastructure to the cloud, the need for robust security measures has become paramount. Amazon Web Services (AWS) is a leading provider of cloud computing services, and it offers a wide range of tools and features to help users secure their applications and data. One essential aspect of AWS security is managing and securing your AWS credentials. In this article, we will explore what AWS credentials are, why they are crucial, and how to set them up securely.
What are AWS Credentials?
AWS credentials are used to authenticate and authorize access to various AWS resources, services, and APIs. They consist of an access key ID and a secret access key, which are generated by AWS when you create an access key pair. These credentials are unique to each AWS account and provide secure access to your AWS resources.
Why are AWS Credentials Important?
AWS credentials play a vital role in ensuring the security and integrity of your AWS infrastructure. By properly managing and securing your credentials, you can prevent unauthorized access to your data, protect your AWS resources from malicious activities, and maintain compliance with security best practices.
Additionally, AWS credentials enable you to control access to your AWS resources and services. You can create multiple sets of credentials to grant specific permissions to different users or applications. This fine-grained access control ensures that users and services can only perform authorized actions, reducing the risk of accidental or intentional misuse of resources.
How to Securely Set Up AWS Credentials:
Setting up AWS credentials securely is crucial to protect your AWS resources from unauthorized access. Follow these best practices to ensure the security of your AWS credentials:
1. Use IAM: AWS Identity and Access Management (IAM) is a service that enables you to manage access to AWS resources securely. It is recommended to set up IAM users and assign appropriate permissions to them instead of using the root AWS account credentials directly.
2. Enable Multi-Factor Authentication (MFA): Enabling MFA adds an extra layer of security to your AWS account. By requiring an additional authentication factor, such as a randomized code generated by a mobile app or hardware device, MFA significantly reduces the risk of unauthorized access even if the credentials are compromised.
3. Rotate Credentials Regularly: It is essential to regularly rotate your AWS credentials to minimize the risks associated with long-term exposure. By changing your access keys periodically, you reduce the window of vulnerability in case they are accidentally leaked or compromised.
4. Use Strong Passwords: When creating IAM user accounts, ensure you use strong and unique passwords. A strong password includes a combination of uppercase and lowercase letters, numbers, and special characters. Avoid using common patterns or easily guessable passwords.
5. Apply the Principle of Least Privilege: When assigning permissions to IAM users, follow the principle of least privilege. Provide only the necessary permissions required for each user or application to perform their intended tasks. This ensures that users have the least possible access to your resources, reducing the risk of accidental or intentional misuse.
6. Monitor and Audit: Regularly monitor your AWS account and review the usage of credentials. AWS provides several tools and services, such as AWS CloudTrail and Amazon GuardDuty, to enable logging, monitoring, and auditing of activity related to your credentials. Monitoring can help identify any suspicious activities and potential security breaches.
FAQs:
Q: Can I use the same AWS credentials for different AWS regions?
A: Yes, the same AWS credentials can be used across different regions. The access key and secret access key remain the same, regardless of the region.
Q: How do I find my AWS access key and secret access key?
A: You can find your AWS access key and secret access key by logging into the AWS Management Console, navigating to the IAM service, selecting the desired IAM user, and accessing the “Security Credentials” tab.
Q: What happens if my AWS credentials are compromised?
A: If your AWS credentials are compromised, act quickly to delete the affected access keys and create new ones. Additionally, investigate the cause of the compromise and take the necessary steps to secure your AWS account and infrastructure.
Q: Can I restrict API access based on IP addresses?
A: Yes, you can use AWS Identity and Access Management (IAM) policies to restrict API access based on IP addresses. This can be configured at the IAM user level or through IAM roles for an entire AWS service or resource.
In conclusion, properly managing and securing your AWS credentials is crucial to maintaining the security of your AWS infrastructure. By following best practices, such as using IAM, enabling MFA, and regularly rotating credentials, you can protect your resources from unauthorized access and mitigate security risks. Stay vigilant, monitor your account, and take immediate action in the event of a compromise to ensure the ongoing security of your AWS credentials and resources.
Unable To Locate Credentials You Can Configure Credentials By Running Aws Configure
In the world of cloud computing, Amazon Web Services (AWS) has emerged as a leading provider, offering a wide range of powerful services and tools. For developers and administrators working with AWS, one of the fundamental tasks is to configure the necessary credentials to access AWS resources securely. However, it is not uncommon for users to encounter an error message stating “Unable to locate credentials” while trying to access AWS services. In this article, we will explore the reasons behind this error message and guide you on how to configure your credentials using the aws configure command.
Understanding the Error: “Unable to Locate Credentials”
When you receive the error message “Unable to locate credentials,” it means that the AWS SDK you are using is unable to find the necessary access key and secret access key to authenticate your requests. These credentials are essential for establishing secure communication between your AWS resources and the SDK or command-line tools you are using.
The aws configure command is an easy and efficient method to provide AWS SDKs or command-line tools with your access key and secret access key. This command allows you to specify the necessary information, including your AWS access key ID, secret access key, default region, and output format, securely.
Configuring Credentials with aws configure
To configure your credentials using the aws configure command, follow these steps:
1. Ensure that you have the AWS Command Line Interface (CLI) installed and set up on your machine. You can download and install the CLI from the official AWS documentation (https://aws.amazon.com/cli/).
2. Open your terminal or command prompt and enter the following command:
aws configure
3. You will be prompted to enter your AWS Access Key ID, Secret Access Key, default region, and output format. These details can be obtained from the AWS Management Console by navigating to the IAM (Identity and Access Management) dashboard and creating an access key for your IAM user.
4. Input your Access Key ID and Secret Access Key when prompted. These keys are unique to your AWS account and should be kept confidential.
5. Specify your default region, which is the region where you intend to perform most of your operations. For example, if you plan to work primarily in the US East (Ohio) region, enter “us-east-2.”
6. Choose your preferred output format. The default option is JSON, but you can choose other formats like text, table, or YAML.
7. Once you have provided all the required information, the aws configure command will create a file called credentials in your home directory (e.g., ~/.aws/credentials for Linux or %userprofile%\.aws\credentials for Windows). This file securely stores your access key and secret access key for future use.
Once you have successfully configured your credentials, you can use AWS SDKs or CLI commands without encountering the “Unable to locate credentials” error message.
FAQs
Q1: Why am I getting the “Unable to locate credentials” error message?
A1: This error occurs when AWS SDKs or command-line tools are unable to find the necessary access key and secret access key for authentication.
Q2: Can I configure multiple sets of credentials?
A2: Yes, you can configure multiple sets of credentials by running the aws configure command with different profiles. Specify the –profile flag followed by the desired profile name when configuring additional credentials.
Q3: What if I lose or forget my access key or secret access key?
A3: If you lose or forget your access key or secret access key, you need to create a new set of credentials in the AWS Management Console. Ensure that you update your credentials file with the new keys using the aws configure command.
Q4: Are there alternative methods to configure AWS credentials?
A4: Yes, apart from using the aws configure command, you can also configure AWS credentials through environment variables, AWS shared credentials file, or IAM roles for EC2 instances.
Q5: Can I use the same set of credentials across different AWS regions?
A5: Yes, your credentials are valid across all AWS regions. However, when you configure your default region using the aws configure command, the resources in the specified region will be the default when no region is explicitly provided.
Conclusion
Configuring credentials is a crucial step in working with AWS services securely. If you encounter the “Unable to locate credentials” error message, follow the steps outlined in this article to configure your credentials using the aws configure command. By providing the necessary access key ID and secret access key, you can establish a secure connection between your applications and AWS resources. Remember to keep your credentials confidential and update them whenever necessary to ensure optimal security and performance while working with AWS.
Images related to the topic botocore.exceptions.nocredentialserror: unable to locate credentials

Found 8 images related to botocore.exceptions.nocredentialserror: unable to locate credentials theme









Article link: botocore.exceptions.nocredentialserror: unable to locate credentials.
Learn more about the topic botocore.exceptions.nocredentialserror: unable to locate credentials.
- Boto3 Error: botocore.exceptions.NoCredentialsError: Unable …
- Resolving the Boto3 NoCredentialsError in Python – Rollbar
- Botocore.Exceptions.NoCredentialsError: Unable to Locate …
- How to Fix botocore.exceptions.NoCredentialsError: Unable to …
- unable to locate credentials – AI Search Based Chat – You.com
- Resolve “Unable to locate credentials” error in Amazon S3
- AWS CLI Unable To Locate Credentials | A Quick Fix – Bobcares
- fatal error: unable to locate credentials – AI Search Based Chat – You.com
- Python, Boto3, and AWS S3: Demystified
- dynamodb botocore.exceptions.nocredentialserror unable to …
See more: nhanvietluanvan.com/luat-hoc