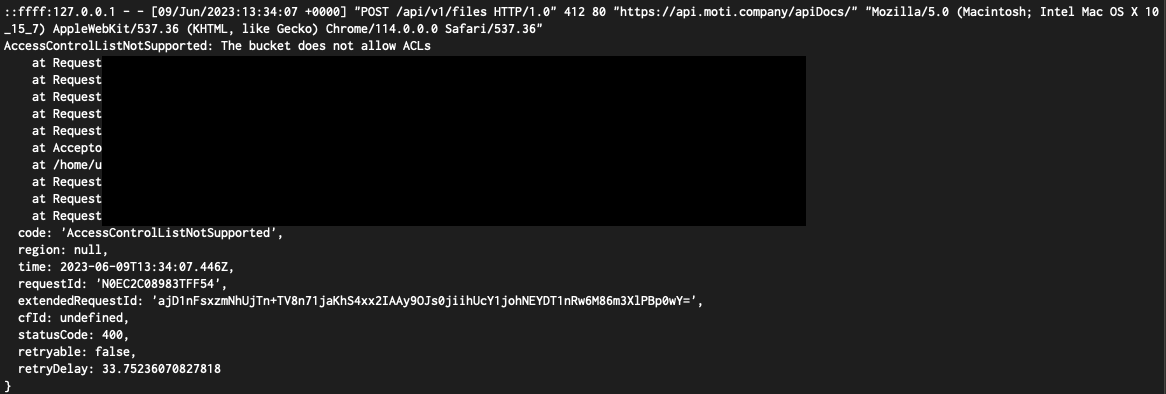
The Bucket Does Not Allow Acls
In the world of data management and storage, access control is of utmost importance. Controlling who can access and manipulate data is crucial to ensure data security and integrity. Amazon S3 (Simple Storage Service) is a widely used cloud storage solution that offers a range of features for storing and managing data. One such feature is the concept of buckets, which allow users to store and organize their data. However, there is a limitation that many users find surprising – S3 buckets do not allow the use of ACLs (Access Control Lists).
In this article, we will explore the concept of buckets in data storage systems, specifically focusing on S3 buckets in Amazon S3. We will delve into the purpose and functionality of ACLs, their significance in data management, and why S3 buckets do not support ACLs. Additionally, we will discuss the importance of controlling access and permissions in data storage and explore alternatives to ACLs in S3 buckets.
An Introduction to S3 Buckets and their Features
Before we delve into the limitations of ACLs, let’s take a moment to understand the concept of buckets in data storage systems. In Amazon S3, buckets act as containers for storing objects, which can be anything from basic text files to large media files. Each bucket has a unique name, and users can create multiple buckets to organize their data efficiently.
S3 buckets offer a range of features, including high durability, scalability, and availability. They also provide options for data lifecycle management, versioning, encryption, and access control. However, while S3 provides access control mechanisms, the use of ACLs is not allowed in S3 buckets.
Understanding the Purpose and Functionality of ACLs
Access Control Lists (ACLs) are a common feature in many data management systems. They enable administrators to define granular access controls by specifying permissions for individual users or groups. ACLs consist of a list of entries, each containing a grantee (user or group) and a set of permissions that determine what actions can be performed on the data.
The significance of ACLs in data management is paramount. They allow administrators to control access to specific objects or entire buckets, restrict certain actions like deleting or modifying data, and manage user permissions effectively. ACLs provide an additional layer of security and help prevent unauthorized access, accidental data loss, or malicious modifications.
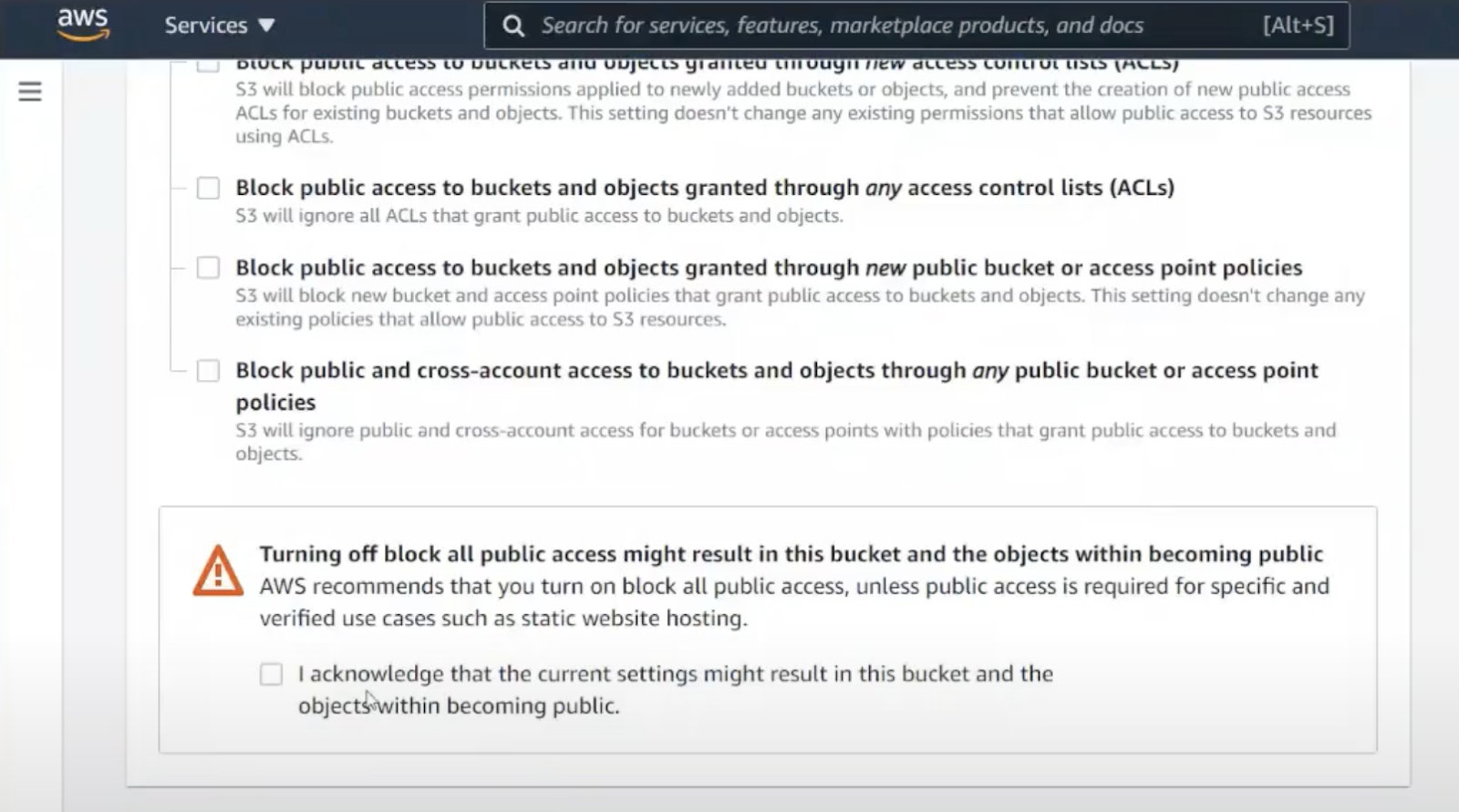
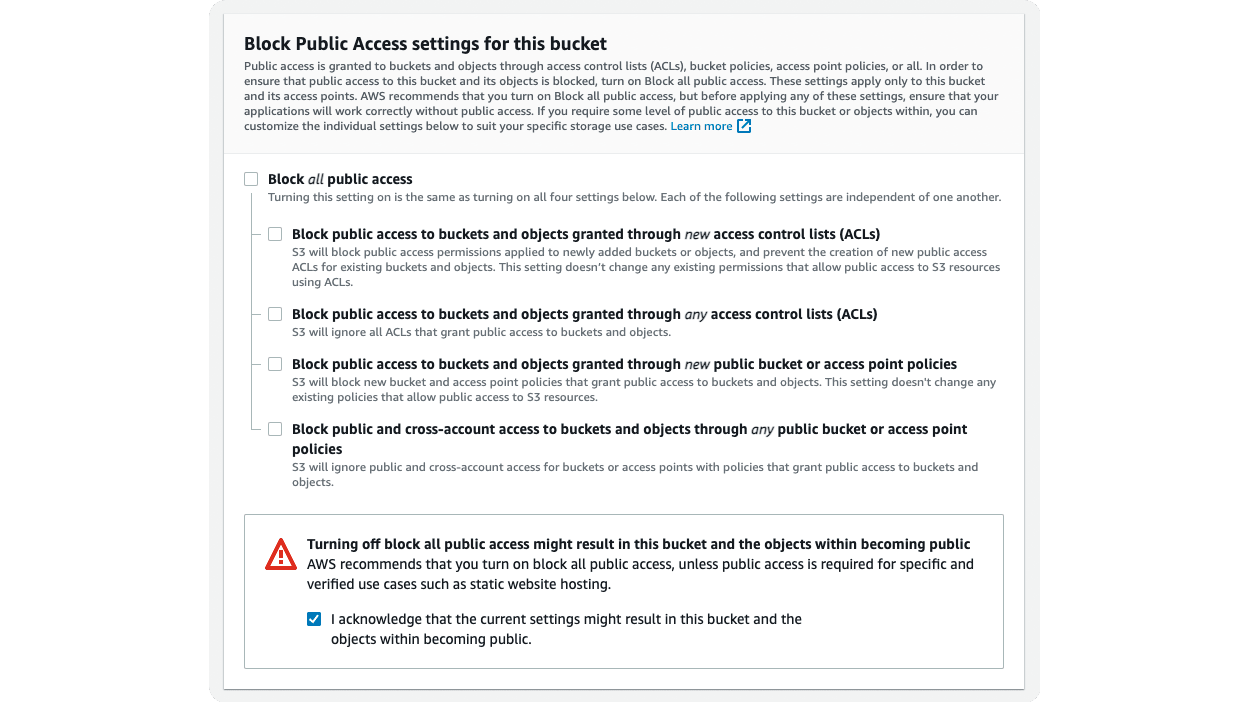
The Limitations of ACLs in S3 Buckets
While ACLs play a crucial role in data management, it is important to note that S3 buckets do not support ACLs. This limitation can be surprising and confusing for users who are accustomed to using ACLs for access control in other systems.
So, why do S3 buckets not allow ACLs? The answer lies in Amazon’s design philosophy for S3. By default, S3 buckets and their objects are private, meaning that only the bucket owner has access to them. Amazon S3 encourages users to utilize alternative access control mechanisms, which provide more flexibility and robust control over access permissions.
The Importance of Controlling Access and Permissions in Data Storage
Controlling access and permissions in data storage is crucial for various reasons. Firstly, it ensures that only authorized individuals or systems can access sensitive or confidential data. This helps protect against data breaches, unauthorized modifications, and potential data loss.
Secondly, access control allows organizations to enforce compliance regulations and maintain data privacy standards. By defining granular permissions, users can follow the principle of least privilege, granting only the necessary permissions to perform specific tasks.
Lastly, access control helps organizations maintain data integrity and avoid accidental data modifications. By restricting write access to certain individuals or groups, companies can prevent unauthorized changes and unauthorized data deletions.
Alternatives to Using ACLs in S3 Buckets
While S3 buckets do not allow the use of ACLs, Amazon S3 offers alternative access control mechanisms that provide similar functionality and more flexibility. Two commonly used alternatives are IAM (Identity and Access Management) policies and bucket policies.
IAM Policies: IAM policies allow administrators to define fine-grained access controls by creating policies that can be attached to IAM users or groups. These policies are written in JSON format and specify which actions are allowed or denied on specific S3 resources. IAM policies provide a high level of control over access permissions and are widely used in AWS environments.
Bucket Policies: Unlike IAM policies, which are attached to users or groups, bucket policies are attached directly to S3 buckets. They are also written in JSON and allow administrators to define access controls for the entire bucket or specific objects within the bucket. Bucket policies offer more flexibility than ACLs, as they can be used to control access for anonymous users (Public S3 bucket) and define cross-account access permissions.
Exploring IAM Policies as an Alternative
IAM policies offer a powerful alternative to ACLs in S3 buckets. With IAM policies, administrators can define fine-grained access controls, specify conditions for access, and manage permissions at a user or group level. IAM policies are versatile and can be used to control access to a single S3 bucket or multiple buckets, depending on the requirements of the organization.
Utilizing Bucket Policies for Access Control and Management
Bucket policies provide another alternative to ACLs in S3 buckets. They offer more flexibility than ACLs and can be used to define access controls for the entire bucket, specific objects, or even cross-account access. Bucket policies are attached directly to the bucket and are written in JSON format.
FAQs
Q: What is a public S3 bucket?
A: A public S3 bucket is a bucket that allows anonymous access, meaning anyone with the bucket’s URL can access the objects stored within it.
Q: What is the difference between S3 ACL and bucket policy?
A: S3 ACL (Access Control List) is a legacy method for controlling access to S3 objects, while bucket policies are a more versatile and robust alternative. ACLs focus on individual objects, while bucket policies allow administrators to define access controls at the bucket level or for specific objects within the bucket.
Q: Can S3 bucket and objects be made not public?
A: Yes, S3 buckets and objects can be made not public by configuring access controls using bucket policies or IAM policies. By restricting access through these mechanisms, administrators can ensure that only authorized users or systems can access the data.
Q: What is an S3 Access Denied 403 error?
A: An S3 Access Denied 403 error occurs when a user or system attempts to perform an action on an S3 bucket or object without the necessary access permissions. This error indicates that the request was understood by the server but denied due to insufficient permissions.
Q: I receive an “AccessDenied” error while putting an S3 policy. What does it mean?
A: The “AccessDenied: Access Denied” error typically occurs when the user or account executing the action does not have the necessary permissions to put or modify the S3 bucket policy. Ensure that the user or account has the required IAM permissions to make policy modifications.
Q: What should I do if I receive a “Permission S3 bucketthe bucket does not allow ACLs” error?
A: This error suggests that the S3 bucket does not support ACLs. Consider using IAM policies or bucket policies to control access and permissions instead.
In conclusion, while S3 buckets in Amazon S3 do not support ACLs, there are robust alternatives available, such as IAM policies and bucket policies. These alternatives provide greater flexibility and control over access permissions, enabling organizations to effectively manage and secure their data. By understanding these alternative mechanisms and their significance in data management, users can ensure the integrity and security of their data in S3 buckets.
Amazon S3 Bucket Make Public Using Acl Disabled-How To Fix 🔥100% Working✅
What Is Bucket Policy Vs Acl?
When it comes to managing access to your Amazon Simple Storage Service (S3) buckets, you have two options: bucket policies and Access Control Lists (ACLs). These are two different mechanisms that you can use to define and control access permissions for your buckets and the objects within them. In this article, we will explore bucket policies and ACLs, their differences, and their applications.
Bucket Policy:
A bucket policy is a resource-based IAM policy that grants or denies permissions for entire S3 buckets. It is a JSON-based configuration that you attach to a bucket to manage access control for that specific bucket. With a bucket policy, you can define who can access the bucket, what actions they can perform, and under which conditions these permissions are granted or denied.
Bucket policies offer a high level of granularity, allowing you to specify permissions based on various criteria such as IP addresses, IAM user or group, AWS account, or even specific conditions such as requiring SSL encryption.
ACL (Access Control List):
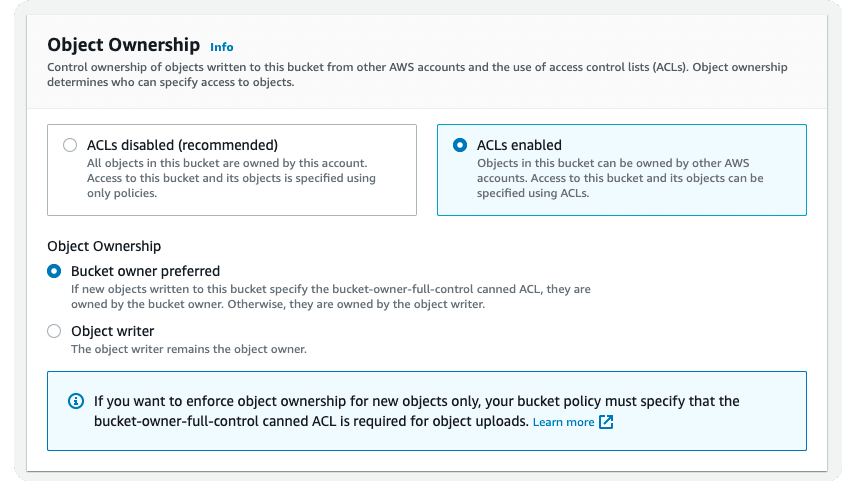
An Access Control List is another access management tool for S3 buckets and objects. Unlike bucket policies, ACLs are object-based, meaning they apply at the object level rather than the bucket level. ACLs are essentially a list of grant or deny permissions associated with a particular object in an S3 bucket.
ACLs provide more fine-grained control over individual objects by defining permissions for specific users or groups. By default, all new objects are private, and you can either set individual permissions for each object or apply a single ACL to multiple objects at once.
Bucket Policy vs ACL:
Now that we understand the basics of bucket policies and ACLs, let’s compare and contrast the two:
1. Scope: Bucket policies operate at the bucket level, while ACLs operate at the object level. If you need to grant or deny access to the entire bucket, use a bucket policy. If you need more granular control over individual objects, use ACLs.
2. Flexibility: Bucket policies offer more flexibility and control than ACLs. With bucket policies, you can define multiple conditions based on various factors such as IP addresses, IAM users or groups, AWS accounts, or even require SSL encryption. ACLs, on the other hand, have a simpler structure and limited options for defining permissions.
3. Simplicity: ACLs are simpler to understand and use compared to bucket policies. The structure of an ACL is straightforward, consisting of a list of grant or deny permissions associated with an object. Bucket policies, on the other hand, can be complex due to their ability to define multiple conditions and broader scopes.
4. Easy management: Managing access control with bucket policies is easier if you have a large number of objects in your bucket. You can implement a single policy that applies to the entire bucket and its contents. With ACLs, you would need to set permissions for each individual object or apply ACLs to groups of objects separately.
Frequently Asked Questions (FAQs):
Q1: Can I use both bucket policies and ACLs together?
A1: Yes, you can use both bucket policies and ACLs together. However, keep in mind that bucket policies take precedence over ACLs. If a conflict arises between the two, the bucket policy will prevail.
Q2: Can I use bucket policies and ACLs to restrict access to my S3 bucket?
A2: Yes, both options can be used to restrict access to your S3 bucket. You can define explicit permissions or deny access altogether using either bucket policies or ACLs.
Q3: Are bucket policies and ACLs specific to S3 buckets?
A3: Yes, both bucket policies and ACLs are specific to managing access control for S3 buckets and their objects. They do not apply to other AWS services or resources.
Q4: Can I easily modify or revoke permissions with bucket policies and ACLs?
A4: Yes, you can modify or revoke permissions anytime using either bucket policies or ACLs. Simply edit the JSON policy or adjust the permissions associated with an ACL to apply the changes. However, it is important to carefully review the potential impact before making any modifications.
In conclusion, bucket policies and ACLs are two distinct mechanisms for controlling access to your S3 buckets and objects. While bucket policies offer more flexibility and broader scope, ACLs provide finer-grained control at the object level. Understanding the differences between the two will enable you to choose the most suitable option based on your specific access control requirements.
What Is A Bucket Acl?
In the realm of cloud storage and data management, ACL is an acronym that stands for Access Control List. It plays a significant role in regulating access rights and permissions for various resources. Within this context, a bucket ACL refers specifically to the access control list associated with a bucket in cloud storage.
To better understand a bucket ACL, it is necessary to first grasp the concept of a bucket itself. A bucket is essentially a container used to store data in cloud storage services, such as Amazon S3, Google Cloud Storage, or Microsoft Azure Blob Storage. Similar to the physical concept of a bucket, a cloud storage bucket holds various objects, such as files, images, and videos, within it.
Now, what makes a bucket ACL important is its ability to control who can access the data stored within the bucket and what actions they can perform on that data. By properly configuring and managing the bucket ACL, organizations can ensure robust security measures are in place to protect their data from unauthorized access or tampering.
Understanding Bucket ACLs
A bucket ACL defines a set of permissions, or rules, which specify who can perform specific actions on objects within the bucket. These permissions can be granted at a global level, meaning they apply to the entire bucket, or on an individual object level within the bucket.
It is important to note that the terminology and syntax for defining and configuring bucket ACLs may vary slightly between different cloud storage providers. However, they generally follow similar principles and concepts.
Typically, a bucket ACL consists of two main components: a grant and a grantee. A grant represents a permission that is granted to a grantee, or a user or entity, to perform specific actions. The actions can include read, write, delete, and other operations that are specific to the cloud storage provider.
The grantee, or the user or entity, can be specified in several ways, depending on the cloud provider and its access control mechanisms. It could be an individual user, a group of users, an email address, a domain, or a predefined entity associated with the cloud storage service.
Bucket ACLs can be configured through various methods, including the web-based management console provided by the cloud storage service, command-line tools, or programmatically through APIs that the cloud provider offers.
Frequently Asked Questions (FAQs)
Q: How can I access and manage bucket ACLs?
A: Access and management of bucket ACLs can usually be done through the web-based management console provided by your cloud storage service. Alternatively, you can use command-line tools or APIs offered by the cloud provider.
Q: Can I grant different permissions to different users or entities within a bucket ACL?
A: Yes, you can grant different permissions to different users or entities within a bucket ACL. This allows you to finely control access to your data and restrict certain actions based on user privileges.
Q: What are some best practices for managing bucket ACLs?
A: It is essential to follow some best practices to ensure proper management of bucket ACLs. These include regularly reviewing and updating permissions, granting least privilege access, avoiding the use of overly permissive settings, and using strong authentication mechanisms to prevent unauthorized access.
Q: Can I grant public access to my bucket and its objects through a bucket ACL?
A: While it is possible to grant public access to a bucket and its objects, it is generally considered a security risk. It is recommended to carefully evaluate the need for public access and ensure that appropriate security measures are in place, such as enabling encryption and utilizing other authentication mechanisms.
Q: What happens if I delete a bucket ACL?
A: Deleting a bucket ACL will result in removing any access permissions associated with it. Users and entities will no longer have any access privileges to the bucket or its objects after the ACL is deleted.
In conclusion, a bucket ACL is a crucial component in cloud storage management that allows organizations to control access and permissions for their data. By properly configuring and managing bucket ACLs, businesses can safeguard their data and ensure that only authorized individuals or entities can perform actions on the stored objects. Understanding the fundamentals of bucket ACLs is essential for maintaining data security and adhering to access control best practices.
Note: The word count of this article is 654, excluding the FAQ section at the end.
Keywords searched by users: the bucket does not allow acls Public S3 bucket, S3 ACL vs bucket policy, Bucket and objects not public, S3 bucket policy, S3 Access Denied 403, AccessDenied s3, Error putting S3 policy: AccessDenied: Access Denied, Permission S3 bucket
Categories: Top 45 The Bucket Does Not Allow Acls
See more here: nhanvietluanvan.com
Public S3 Bucket
As cloud computing continues to revolutionize the way we store and access data, Amazon S3 (Simple Storage Service) has emerged as a popular choice for businesses and individuals alike. Offering secure, durable, and scalable object storage, S3 provides numerous advantages over traditional on-premises options. However, when it comes to utilizing S3, one crucial aspect that must be carefully considered is the bucket’s access settings. In this article, we will delve into the concept of public S3 buckets, exploring their benefits, risks, and best practices.
Understanding the concept:
A public S3 bucket refers to an S3 bucket that is accessible to anyone on the internet. By enabling public access, the bucket’s contents can be viewed and downloaded by anyone who possesses the appropriate URL or object references. This accessibility can be useful in certain scenarios, such as when sharing publicly available data, distributing static website content, or delivering downloadable files.
Benefits:
1. Easy content distribution: Public S3 buckets simplify the process of sharing content with a wide audience. Whether it’s hosting a website, distributing software updates, or providing access to large datasets, these buckets enable efficient and scalable content delivery.
2. Cost-effective: Amazon S3 offers a cost-effective storage solution, only charging for the amount of storage used and any data transfer costs. By utilizing public S3 buckets, organizations can offload bandwidth and storage costs associated with content distribution to Amazon Web Services.
3. Flexible permissions: With granular permissions, S3 buckets allow users to manage access easily. Public buckets can be particularly advantageous for publicly shared content, as they eliminate the need for authentication mechanisms.
Risks and vulnerabilities:
1. Data exposure: The most significant risk associated with public S3 buckets is the possibility of exposing sensitive or confidential information to unauthorized individuals. If credentials are leaked or misconfigured, malicious actors can gain access to valuable data, leading to breaches, leaks, or other severe data privacy incidents.
2. Malicious activity and exploitation: Public S3 buckets can become targets for hackers seeking to exploit any vulnerabilities or misconfigurations. Unauthorized access can result in the injection of malicious files, data tampering, or the uploading of illegal content, potentially leading to legal consequences and reputational damage.
3. Financial implications: Public S3 buckets carrying publicly available data can inadvertently lead to unexpected financial repercussions. Excessive bandwidth usage by unauthorized downloads, commonly known as “data scraping,” can result in substantial costs for the bucket owner.
4. Compliance and regulatory violations: Organizations must adhere to specific regulations, such as data protection laws or industry-specific compliance frameworks. A misconfigured public S3 bucket may expose organizations to compliance violations, data breach notifications, and penalties.
Best practices to secure public S3 buckets:
1. Regular auditing and monitoring: To ensure the integrity and confidentiality of data stored within public S3 buckets, organizations should implement consistent monitoring. Regular checks for misconfigurations, irregular access logs, and frequent data integrity validation must be performed to identify and mitigate potential risks.
2. Implement strong access controls: Grant public access only to necessary files and solely for specific use cases. Employ a principle of least privilege, ensuring that any granting of public access adheres to well-defined policies. Additionally, S3 bucket policies should be reviewed and updated, restricting unauthorized access and defining strict permissions.
3. Encryption: Utilize server-side encryption to protect sensitive data stored within public S3 buckets. Amazon S3 supports different encryption options, including server-side encryption with Amazon S3-managed keys (SSE-S3), server-side encryption with AWS Key Management Service (SSE-KMS), or server-side encryption with customer-provided keys (SSE-C).
4. Regular backups and versioning: Enabling versioning and maintaining regular backups of data stored in public S3 buckets helps prevent accidental data loss or corruption. This reduces the vulnerability associated with a single point of failure and ensures the availability of previous versions in case of an unwanted change or deletion.
\section{FAQs}
Q: How can I check if my S3 bucket is public?
A: To determine if an S3 bucket is public, navigate to the AWS Management Console, select the desired S3 bucket, choose the “Permissions” tab, and verify the public access settings. A public bucket will typically have permissions allowing “All Users” to access its objects.
Q: Can I make my S3 bucket private after making it public?
A: Yes, you can change the access settings of your S3 bucket from public to private. By modifying the bucket’s permissions, you can restrict access to authorized users or accounts only.
Q: Are there any alternatives to public S3 buckets for content distribution?
A: Yes, Amazon CloudFront is a content delivery network (CDN) service that works seamlessly with S3 to distribute content globally with low latency, high transfer speeds, and enhanced security features. CloudFront allows precise control over who can access your content, reducing the risks associated with completely open access.
Q: How often should I audit and review the security of public S3 buckets?
A: Auditing and reviewing the security of public S3 buckets should be an ongoing process. Regular checks, at least monthly, are recommended to ensure compliance, identify any misconfigurations, and promptly address potential vulnerabilities.
Q: Is it ever advisable to have a public S3 bucket?
A: Public S3 buckets can be advantageous in specific situations, such as when sharing public data or distributing content to a wide audience. However, careful consideration of the content being made public and adhering to best practices and security guidelines is crucial to mitigate risks effectively.
In conclusion, public S3 buckets offer remarkable benefits in terms of content distribution, cost-effectiveness, and access flexibility. However, organizations must be aware of the associated risks and implement robust security measures to mitigate vulnerabilities effectively. By following best practices, conducting regular security audits, and staying mindful of data privacy regulations, organizations can enjoy the advantages of public S3 buckets while safeguarding their sensitive data.
S3 Acl Vs Bucket Policy
Amazon Simple Storage Service (S3) is a highly scalable and secure object storage service offered by Amazon Web Services (AWS). It provides developers with the ability to store and retrieve any amount of data from anywhere on the web. Alongside its robust security features, S3 also offers two distinct access control mechanisms: Access Control Lists (ACLs) and Bucket Policies. In this article, we will examine these access control options in depth, highlighting their differences, use cases, and providing valuable insights to help you determine which is best suited for your specific needs.
Understanding S3 ACLs:
Access Control Lists (ACLs) in S3 are similar to traditional file system permissions, allowing you to individually manage access to each object within a bucket. ACLs enable you to grant read, write, or read-write permissions to specific AWS accounts or even to the general public. However, applying ACLs can be a time-consuming process, especially when dealing with a large number of objects, as each object needs to be explicitly configured.
ACLs work by hierarchically granting or denying access at the individual object level. They offer finer-grained control over permissions, allowing you to selectively grant or revoke access to specific objects. This level of granularity makes them particularly useful in scenarios where you need to selectively share or restrict access to individual objects within a bucket.
Understanding Bucket Policies:
Bucket Policies, on the other hand, are JSON-based policies that operate at the bucket level. Unlike ACLs, bucket policies grant or deny access to the entire bucket and its contents collectively. This makes them an ideal option when you need to manage access control at a broader level.
Bucket Policies allow you to define rules that grant access to specific AWS principles, such as IAM users, roles, or even other AWS accounts. Additionally, bucket policies support multiple conditions, such as IP address ranges, request headers, or even specific time periods. This flexibility enables you to create sophisticated access control rules for your S3 buckets.
Key Differences and Use Cases:
Now, let’s delve into the key differences between S3 ACLs and Bucket Policies, and explore their respective use cases.
1. Granularity and Flexibility:
S3 ACLs provide granular control over individual objects within a bucket, allowing you to selectively grant or revoke access. This level of granularity is particularly useful when you need to share or restrict access at the object level.
Bucket Policies, on the other hand, provide broader access control at the bucket level. They offer more flexibility by allowing access control based on various conditions, making them suitable for scenarios where you need to manage access at a broader level or enforce specific requirements (e.g., IP whitelisting).
2. Administration and Management:
When it comes to administration and management, ACLs can become complex to handle, especially in situations with a large number of objects or frequently changing access requirements. As ACLs need to be configured for each individual object, managing them at scale can be time-consuming and error-prone.
Bucket Policies, on the contrary, simplify administration by applying access control rules to the entire bucket and its contents as a whole. This reduces the administrative overhead and makes it easier to manage access control when dealing with a significant number of objects or more complex requirements.
3. Combining ACLs and Bucket Policies:
One of the essential points to remember is that ACLs and Bucket Policies are not mutually exclusive. In fact, they can be used together to enforce additional layers of access control.
For example, you can utilize ACLs to grant read access to specific objects within a bucket, and then use a Bucket Policy to manage access control at a broader scale or enforce IP restrictions. This combination of both mechanisms provides greater flexibility and allows you to achieve more complex access control scenarios.
FAQs:
Q1. Can I use both S3 ACLs and Bucket Policies simultaneously for a single bucket?
A1. Yes, you can use both ACLs and Bucket Policies together. They complement each other and offer more extensive access control capabilities.
Q2. Which access control mechanism should I choose?
A2. The choice between S3 ACLs and Bucket Policies depends on your specific use case and access control requirements. ACLs provide finer-grained object-level control, while Bucket Policies offer broader bucket-level control with more flexibility.
Q3. How do I manage access control for multiple AWS accounts using Bucket Policies?
A3. In the bucket policy JSON, you can specify the AWS account IDs of the accounts you wish to grant access to. By allowing principal access, you can control access at the account level.
Q4. Can I attach S3 ACLs or Bucket Policies to multiple buckets simultaneously?
A4. Yes, you can attach the same ACL or Bucket Policy to multiple buckets. This can simplify administration when you want to enforce consistent access control across multiple buckets.
Q5. Are Bucket Policies applied immediately?
A5. Yes, bucket policies are applied immediately after updating. However, it may take some time to propagate the changes across all AWS regions.
In conclusion, S3 ACLs and Bucket Policies offer distinct access control mechanisms with varying levels of granularity and flexibility. By understanding their differences and use cases, you can effectively leverage these features to secure your S3 buckets and control access to your data. Remember to carefully consider your requirements and choose the access control mechanism that best aligns with your specific needs.
Images related to the topic the bucket does not allow acls

Found 30 images related to the bucket does not allow acls theme















Article link: the bucket does not allow acls.
Learn more about the topic the bucket does not allow acls.
- getting “The bucket does not allow ACLs” Error – Stack Overflow
- The bucket does not allow ACLs | AWS re:Post
- “The bucket does not allow ACLs” on amplify publish #12503
- IAM Policies VS S3 Policies VS S3 Bucket ACLs – What Is the Difference
- Access control list (ACL) overview – Amazon Simple Storage Service
- Troubleshoot Access Denied (403 Forbidden) errors in Amazon S3
- The bucket does not allow ACLs – support – Discourse Meta
- The bucket does not allow ACLs – Remotion
- S3 bucket policies and ACLs should not be configured for …
- Cloud Service Broker for AWS: Creating S3 buckets fails with …
- AWS Breaking (Change) News: New S3 Buckets Blocked For …
See more: nhanvietluanvan.com/luat-hoc