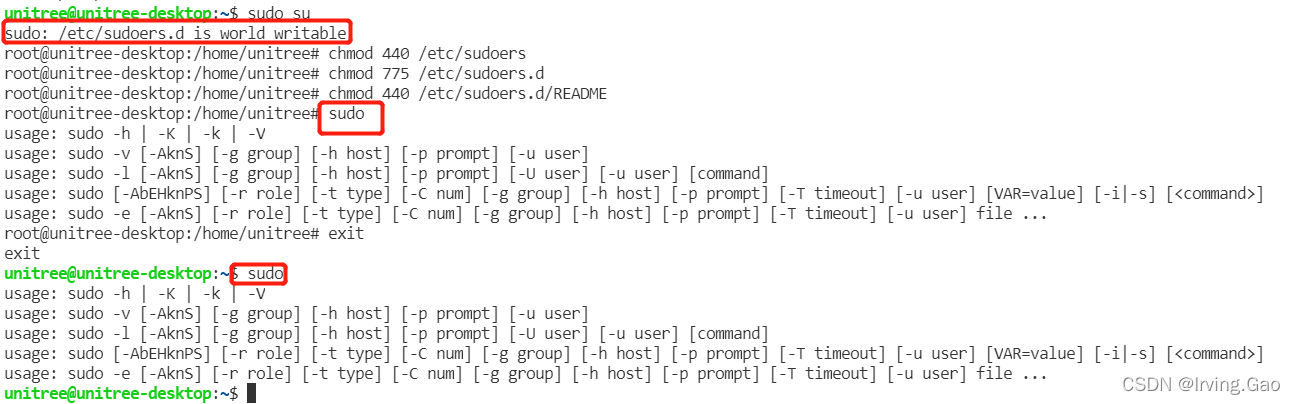
Sudo /Etc/Sudo.Conf Is World Writable
Introduction:
The sudo system is a crucial tool for managing user privileges on Unix-like operating systems. It allows certain users to execute specific commands as another user, typically as the superuser or root. However, it is important to ensure that the configuration files used by sudo are properly secured, as any unauthorized modifications can pose significant risks. In this article, we will delve into the world-writable permissions on the /etc/sudo.conf file, analyzing the implications, potential exploits, and best practices for securing it.
What does it mean for a file to be world writable?
When a file is labeled as “world writable,” it means that all users on the system, regardless of their ownership or group, have the permission to modify or delete the file. This level of access can be a serious vulnerability, as it enables any user to tamper with critical system files, potentially leading to unauthorized privilege escalation and compromising the security of the entire system.
Understanding the purpose of /etc/sudo.conf in the sudo system:
The /etc/sudo.conf file is a crucial configuration file utilized by the sudo system. It allows system administrators to customize and fine-tune the behavior of sudo. It can include settings such as the default path for commands, log handling, and plugin options. By modifying the /etc/sudo.conf file, administrators can define global settings that affect all users who utilize the sudo command.
The potential risks of having /etc/sudo.conf set as world writable:
Setting /etc/sudo.conf as world writable can expose the system to numerous risks. Malicious actors can exploit this vulnerability to make unauthorized modifications to the file, potentially granting themselves elevated privileges or causing disruptions in the system’s functionality. By altering the configurations in /etc/sudo.conf, attackers can manipulate the behavior of sudo, allowing them to bypass security measures or perform unauthorized actions.
How world-writable permissions on /etc/sudo.conf can be exploited:
Given that /etc/sudo.conf contains critical settings for the sudo system, unauthorized modifications can have severe consequences. Attackers can potentially add or modify entries that grant unauthorized users root access or elevate their privileges. This could lead to the compromise of sensitive data, the installation of malicious software, or even a complete takeover of the system.
Potential consequences of unauthorized modifications to /etc/sudo.conf:
Unauthorized modifications to /etc/sudo.conf can result in severe repercussions for the system and its users. These consequences may include unauthorized privilege escalation, unauthorized execution of sensitive commands, unintended permissions for regular user accounts, and the inability to manage user privileges efficiently. Additionally, compromised configurations in /etc/sudo.conf can affect the overall stability and security of the system.
Best practices for securing /etc/sudo.conf from unwanted modifications:
1. Restrict file permissions: Ensure that the /etc/sudo.conf file is not world writable. Only the root user or a specific group authorized by the administrator should have write permissions on the file.
2. Implement proper ownership: Set the ownership of /etc/sudo.conf to root or another trusted system account. This prevents unauthorized users from modifying it.
3. Regularly monitor file permissions: Periodically check the permissions and ownership of /etc/sudo.conf to detect any unauthorized changes.
4. Limit access to the system: Restrict physical and network access to the system hosting /etc/sudo.conf to reduce the risk of unauthorized modifications.
5. Apply patches and updates: Keep the system up to date with the latest security patches and updates to minimize the risk of vulnerabilities that could be exploited.
Steps to check and fix world-writable permissions on /etc/sudo.conf:
Checking and fixing world-writable permissions on /etc/sudo.conf involves the following steps:
1. Open a terminal or command prompt.
2. Type the command “ls -l /etc/sudo.conf” to display the current permissions and ownership of the file.
3. If the permissions show that the file is world writable or the ownership is incorrect, proceed to fix it.
4. To change the permissions, use the command “sudo chmod 644 /etc/sudo.conf” to make it read and writeable only by the root user.
5. If the ownership is incorrect, utilize the command “sudo chown root:root /etc/sudo.conf” to set the file’s ownership to the root user and group.
6. Finally, verify the changes by again checking the permissions and ownership with the command “ls -l /etc/sudo.conf.”
Monitoring and detecting unauthorized changes to /etc/sudo.conf:
Implementing regular monitoring and detection procedures is essential to identify any unauthorized changes to /etc/sudo.conf. This can be accomplished by using file integrity monitoring tools, which periodically scan and compare the current state of the file against a known-good baseline. Additionally, tracking system logs for suspicious activities, such as failed attempts to modify or access /etc/sudo.conf, can also aid in detecting unauthorized changes.
Ensuring the integrity of /etc/sudo.conf for a secure sudo configuration:
Maintaining the integrity of /etc/sudo.conf is crucial for a secure sudo configuration. By following the best practices mentioned above, monitoring file permissions and ownership, and promptly addressing any detected unauthorized modifications, administrators can ensure the file’s integrity and minimize the risk of compromise.
In conclusion, the world-writable permissions on /etc/sudo.conf can pose significant risks to the security and stability of a system. Unauthorized modifications to this critical configuration file can lead to unauthorized privilege escalation, compromised data, and system compromise. By implementing best practices for securing /etc/sudo.conf, regularly monitoring for unauthorized changes, and promptly addressing any detected vulnerabilities, system administrators can maintain a secure sudo configuration. Remember to follow the necessary steps to check and fix world-writable permissions and utilize monitoring tools to ensure the integrity of /etc/sudo.conf.
Sudo: Fatal Error, Unable To Load Plugins | Sudo: /Etc/Sudo.Conf Is World Writable
What Are The Default Permissions For Sudo Conf?
The sudo.conf file is a configuration file for the sudo (superuser do) command in Linux and Unix systems. It defines various settings and options for sudo, allowing administrators to customize its behavior. However, due to the sensitive nature of sudo, it is important to understand the default permissions for the sudo.conf file to ensure secure system administration. In this article, we will delve into the default permissions for this crucial file, discussing their implications and addressing frequently asked questions.
Default Permissions for sudo.conf:
By default, the sudo.conf file has permissions set to 0440 or 0460, depending on the distribution. This means that the owner, usually the root user, has read and write permissions, while the group (often also root) has only read permissions. Other users on the system have no permissions to access the file.
Implications of Default Permissions:
The default permissions for sudo.conf help to ensure the security and integrity of the file. By restricting write access to only the owner, it prevents unauthorized modifications to the configuration, reducing the risk of compromising the system. Additionally, by preventing access from other users, it helps to maintain confidentiality and protects sensitive information contained within the file.
FAQs:
Q: What is the sudo.conf file used for?
A: The sudo.conf file is used to customize the behavior of the sudo command. It allows administrators to specify various settings, such as restricting certain commands, controlling the use of environment variables, and defining default settings for sudo.
Q: How do I check the permissions of the sudo.conf file?
A: You can check the permissions of the sudo.conf file by using the “ls -l” command in the terminal. It will display the file permissions in the following format: -rw-r–r–. The first character indicates the file type (- for regular files). The next three characters (rw-) represent the owner’s permissions, the second three characters (r–) represent the group’s permissions, and the last three characters (r–) represent other users’ permissions.
Q: Can I change the permissions of the sudo.conf file?
A: Yes, it is possible to change the permissions of the sudo.conf file using the chmod command. However, it is crucial to exercise caution and understand the implications of changing permissions. Modifying permissions can potentially introduce security vulnerabilities if not done properly.
Q: What are the risks of improper permissions on the sudo.conf file?
A: Allowing unauthorized write access to the sudo.conf file can lead to malicious modifications, such as granting excessive privileges to users or allowing unauthorized execution of commands. Similarly, granting read access to the file for non-privileged users can expose sensitive information, leading to elevated risks of system compromise.
Q: Are there any recommendations for securing the sudo.conf file?
A: Yes, there are several recommendations for securing the sudo.conf file. Firstly, it is advised to keep the default permissions intact unless there is a specific requirement to change them. Restricting write access to the owner and limiting read access to the root group helps maintain a secure configuration. Additionally, it is essential to regularly monitor the file for any unauthorized changes and promptly investigate any suspicious activities.
In conclusion, understanding the default permissions for the sudo.conf file is crucial for secure system administration. The default permissions of 0440 or 0460 effectively restrict write access to the owner and limit read access to the group, ensuring the integrity and security of the configuration. It is crucial to exercise caution when modifying these permissions, as improper changes can introduce security risks. By adhering to recommended security practices and regularly monitoring the sudo.conf file, system administrators can maintain a secure and reliable sudo configuration.
Does Sudo Change Permissions?
When it comes to managing files and directories on a Linux or Unix-based system, it is essential to understand the concept of permissions and how they impact access control. Permissions play a crucial role in ensuring the security and integrity of your system by specifying who can do what with certain files and directories. One widely used command to perform tasks that require elevated privileges is “sudo.” But what exactly does sudo do? More specifically, does sudo change permissions? This article aims to delve into the topic and shed light on this frequently asked question.
Understanding Permissions and Superuser Rights
Before we dive into the impact of the sudo command on permissions, let’s quickly review the fundamentals of permissions and superuser rights. In Unix-like operating systems, every file and directory is associated with three sets of permissions: read, write, and execute. These permissions can be assigned separately for three different entities: the owner of the file, the group to which the file belongs, and others (anyone who is not the owner or a member of the group).
The superuser, sometimes referred to as root, is a special user account that holds absolute power on the system. The superuser has the ability to override any permission restrictions and perform any task without limitation. By default, only the superuser can change system-wide settings, modify protected files, and execute critical administrative commands.
Understanding the Sudo Command
The sudo command, which stands for “superuser do,” enables authorized users to execute specific commands as the superuser or another user with elevated privileges. When using the sudo command, users are required to authenticate themselves with their own passwords, providing an additional layer of security. This allows system administrators to delegate certain tasks to trusted users without sharing the superuser password.
The primary purpose of sudo is not to change permissions, but rather to temporarily gain elevated privileges to perform actions that would otherwise require superuser rights. By invoking sudo, users can execute commands as if they were the superuser, granting them access to restricted resources and operations.
Impact of Sudo on Permissions
Now that we have a solid understanding of permissions and the sudo command, let’s address the central question: does sudo change permissions? The answer is both yes and no. Confusing, right? Let’s clarify.
When a user runs a command with sudo, it doesn’t necessarily change the permissions of the file or directory being accessed. However, it allows the user to perform actions that require elevated privileges, effectively bypassing the access restrictions imposed by permissions.
For example, suppose you have a file that can only be read and modified by the superuser (like some critical system logs). If you try to open and edit this file without sudo, you will encounter a “Permission Denied” error. However, if you use sudo to open the file with a text editor or a command-line text-processing tool, you will be able to make the modifications successfully. Nonetheless, the original permissions of the file will remain untouched.
In contrast, certain actions performed with sudo can indirectly affect permissions. For instance, running a command with sudo to change the ownership or modify the permissions of a file will indeed alter the permissions of that particular file. However, it’s important to emphasize that it is the command executed with sudo that modifies the permissions, not the act of using sudo itself.
Frequently Asked Questions
Q: Can sudo change the permissions of a file?
A: No, using sudo itself does not directly change the permissions of a file. However, executing a command with sudo that modifies the permissions or ownership of a file will indeed modify those permissions.
Q: Can I use sudo to gain superuser rights permanently?
A: No, using sudo only grants temporary elevated privileges for the execution of a specific command or set of commands. Once the task is completed, the user returns to their regular privileges.
Q: Can I use sudo to delete critical system files?
A: Yes, with superuser rights obtained through sudo, it is possible to delete critical system files. Therefore, extreme caution should be exercised when using sudo to avoid unintended consequences.
Q: Can I restrict certain commands from being executed with sudo?
A: Yes, system administrators can configure the sudoers file to restrict specific commands from being executed with sudo. This is done by modifying the sudoers configuration using the sudo visudo command.
Q: Are there alternatives to using sudo for elevated privileges?
A: Yes, alternatives to using sudo include the su command, which allows switching to the root user account entirely, and the graphical interface provided by applications like “gksu” and “kdesu.”
In conclusion, the sudo command does not directly change the permissions of files or directories. Instead, it enables users to execute specific commands with elevated privileges, bypassing the access restrictions imposed by permissions. Understanding the distinction between using sudo and the actual modifications to permissions is crucial for efficiently and securely managing your Linux or Unix-based system.
Keywords searched by users: sudo /etc/sudo.conf is world writable sudo: /etc/sudoers is owned by uid 1000, should be 0, Wrong permissions on configuration file should not be world writable, Sudo: unable to stat /etc/sudoers permission denied, Sudo: unable to initialize policy plugin, Chown changing ownership of etc sudoers Operation not permitted, Pkexec must be setuid root, Etc sudoers is owned by uid 1000 should be 0 wsl, Chmod 777 etc
Categories: Top 58 Sudo /Etc/Sudo.Conf Is World Writable
See more here: nhanvietluanvan.com
Sudo: /Etc/Sudoers Is Owned By Uid 1000, Should Be 0
When it comes to managing user privileges on a Unix-like operating system, sudo is an invaluable tool. It allows users to execute commands with the security privileges of another user, commonly the superuser or root. This capability empowers system administrators to delegate some administrative tasks to regular users, limiting potential security risks. However, occasionally, issues may arise, and one such issue is when the ownership of the sudoers file, located at /etc/sudoers, is incorrectly set to UID 1000 instead of 0. In this article, we will delve into why this issue occurs, its implications, and how it can be resolved.
Understanding the Issue:
By default, the sudoers file should be owned by the superuser, with a User ID (UID) of 0. A UID of 0 represents the root user, while other UIDs are assigned to regular users. When the ownership of the sudoers file is set to UID 1000, it means that a regular user, with a non-privileged UID, owns the file. This situation can lead to security vulnerabilities, as the incorrect ownership allows the user to potentially modify the file and escalate their privileges, undermining the intended security model.
Possible Causes:
The incorrect ownership of /etc/sudoers can occur due to a variety of reasons. One possible cause is the improper modification of ownership or permissions by a system administrator. Alternatively, a glitch during the system’s setup or an error while running tools or scripts for managing user privileges could result in this misconfiguration.
Implications:
The ownership of /etc/sudoers being set to UID 1000 poses several risks to the system’s security. As mentioned earlier, the file can potentially be modified by the user who owns it. This user may leverage this access to elevate their privileges, gain unauthorized control over critical system resources, or perform malicious activities. Therefore, rectifying this issue is of utmost importance to ensure the system remains secure and protected.
Resolving the Issue:
Resolving the sudoers file ownership issue involves reverting it to the correct UID of 0, making the superuser the file owner. The following steps outline how this can be done:
1. Access the system as a user with sudo privileges or as the root user.
2. Open a terminal or shell prompt.
3. Execute the following command to check the current ownership of /etc/sudoers:
“`$ ls -l /etc/sudoers“`
4. If the command displays UID 1000 instead of 0, proceed with changing the ownership.
5. Execute the following command to change the owner of /etc/sudoers back to UID 0:
“`$ sudo chown root:root /etc/sudoers“`
6. Verify that the ownership has been corrected by re-executing the command from step 3.
FAQs:
Q: Is it necessary to resolve the incorrect ownership of /etc/sudoers?
A: Yes, it is highly recommended to rectify the issue. The incorrect ownership poses a security risk and may allow unauthorized users to escalate their privileges.
Q: Can I change the ownership of the sudoers file manually using the graphical file manager?
A: It is possible, but it is generally recommended to use the command-line approach mentioned in the steps above. Command-line methods ensure accuracy and allow for automation if required.
Q: How can I prevent this issue from occurring in the future?
A: To avoid this issue, it is essential to follow best practices when managing user privileges. This includes limiting access to administrative accounts, double-checking changes made to system files, and regularly auditing the permissions and ownership of critical files.
Q: Are there any alternatives to sudo for managing user privileges?
A: Yes, alternatives like su (substitute user) are available, but sudo is widely preferred due to its advanced features, fine-grained control, and better auditability.
Q: Can I use other tools to check the permissions and ownership of /etc/sudoers?
A: Yes, there are various commands you can use, such as stat, getfacl, or even a graphical file manager, to verify ownership and permissions.
In conclusion, correctly configuring the ownership of the sudoers file in Unix-like systems is crucial to maintaining a secure environment. Having the file owned by a non-privileged user, identified by UID 1000 instead of 0, can introduce significant security risks, potentially compromising the entire system. By adhering to the corrective steps outlined in this article, system administrators can effectively mitigate these vulnerabilities and safeguard the integrity of their systems.
Wrong Permissions On Configuration File Should Not Be World Writable
Configuration files play a crucial role in the proper functioning of software and applications. These files contain important settings and parameters that dictate how a program functions and interacts with its environment. However, it is imperative to ensure that the permissions on these configuration files are set correctly to maintain security and prevent unauthorized access.
When it comes to file permissions, a common mistake is setting configuration files as world-writable. This means that anyone with read and write access to the system can modify the configuration file at will, potentially compromising the security and stability of the entire system. In this article, we will delve into the reasons why wrong permissions on configuration files should not be world-writable, and highlight the importance of setting appropriate file permissions for these critical files.
1. Security Concerns:
Allowing world-writable permissions on configuration files introduces serious security risks. Unauthorized users or malicious actors can easily modify the configuration file, potentially injecting malicious code or altering critical settings. This could lead to unauthorized access, data breaches, or even complete compromise of the system. By restricting write access to only authorized users or system processes, the risk of such security incidents can be significantly mitigated.
2. Stability and Reliability:
Configuration files define how software behaves and interacts with the system. Wrong permissions on these files can result in accidental changes or corruption, leading to instability and unreliable performance of the software. This could prevent the system from functioning optimally or even cause it to crash. By restricting write access to trusted sources, errors caused by accidental modifications can be minimized, ensuring the stability and reliability of the system.
3. Compliance and Regulations:
In many industries, organizations are required to adhere to strict compliance and regulatory standards. These standards often mandate specific controls around access and modification of critical configuration files. By setting appropriate permissions, organizations can ensure they meet these requirements, avoid penalties, and maintain the integrity of their systems.
4. Mitigating Human Errors:
Mistakes can happen, even by well-intentioned individuals. Allowing world-writable permissions on configuration files increases the likelihood of accidental modifications or deletions, especially in environments with multiple users. By restricting write access to only trusted personnel or automated processes, the chances of inadvertent errors can be significantly reduced, minimizing downtime and potential security breaches.
FAQs:
1. Why should configuration files be protected from unauthorized modifications?
Configuration files control how software operates and interacts with the system. Unauthorized modifications can lead to security breaches, instability, and unreliable performance.
2. What are the recommended permissions for configuration files?
Ideal permissions for configuration files vary depending on the specific needs of the system and software. However, it is generally advised to restrict write access to trusted users or processes and limit read access to relevant parties only.
3. How can I check the permissions on my configuration files?
On Unix-based systems, you can use the `ls -l` command to view the permissions of files. The output will display the owner, group, and others’ permissions as a series of letters (e.g., rwxr-xr–).
4. What are some best practices for securing configuration files?
a. Restrict write access to only trusted users or processes.
b. Ensure appropriate ownership and group permissions.
c. Regularly monitor and audit changes to configuration files.
d. Encrypt sensitive information within the files.
e. Regularly update and patch software to fix any known vulnerabilities.
5. Can incorrect permissions on configuration files lead to system failures?
Yes, incorrect permissions can lead to system failures. Accidental modifications or corruption of these critical files can result in instability, crashes, and unreliable software performance.
Conclusion:
Wrong permissions on configuration files represent a serious security risk that can compromise the integrity, stability, and reliability of the entire system. By ensuring that these files are not world writable, businesses can protect themselves from unauthorized access, data breaches, and potential system failures. It is crucial to implement appropriate permissions, regularly monitor changes, and follow best practices to maintain the security and optimal performance of software and applications.
Images related to the topic sudo /etc/sudo.conf is world writable

Found 45 images related to sudo /etc/sudo.conf is world writable theme













Article link: sudo /etc/sudo.conf is world writable.
Learn more about the topic sudo /etc/sudo.conf is world writable.
- How to solve “sudo: /etc/sudoers.d is world writable”
- How to fix this sudo: /etc/sudoers is world writable?
- How to correct the permissions of sudoers file – The Geek Diary
- Sudo – ArchWiki
- How to Give All Permissions in Ubuntu – Small Business – Chron.com
- How to run sudo command without a password on a Linux or Unix – nixCraft
- How to Use Sudo and the Sudoers File – Hostinger
- Re: sudo: /etc/sudoers is world writable – Ubuntu Forums
- etc/sudo.conf is world writable ; /usr/lib/sudo/sudoers … – Reddit
- sudo: no valid sudoers sources found, quitting – Super User
- sudo: /etc/sudoers.d is world writable – Red Hat Customer Portal
See more: nhanvietluanvan.com/luat-hoc