Deployment And Application Do Not Have Matching Security Zones.
Subheading 1: Understanding Security Zones in Deployment and Application
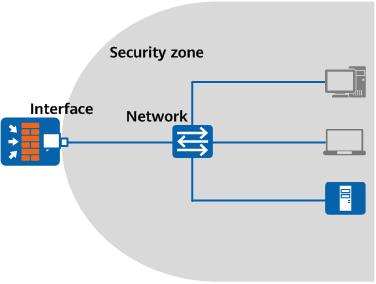
In the world of cybersecurity, security zones play a crucial role in ensuring the protection of sensitive data and systems. Security zones are virtual boundaries that segregate different parts of a network, application, or deployment, based on the level of trust and security controls required. These zones help organizations maintain the integrity, confidentiality, and availability of their resources by limiting access and controlling communication between different zones.
When it comes to deployment and application, security zones become even more critical. Deployment refers to the process of installing and configuring software or applications on a system, while application refers to the actual software or program that is being deployed. Both deployment and application should ideally be assigned to the same or matching security zone to ensure a consistent level of protection and to prevent potential security breaches.
Subheading 2: The Importance of Matching Security Zones
Matching security zones between deployment and application serve as a fundamental security best practice. It ensures that the security controls and policies that apply to a specific security zone are consistent across all levels of the deployment and application. Without matching security zones, organizations expose themselves to a range of security risks and vulnerabilities.
Subheading 3: Implications of Deployment and Application without Matching Security Zones
When deployment and application do not have matching security zones, organizations face a series of implications that can have severe consequences for their security posture. One of the primary implications is the inability to enforce uniform security controls throughout the entire deployment and application.
For example, if the deployment is configured with strict security controls in a high-security zone, but the application itself is assigned to a lower-security zone, attackers may be able to exploit vulnerabilities in the application to gain unauthorized access to sensitive data or systems. This mismatch in security zones undermines the overall security posture and weakens the organization’s ability to protect against potential threats.
Subheading 4: Risks and Vulnerabilities in Misaligned Security Zones
The misalignment of security zones in deployment and application exposes organizations to several risks and vulnerabilities. Some of these include:
1. Unauthorized access: When security zones are not aligned, it becomes easier for attackers to gain unauthorized access to sensitive resources. They can exploit vulnerabilities, bypass security controls, or impersonate legitimate users to gain entry into higher-security zones.
2. Data breaches: Misaligned security zones increase the likelihood of data breaches. For example, if an application with access to sensitive customer information is not assigned to the appropriate security zone, it could be compromised, leading to the exposure of sensitive data.
3. Malware propagation: If deployment and application are not in matching security zones, malware can spread more easily across the system or network. Once an attacker gains access through a vulnerable application, they can use it as a launching pad to infiltrate other areas of the system.
4. Integrity compromise: Without matching security zones, the integrity of the deployment and application can be compromised. Attackers can tamper with the application’s code or configurations, leading to functionality issues, unauthorized modifications, or even complete system compromise.
Subheading 5: Common Challenges in Establishing Matching Security Zones
Achieving matching security zones between deployment and application can present various challenges for organizations. Some common challenges include:
1. Lack of awareness: Many organizations underestimate the importance of matching security zones, leading to a lack of awareness about this best practice. Without understanding the risks involved, organizations may not prioritize aligning their security zones correctly.
2. Complex environments: In large and complex environments, organizations often struggle to identify and define appropriate security zones. Different applications and deployment scenarios may require different security controls, and mapping them accurately can be a daunting task.
3. Legacy systems and applications: Legacy systems and applications often pose challenges when it comes to aligning security zones. These older systems may have their unique security requirements or limitations, making it difficult to fit them into the organization’s overall security framework.
4. Lack of coordination: Proper coordination between the deployment and application teams is essential to ensure matching security zones. Miscommunication or lack of collaboration can result in misalignment and create security gaps.
Subheading 6: Best Practices for Ensuring Matching Security Zones
To establish matching security zones in deployment and application, organizations should follow these best practices:
1. Conduct a thorough risk assessment: Start by assessing the risks associated with each deployment and application scenario. Identify the assets, the sensitivity of the data, and the potential impact of a security breach. This assessment will guide the establishment of appropriate security zones.
2. Define and document security zone requirements: Clearly define the security requirements for each deployment and application scenario. Specify the security controls, access privileges, and communication pathways that should be allowed or restricted.
3. Standardize security zone frameworks: Establish a standardized framework for security zones within the organization. This framework should be based on industry best practices and align with regulatory requirements.
4. Implement access controls and segmentation: Implement access controls and network segmentation measures that enforce the defined security zones. Use firewalls, virtual private networks (VPNs), or other security measures to restrict communication between zones and enforce separation.
Subheading 7: Technologies and Tools for Securing Matching Security Zones
Several technologies and tools are available to help organizations secure matching security zones. These include:
1. Firewall solutions: Firewalls play a crucial role in enforcing access control policies and segmenting the network into separate security zones. Organizations should invest in robust firewall solutions capable of granular traffic filtering and rule enforcement.
2. Intrusion Detection and Prevention Systems (IDPS): IDPS solutions help identify and prevent potential attacks or unauthorized access attempts between different security zones. They monitor network traffic and raise alarms or take proactive measures to mitigate threats.
3. Security Information and Event Management (SIEM) systems: SIEM systems collect and analyze security event data from various sources, providing organizations with a centralized view of their security posture. They help detect and respond to misaligned security zones or suspicious activities.
4. Vulnerability scanners: Regularly scanning for vulnerabilities in both the deployment and application can help identify any misalignments or weaknesses. By addressing these vulnerabilities promptly, organizations can minimize the chances of security breaches.
Subheading 8: The Role of Training and Awareness in Achieving Matching Security Zones
Training and awareness play a crucial role in achieving and maintaining matching security zones. Organizations should invest in training programs to educate their employees about the importance of security zones and their role in maintaining a robust security posture.
FAQs:
Q1: What is the significance of matching security zones in deployment and application?
A1: Matching security zones ensure consistent security controls and policies throughout the entire deployment and application, minimizing the risk of unauthorized access and data breaches.
Q2: Can misaligned security zones lead to compromised system integrity?
A2: Yes, misaligned security zones can compromise the integrity of the deployment and application, allowing attackers to tamper with code or configurations.
Q3: What challenges do organizations face when establishing matching security zones?
A3: Common challenges include lack of awareness, complexity in large environments, limitations of legacy systems, and lack of coordination between teams.
Q4: How can organizations ensure matching security zones in deployment and application?
A4: Organizations can follow best practices such as conducting risk assessments, defining security zone requirements, standardizing frameworks, and implementing access controls and segmentation.
Q5: What technologies and tools can aid in securing matching security zones?
A5: Firewall solutions, IDPS systems, SIEM systems, and vulnerability scanners are some of the technologies and tools organizations can leverage to secure matching security zones.
In conclusion, matching security zones between deployment and application are vital for maintaining a robust security posture. Organizations must understand the risks and implications of misaligned security zones and implement best practices, technologies, and training programs to ensure a consistent level of protection. By prioritizing matching security zones, organizations can minimize the potential for security breaches and protect their valuable assets and data from unauthorized access or compromise.
Deployment And Application Do Not Have Matching Security Zones (2 Solutions!!)
What Are The Security Zones In Windows 10?
When it comes to protecting your computer and data, it is crucial to understand the concept of security zones in Windows 10. These security zones define the level of trust a user has for a particular website or network location. By categorizing websites and network resources into different security zones, Windows 10 provides varying levels of protection and privacy based on the user’s trust level. In this article, we will delve into the details of security zones in Windows 10, explaining what they are, how they work, and why they are essential for maintaining a secure computing environment.
Understanding Security Zones:
Security zones in Windows 10 refer to predefined groups of websites or network locations that share similar levels of trust. Microsoft defines four security zones: Internet, Local intranet, Trusted sites, and Restricted sites.
1. Internet Zone:
The Internet zone comprises all websites that are accessed through the Internet. By default, this zone has the highest security settings, intended to protect users from potentially harmful content and malicious attacks. Windows 10 automatically assigns this security zone to all websites not categorized in the other specified zones.
2. Local Intranet Zone:
The Local intranet zone is designated for websites or network resources within a user’s local network. This includes resources such as internal company websites, file shares, and other network-based services. By default, the Local intranet zone has lower security settings, accommodating trusted internal resources.
3. Trusted Sites Zone:
The Trusted sites zone allows users to specify their own list of trusted websites. These websites are considered safe and have fewer security restrictions. Users often add trusted websites that they frequently visit, such as online banking portals or other reputable sites, to this zone. The Trusted sites zone offers a balance between security and usability.
4. Restricted Sites Zone:
The Restricted sites zone is the opposite of the Trusted sites zone. It is used to specify websites or network locations that are considered untrustworthy or potentially harmful. The Restricted sites zone has the highest security settings, actively blocking and warning users about suspicious or malicious content.
How Security Zones Work:
When a user visits a website or accesses a network resource, Windows 10 checks the security zone assignment for that destination. Based on the respective security zone, the operating system applies the corresponding security settings and restrictions. These security settings define actions such as allowing or blocking downloads, enabling Scripting or ActiveX controls, and prompting for user consent before certain actions occur.
Each security zone is associated with a set of default security settings that can be modified by the user or an administrator. These settings determine the overall trust level and behavior of websites or network resources within the respective zone. For example, in the Internet zone, the default security settings are designed to protect users from potentially unsafe content, limiting certain functionality to prevent unauthorized access or malicious activities.
Why Security Zones are Important:
Security zones play a vital role in maintaining a secure computing environment. By categorizing websites and network resources into different zones, Windows 10 offers a balanced approach to security, allowing users to access trusted resources while mitigating the risks of accessing potentially harmful content.
Security zones also provide a clear visual indication of a website’s trustworthiness through Internet Explorer’s security bar. This bar, visible at the top of each webpage, displays the zone icon and can provide additional information about the website’s security status.
FAQs:
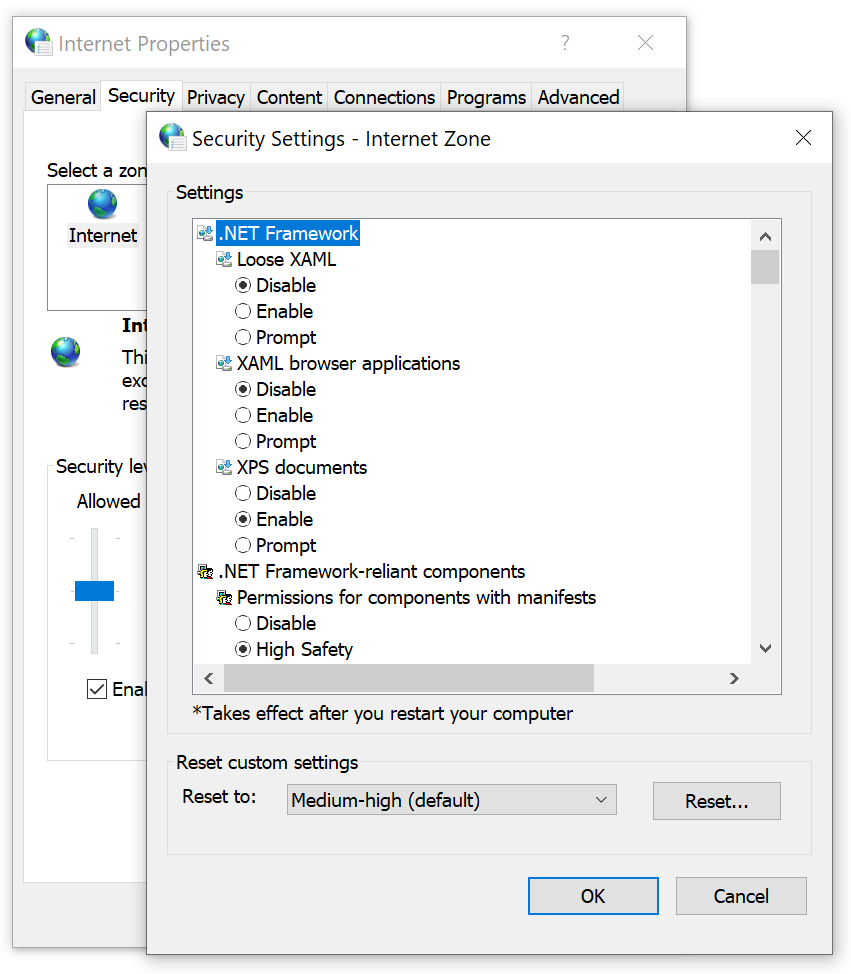
Q: Can I customize the security settings for each security zone?
A: Yes, users and administrators can modify the default security settings for each security zone based on their specific requirements. However, it is important to strike a balance between security and usability when customizing these settings.
Q: How do I add a website to the Trusted sites zone?
A: To add a website to the Trusted sites zone, open Internet Explorer, go to Internet Options, select the Security tab, and click on Trusted sites. From there, you can manually enter the website’s URL and add it to the list.
Q: How can I check the security zone of a website I’m visiting?
A: In Internet Explorer, you can check the security zone of a website by looking at the security bar at the top of the webpage. It will display the icon representing the respective security zone.
Q: Are security zones only applicable to Internet Explorer?
A: While security zones were primarily designed for Internet Explorer, many of the underlying principles and concepts are also applicable to other web browsers in Windows 10.
In conclusion, understanding security zones in Windows 10 is crucial for maintaining a secure computing environment. By categorizing websites and network resources into different zones, Windows 10 offers varying levels of trust and protection, allowing users to access reliable resources while minimizing the risks of potential threats. It is essential to be aware of these security zones and their associated settings to ensure a safe online experience.
What Are The Security Zones In Internet Explorer?
Internet Explorer, the web browser developed by Microsoft, includes a feature called “security zones” that helps protect users from potential online threats. These security zones classify websites into different categories based on their trustworthiness and assign different levels of security settings to each zone. By doing so, Internet Explorer ensures a safer browsing experience for its users.
The security zones in Internet Explorer are divided into five categories:
1. Internet Zone: This zone includes all websites on the Internet that are not explicitly assigned to other zones. By default, websites in this zone have medium security settings. Internet Zone is designed to handle websites that are not explicitly listed in any other zone.
2. Local Intranet Zone: Local Intranet Zone includes websites hosted within a local network or corporate intranet. Since these websites typically have a higher level of trust, Internet Explorer assigns a lower level of security settings to this zone by default. This allows users to access local resources more seamlessly while providing a reasonable level of security.
3. Trusted Sites Zone: Trusted Sites Zone consists of websites that users consider trustworthy and safe. By adding websites to this zone, users can lower the security settings further, allowing more functionality on trustworthy sites. This zone is often used for internal tools or web applications that users want to explicitly trust.
4. Restricted Sites Zone: Restricted Sites Zone is the opposite of Trusted Sites Zone. Websites added to this zone are considered untrusted and potentially harmful. By default, websites in this zone have very high security settings, which can help protect users from malicious content. This zone is used to block access to websites that may contain harmful content or suspicious activities.
5. Custom Security Zones: Apart from the four default zones, Internet Explorer also allows users to create and customize their own security zones. This can be useful for specific scenarios where users may want to define specific security settings for particular websites or group of websites. For instance, users can create a custom zone for websites related to online banking and set stricter security settings for additional protection.
FAQs:
Q: How can I view and modify the security zone settings in Internet Explorer?
A: To manage security zone settings in Internet Explorer, go to the “Internet Options” menu in the browser. From there, navigate to the “Security” tab and click on “Custom level.” Here, you can view and adjust the security settings for each zone.
Q: Should I add all websites to the Trusted Sites Zone?
A: No, it is not recommended to add all websites to the Trusted Sites Zone. Adding websites to this zone lowers the security settings, which can leave your system vulnerable to potential threats. Reserve the Trusted Sites Zone for websites that you trust explicitly.
Q: Can the security zone settings be applied to other web browsers?
A: No, the security zone settings in Internet Explorer are specific to that browser and do not apply to other web browsers, such as Chrome, Firefox, or Safari.
Q: Are the security zone settings enough to protect my computer from all online threats?
A: While the security zone settings in Internet Explorer provide a layer of protection, they are not a foolproof solution. It is always essential to keep your browser and operating system up to date, use a reliable antivirus software, exercise caution while browsing, and be wary of clicking on suspicious links or downloading unknown files.
Q: Can websites change their security zone classification?
A: No, website owners do not have control over the security zone classification assigned to their sites. However, they can follow best practices for web security to ensure that their websites are not flagged as potentially harmful sites.
In conclusion, the security zones in Internet Explorer play a crucial role in protecting users from online threats. By assigning different security settings to websites based on their trustworthiness, Internet Explorer helps ensure a safer browsing experience. Users can view and adjust the security zone settings as necessary but should exercise caution and only add websites to the Trusted Sites Zone when they explicitly trust them. Remember, while security zones offer protection, it is important to adopt additional security measures to safeguard your computer and personal information online.
Keywords searched by users: deployment and application do not have matching security zones. system.deployment.application.invaliddeploymentexception (zone), System Deployment application InvalidDeploymentException, the manifest for this application does not have a signature. signature validation will be ignored.
Categories: Top 24 Deployment And Application Do Not Have Matching Security Zones.
See more here: nhanvietluanvan.com
System.Deployment.Application.Invaliddeploymentexception (Zone)
Introduction (Word count: 100)
The system.deployment.application.invaliddeploymentexception (ZONE) is an error commonly encountered by developers and users working with .NET applications. In this article, we will delve into the details of this exception, its causes, effects, and provide potential solutions to help you overcome this issue.
Understanding the system.deployment.application.invaliddeploymentexception (ZONE) (Word count: 200)
The system.deployment.application.invaliddeploymentexception (ZONE) is an exception that occurs in the .NET framework’s ClickOnce deployment methodology. ClickOnce facilitates easy installation and updates of applications over the Internet. However, this exception is raised when there is a problem with the deployment, causing the application to crash or not load properly.
Causes of the system.deployment.application.invaliddeploymentexception (ZONE) (Word count: 250)
1. Corrupted or incomplete deployment manifests: The application’s manifest files may become corrupt or contain incomplete information, which can trigger the exception.
2. Incorrect application prerequisites: If the required prerequisite software components or frameworks are missing or incompatible, the exception may arise.
3. Mixed .NET framework versions: Different assemblies or components within the application may have been built targeting different versions of the .NET framework, causing compatibility conflicts.
4. Tampered deployment files: A user or external factor modifying the application’s installation files can lead to an invalid deployment exception.
5. Network-related issues: Problems with the user’s network connection, such as interruptions or slow connections, may interfere with the proper deployment of the application.
Effects of the system.deployment.application.invaliddeploymentexception (ZONE) (Word count: 200)
When this exception occurs, users may experience various issues:
1. Application crashes: The application may fail to start, freeze, or crash after displaying the exception.
2. Incorrect functionality: Users may encounter missing features or unexpected behavior due to improper deployment.
3. Inability to update or install applications: The exception may prevent users from installing or updating applications through the ClickOnce technology.
Solutions for the system.deployment.application.invaliddeploymentexception (ZONE) (Word count: 300)
1. Clear ClickOnce cache: Clearing the ClickOnce cache can remove any corrupt or incomplete files, forcing the application to re-download all necessary components.
2. Verify prerequisites: Ensure that the user’s system meets all required prerequisites for the application. If not, install or update the necessary components.
3. Check .NET framework versions: Review all assemblies and components within the application to ensure they are built against the same version of the .NET framework. Rebuilding the application may be necessary to ensure compatibility.
4. Ensure unaltered deployment files: Verify that the application’s deployment files have not been tampered with, ensuring the integrity of the deployment.
5. Stable network connection: Users should ensure a stable and uninterrupted network connection during the application deployment to prevent any issues.
Frequently Asked Questions (Word count: 120)
Q1. How can I clear the ClickOnce cache?
A1. To clear the ClickOnce cache, follow these steps:
– Open the “Run” dialog (Windows + R key)
– Type “%userprofile%\appdata\local\Apps\2.0” and press Enter
– Delete all the files and folders within this directory
Q2. Can I manually install prerequisites to avoid the exception?
A2. Yes, downloading and installing the required prerequisites manually can help to prevent the exception.
Q3. What if the solution provided does not resolve the issue?
A3. If the suggested solutions do not resolve the problem, you may need to seek further assistance from experienced developers or consult the application’s support resources.
Q4. Is the system.deployment.application.invaliddeploymentexception (ZONE) specific to ClickOnce deployments only?
A4. Yes, this exception arises exclusively within the context of ClickOnce deployments.
Conclusion (Word count: 100)
The system.deployment.application.invaliddeploymentexception (ZONE) error can hinder the smooth functioning of .NET applications deployed through the ClickOnce technology. By understanding the causes and implementing the provided solutions, developers and users can overcome this exception and ensure a successful deployment experience. Remember, resolving the issue may require experimenting with different solutions, depending on the specific circumstances of the deployment exception encountered.
System Deployment Application Invaliddeploymentexception
What is InvalidDeploymentException?
InvalidDeploymentException is an exception class that is part of the System.Deployment.Application namespace in .NET programming. It is thrown when an error occurs during the deployment of applications using ClickOnce technology. ClickOnce is a deployment technology that allows developers to create self-updating applications that are web-enabled. InvalidDeploymentException helps developers troubleshoot deployment issues and handle them gracefully.
Causes of InvalidDeploymentException
There can be several causes for the InvalidDeploymentException. Let’s discuss some of the common ones:
1. Corrupt or incomplete deployment package: If the ClickOnce deployment package is not created properly or gets corrupted during transfer, it can lead to InvalidDeploymentException. In such cases, re-creating and re-deploying the package usually resolves the issue.
2. Insufficient permissions: If the user does not have sufficient permissions to install or update applications, it can lead to deployment failures, resulting in an InvalidDeploymentException. This can occur when trying to install or update applications on restricted corporate or network environments.
3. Expired certificate: ClickOnce applications are signed with a digital certificate for authenticity. If the certificate used to sign the application expires, it can cause the InvalidDeploymentException. Developers need to ensure that their certificates are valid and up-to-date.
4. Incompatible framework version: If the target machine does not have the required version of .NET Framework installed, it can cause the InvalidDeploymentException. Developers should ensure that the application is compatible with the targeted framework version.
Handling InvalidDeploymentException
When encountering an InvalidDeploymentException, it is crucial to handle the exception gracefully to provide meaningful feedback to users and aid in troubleshooting. Here are some steps to handle InvalidDeploymentException:
1. Catch the exception: Surround the deployment code with a try-catch block and catch the InvalidDeploymentException. This allows you to capture the exception and handle it accordingly.
2. Display an error message: When the exception occurs, display an error message to the user indicating that the deployment failed. Provide clear instructions on how to resolve the issue, such as checking internet connectivity, updating permissions, or trying again later.
3. Log the exception details: Logging the exception details, such as the error message, stack trace, and deployment logs, can help in identifying the root cause of the deployment failure. This information can be used by developers or support teams for troubleshooting purposes.
4. Provide troubleshooting steps: If there are common reasons for the InvalidDeploymentException, include troubleshooting steps in your error message. This can help users resolve the issue without further assistance.
Frequently Asked Questions (FAQs)
Q1. How can I avoid InvalidDeploymentException?
To avoid InvalidDeploymentException, ensure that your deployment package is created correctly and transferred securely. Validate your certificates before signing the application. Also, verify that the target machine has the required .NET Framework version. Testing deployments in different environments can help catch potential issues early.
Q2. Why does InvalidDeploymentException occur only in ClickOnce applications?
InvalidDeploymentException is specific to ClickOnce applications because it is an error related to the deployment process handled by ClickOnce technology. Other deployment mechanisms, like traditional setups or MSI packages, might throw different exceptions or errors.
Q3. Can I customize the error message displayed to the user when InvalidDeploymentException occurs?
Yes, you can customize the error message displayed to the user. Catch the InvalidDeploymentException and then display a user-friendly error message that provides instructions on how to resolve the issue. Tailoring the error message can help users understand and troubleshoot the problem more effectively.
Q4. I have a valid certificate, but I still encounter InvalidDeploymentException. What could be the issue?
Although you have a valid certificate, ensure that the certificate is not revoked or expired. Check the certificate’s validity period and verify if it’s listed as revoked. If everything seems in order, double-check your deployment package and framework compatibility.
Q5. Can I automate the handling of InvalidDeploymentException?
Yes, you can automate the handling of InvalidDeploymentException, especially in scenarios where the error can be resolved programmatically. For example, you can automatically check and update permissions, or prompt the user to install the required .NET Framework version.
InvalidDeploymentException serves as a crucial component of ClickOnce technology, aiding in the successful deployment of applications. By understanding the causes of this exception and implementing proper handling strategies, developers can create robust and user-friendly deployment processes.
Images related to the topic deployment and application do not have matching security zones.

Found 9 images related to deployment and application do not have matching security zones. theme






Article link: deployment and application do not have matching security zones..
Learn more about the topic deployment and application do not have matching security zones..
- Deployment and Application Do Not … – Position Is Everything
- Deployment and Application do not have matching Security …
- How To Fix “Deployment And Application Do Not Have …
- Exchange hybrid configuration wizard with the error …
- Deployment and application do not have matching security …
- Fix Deployment and Application do not have Matching …
- Per-site configuration by policy | Microsoft Learn
- Change Internet Explorer Security settings – Microsoft
- Deployment and application do not have matching security …
- Error: Deployment and application do not have matching …
- Deployment and application do not have matching security …