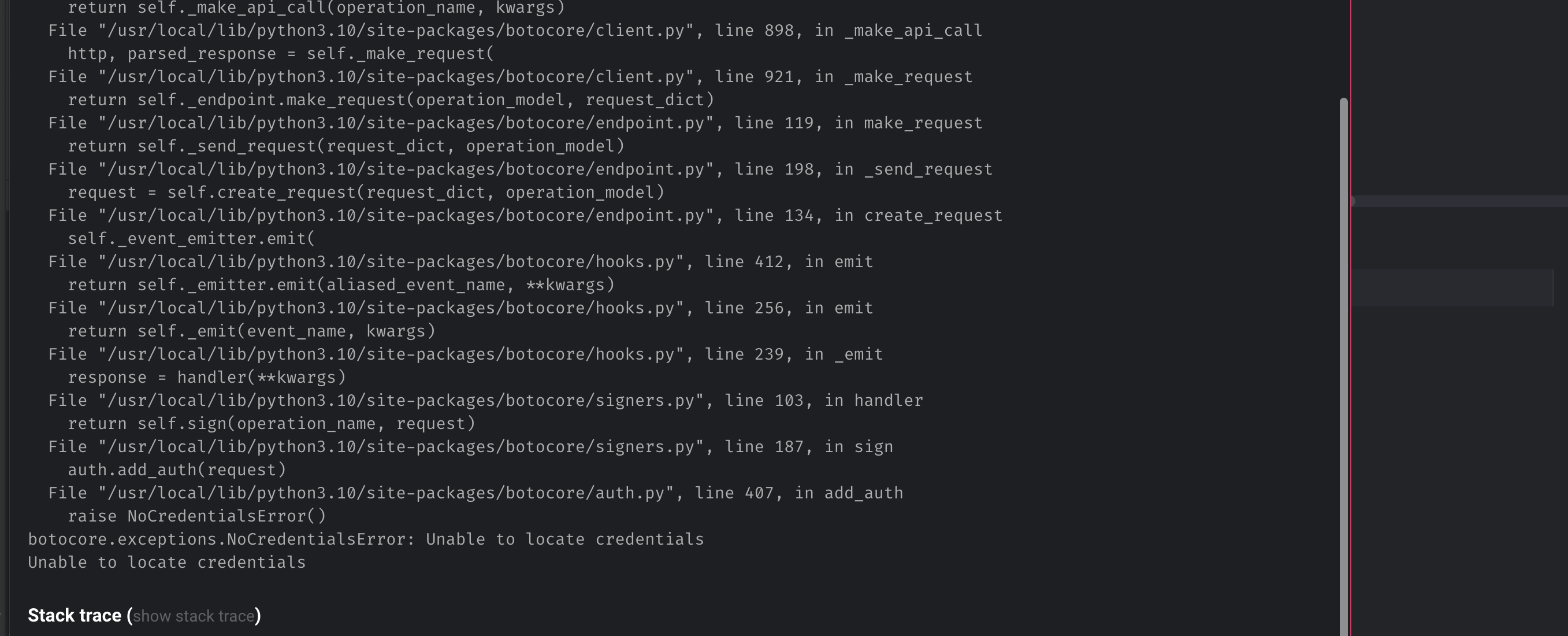
Botocore.Exceptions.Nocredentialserror Unable To Locate Credentials
Introduction:
The botocore.exceptions.nocredentialserror is a commonly encountered error in AWS (Amazon Web Services) when using the AWS SDK (Software Development Kit) in Python, specifically the boto3 library. This error occurs when the SDK is unable to locate the necessary credentials required for authentication and authorization to access AWS services. In this article, we will explore the causes of this error and discuss the troubleshooting steps to resolve it.
What is botocore.exceptions.nocredentialserror?
The botocore.exceptions.nocredentialserror is an exception raised by the botocore library, which is the core foundation for AWS SDKs in Python. This error signifies that the library was unable to find the necessary credentials required for making API calls to AWS services. Credentials are necessary to securely authenticate and authorize the user or application accessing AWS resources.
Causes of botocore.exceptions.nocredentialserror:
1. Incorrect AWS credentials: One of the most common causes of this error is using incorrect AWS credentials. This could be due to typos or mistakes made while entering the access key ID and secret access key.
2. AWS credentials not configured: If the AWS credentials are not configured on the system where the Python script is running, the SDK will not be able to locate the credentials. The credentials can be configured using the AWS CLI (Command Line Interface) or by setting environment variables.
3. Credentials not being passed correctly: When using the SDK, it is necessary to pass the credentials explicitly. If the credentials are not being passed correctly to the SDK, it will result in the “nocredentialserror”.
4. Expired or revoked credentials: AWS credentials have an expiration date. If the credentials being used have expired or have been revoked, the SDK will be unable to locate valid credentials. It is important to regularly check and renew credentials to avoid such issues.
5. Issues with IAM roles and policies: If the AWS account has an IAM role associated with it, the role needs to have the required permissions to access the AWS services being used. If there are any issues with the IAM role or its associated policies, it can result in the “nocredentialserror”.
6. Incorrect region configuration: AWS services are deployed in different regions around the world. If the SDK is configured with an incorrect region, it may result in the “nocredentialserror”. It is important to ensure that the region configuration matches the AWS services being used.
7. Network connectivity issues: If there are network connectivity issues between the system running the Python script and the AWS services, the SDK may fail to locate the necessary credentials. It is important to check the network connectivity and firewall settings to rule out any network-related issues.
8. Using an incompatible or outdated version of the AWS SDK: The botocore.exceptions.nocredentialserror could also arise if you are using an incompatible or outdated version of the AWS SDK. It is recommended to use the latest version of the AWS SDK to avoid compatibility issues and benefit from bug fixes and new features.
Troubleshooting botocore.exceptions.nocredentialserror:
To troubleshoot and resolve the botocore.exceptions.nocredentialserror, follow these steps:
1. Check AWS credentials and configuration: Double-check the AWS credentials (access key ID and secret access key) being used and ensure they are correct. Verify the configuration settings of the AWS SDK to ensure they match the AWS account being accessed.
2. Verify passed credentials and permissions: If you are passing credentials explicitly to the SDK, verify that they are being passed correctly without any typos. Also, check the permissions associated with the credentials to ensure they have the necessary permissions to access the required AWS services.
3. Ensure credentials are not expired or revoked: Regularly check the expiration date of the credentials being used. If they have expired, generate new credentials and update the SDK configuration accordingly. Similarly, if the credentials have been revoked or compromised, generate new credentials to ensure the security of your AWS resources.
4. Check IAM roles and policies: If IAM roles are being used, verify that the associated policies have the necessary permissions to access the required AWS services. Ensure that the IAM role is correctly configured and assigned to the AWS account being used.
5. Verify correct region configuration: Review the region configuration in the SDK and ensure that it matches the AWS services being accessed. If the region is incorrect, update it to the appropriate region.
6. Troubleshoot network connectivity issues: Check the network connectivity between the system running the Python script and AWS services. Ensure that the system has proper network access to the required IP addresses and ports used by AWS services. Verify firewall settings to rule out any network-related issues.
7. Upgrade to the latest version of the AWS SDK: If you are using an older version of the AWS SDK, consider upgrading to the latest version. The latest version may address any bugs or compatibility issues related to the “nocredentialserror”.
8. Consider using the AWS CLI for easier credentials management: The AWS CLI provides a simplified way to manage AWS credentials and configurations. Consider using the AWS CLI to configure and manage your credentials, which may reduce the chances of encountering the “nocredentialserror”.
In conclusion, the botocore.exceptions.nocredentialserror is a common error encountered when using the AWS SDK in Python. This article discussed the causes of this error, including incorrect credentials, expired or revoked credentials, incorrect region configuration, network connectivity issues, and more. It also provided troubleshooting steps to resolve the error, such as checking AWS credentials and configuration, verifying passed credentials and permissions, and upgrading to the latest version of the AWS SDK. By following these steps, you should be able to resolve the “nocredentialserror” and successfully access AWS services using the boto3 library.
FAQs:
Q: How can I install boto3 in Python 3?
A: Boto3 can be installed using the pip package manager by running the command “pip install boto3” in the terminal or command prompt.
Q: How do I configure AWS credentials?
A: AWS credentials can be configured by running the command “aws configure” in the terminal or command prompt after installing the AWS CLI. It will prompt you to enter the access key ID, secret access key, default region, and default output format.
Q: What are some common boto3 exceptions?
A: Apart from the “nocredentialserror”, some common boto3 exceptions include botocore.exceptions.clienterror, botocore.exceptions.connectionerror, botocore.exceptions.endpointconnectionerror, and botocore.exceptions.paramvalidationerror.
Q: How can I generate a presigned URL using boto3?
A: Boto3 provides the “generate_presigned_url” method, which allows you to generate a presigned URL for accessing private objects in Amazon S3. The method requires the “Bucket” name, “Key” (object key), and optional parameters like “ExpiresIn” (expiration time) and “HttpMethod” (HTTP method).
Q: What is S3boto?
A: S3boto is not a specific term or library related to AWS or boto3. It might be a typo or a misinterpretation. Please verify the correct term or context for further information.
Q: How can I set up credentials to resolve the awsbotocore.exceptions.nocredentialserror?
A: You can set up credentials by running the “aws configure” command with the AWS CLI. This will prompt you to enter the access key ID, secret access key, default region, and default output format, which will be used by the SDK to locate and authenticate with AWS services.
How To Setup Boto3 And Aws Credentials On Windows 10 | Aws Command Line Configuration | Aws Cli
Why Is Python S3 Unable To Locate Credentials?
Python is a widely used programming language due to its simplicity and versatility. It offers a vast array of libraries and packages that developers can use to enhance their applications. One such library is Boto3, which is the official Amazon Web Services (AWS) SDK for Python. Boto3 makes it easy to integrate AWS services into Python applications, including Amazon S3, which is an object storage service offered by AWS.
However, users sometimes encounter an issue where Python S3 is unable to locate credentials. This can be frustrating, especially if you have already set up your AWS credentials properly. Let’s take a closer look at some of the common reasons behind this problem and explore possible solutions.
1. Invalid or missing AWS credentials:
One of the main causes of Python S3 being unable to locate credentials is either having invalid or missing AWS credentials. You need to ensure that you have provided the correct credentials in your code or configuration. These credentials typically consist of an access key ID and a secret access key. You can generate these credentials in the AWS Management Console by creating an access key for an IAM user or by using an IAM role if your application is running on an EC2 instance.
2. Credential configuration issues:
Another potential reason for this issue is incorrect configuration of credentials. Boto3 looks for AWS credentials in various places, such as environment variables, shared configuration files, and instance profile credentials. If you have not set up the credentials correctly or have inconsistent configuration across these sources, Python S3 may fail to locate them. It is crucial to inspect the configuration settings and ensure that the credentials are properly set and accessible by your application.
3. Incorrect region configuration:
AWS services, including Amazon S3, are segregated by regions. When you make API requests, you must specify the correct AWS region where your S3 bucket is located. If you don’t set the region properly in your Python code or AWS configuration, it can result in Python S3 being unable to locate the required credentials. Verify that you have specified the correct region when interacting with S3 services.
4. Network connectivity issues:
Sometimes, the inability to locate credentials may not be a problem with the code or credentials themselves but rather a network connectivity issue. Ensure that your application has internet access and can reach the AWS service endpoints. Network connectivity problems can prevent Python S3 from accessing the AWS metadata service to retrieve the required credentials automatically.
FAQs:
Q1. How do I verify if my AWS credentials are valid?
To check the validity of your AWS credentials, you can use the AWS Command Line Interface (CLI) or the AWS SDKs and examine the response from an API call (e.g., listing buckets in S3). If the call succeeds, your credentials are valid; otherwise, you may need to generate new credentials or verify the existing ones.
Q2. Can I store AWS credentials in environment variables?
Yes, you can store AWS credentials in environment variables, such as `AWS_ACCESS_KEY_ID` and `AWS_SECRET_ACCESS_KEY`. Boto3 will automatically use these variables if they are set, making your code more secure by avoiding hardcoding credentials directly.
Q3. Can IAM roles be used instead of accessing credentials directly?
Yes, AWS Identity and Access Management (IAM) roles can be used to grant permissions to your applications without having to store and manage access keys. By assigning a role to your application (e.g., when running on an EC2 instance), it can automatically access the necessary AWS services without explicitly providing credentials.
Q4. What should I do if Python S3 still cannot locate credentials?
If you have followed the recommendations mentioned above and are still experiencing issues with credentials, it is essential to double-check that the correct AWS SDK and its version are installed. Additionally, ensure that the necessary IAM permissions are granted to the user or role associated with the credentials. AWS documentation and developer forums can provide further guidance on troubleshooting specific scenarios.
In conclusion, Python S3 being unable to locate credentials can be caused by various factors such as invalid or missing credentials, incorrect configuration, region mismatches, or network connectivity issues. By addressing these potential causes and following best practices for managing AWS credentials, you can ensure smooth integration of Python applications with Amazon S3 and other AWS services.
Why Is Download From S3 Unable To Locate Credentials?
Amazon S3 (Simple Storage Service) is a cloud-based storage service offered by Amazon Web Services (AWS). It allows individuals and organizations to store and retrieve data from anywhere on the web. However, sometimes users may encounter an issue where they are unable to locate their credentials when attempting to download files from S3. This article will explore the possible reasons behind this problem and provide solutions to resolve it.
1. Incorrectly configured credentials:
One of the most common reasons for being unable to locate credentials when downloading from S3 is misconfiguration. Users need to set up their AWS credentials correctly in order to access S3. To do this, they should configure their AWS access key ID and secret access key, along with optional session tokens, in a credential file or environment variables. If any of these values are missing or entered incorrectly, S3 will be unable to locate the credentials.
2. Lack of IAM permissions:
IAM (Identity and Access Management) is a service provided by AWS that allows users to manage access and permissions for their AWS resources. Insufficient IAM permissions can prevent S3 from locating the necessary credentials. Users should ensure that they have the required IAM permissions to access S3 buckets and download files. They can do this by checking their IAM policies and verifying that S3 access is granted.
3. Expired or revoked credentials:
AWS access keys have expiration periods for security purposes. If your access key has expired, S3 will be unable to locate those credentials. Additionally, if your access key has been revoked by the account owner or IAM administrator, you won’t be able to download from S3. To resolve this, generate a new access key and update your credentials accordingly.
4. Network connectivity issues:
Sometimes, network connectivity problems can lead to the inability to locate credentials when downloading from S3. Ensure that your internet connection is stable and try accessing other websites or services to confirm it is not a network issue. If other services work fine, consider reaching out to AWS support to investigate further.
5. Incorrect region or endpoint:
S3 is available in various regions across the globe, and each region has its own unique endpoint. If you are unable to locate credentials, double-check that you are using the correct region/endpoint. Making requests to the wrong region can result in a failure to authenticate and access S3.
FAQs:
Q: How do I configure AWS credentials for S3 access?
A: To configure AWS credentials, you can use the AWS CLI (Command Line Interface) or AWS Management Console. For the CLI, use the “aws configure” command and enter your access key ID, secret access key, default region, and output format. In the AWS Management Console, navigate to the IAM service, access the Users section, choose your user, and select the “Security credentials” tab to manage your access keys.
Q: Why am I still unable to locate credentials after setting them up correctly?
A: Double-check the configuration values, ensure that IAM policies have been properly set, and verify that the correct region/endpoint is being used. If the problem persists, try generating new access keys and update your credentials accordingly. If none of these steps work, consider reaching out to AWS support for further assistance.
Q: Can I download from S3 without credentials?
A: No, credentials are necessary to authenticate and access S3 resources. It ensures proper security measures are in place to protect your data. Without credentials, S3 will deny access to the requested files.
Q: What should I do if my AWS access key has expired?
A: Generate a new access key and update your credentials. This can be done in the IAM section of the AWS Management Console, where you can create a new access key for your user and remove the expired one. Then, update your local configuration with the new access key to continue accessing S3.
In conclusion, the inability to locate credentials when downloading from Amazon S3 can be caused by misconfigured or missing credentials, lack of IAM permissions, expired or revoked access keys, network connectivity issues, or using incorrect regions or endpoints. By ensuring that AWS credentials are correctly set up, IAM permissions are appropriate, and all values are valid, users can resolve this issue and successfully download files from S3.
Keywords searched by users: botocore.exceptions.nocredentialserror unable to locate credentials Install boto3 python3, AWS credentials, Unable to locate credentials you can configure credentials by running aws configure, Boto3, Boto3 exceptions, Generate_presigned_url boto3, S3boto, Setup credentials aws
Categories: Top 46 Botocore.Exceptions.Nocredentialserror Unable To Locate Credentials
See more here: nhanvietluanvan.com
Install Boto3 Python3
Boto3 is an Amazon Web Services (AWS) Software Development Kit (SDK) for Python, which allows developers to interact with AWS services programmatically. With Boto3, you can easily integrate your Python applications with various AWS services, such as EC2, S3, DynamoDB, and more. This article will guide you through the process of installing Boto3 for Python3 and provide answers to frequently asked questions (FAQs) about the installation process.
Installing Boto3 for Python3:
Before proceeding with the installation, ensure that you have Python3 and pip (Python package installer) installed on your system. Here’s a step-by-step guide to installing Boto3 for Python3:
1. Open your terminal or command prompt.
2. Run the following command to install Boto3:
“`
pip install boto3
“`
Ensure that you have a stable internet connection to download the required packages. The installation process might take a few moments.
3. Once the installation is complete, you can verify the installation by running the following command:
“`
python -c “import boto3”
“`
If there are no error messages, the installation was successful. You are now ready to use Boto3 in your Python projects!
Frequently Asked Questions (FAQs):
Q: Is Boto3 compatible with Python2?
A: Boto3 is designed to work with Python version 3 and above. It is not compatible with Python2.
Q: Can I use Boto3 without an AWS account?
A: While you can install Boto3 without an AWS account, you will need valid AWS credentials (access key and secret access key) to interact with AWS services programmatically.
Q: How do I configure AWS credentials for Boto3?
A: Boto3 relies on the AWS SDK for Python (known as Boto3) to read AWS credentials. The AWS SDK for Python checks for the presence of environment variables `AWS_ACCESS_KEY_ID` and `AWS_SECRET_ACCESS_KEY` for credentials. Alternatively, you can set up the AWS CLI (Command Line Interface) and use `aws configure` command to configure credentials.
Q: Are there any additional requirements for using Boto3?
A: Boto3 requires the `botocore` package, which is installed automatically when installing Boto3. Additionally, ensure that you have the necessary IAM roles and permissions to access the AWS services you intend to use.
Q: Which AWS services are supported by Boto3?
A: Boto3 supports a wide range of AWS services, including but not limited to:
– AWS Lambda
– Amazon S3
– Amazon EC2
– Amazon SQS
– Amazon DynamoDB
– Amazon RDS
– Amazon SNS
The complete list of supported services can be found in the Boto3 documentation.
Q: How can I upgrade Boto3 to the latest version?
A: You can upgrade Boto3 by running the following command:
“`
pip install –upgrade boto3
“`
This will install the latest available version of Boto3.
Q: Can Boto3 be used with other programming languages?
A: Boto3 is specifically designed for Python, and there are no official versions available for other programming languages. However, AWS provides SDKs for various other languages, such as JavaScript, Java, Ruby, and more.
Q: How do I get started with Boto3?
A: To get started with Boto3, you can refer to the official Boto3 documentation, which provides comprehensive guides, examples, and API references. The documentation covers various aspects of working with AWS services using Boto3.
In conclusion, installing Boto3 for Python3 is a straightforward process that allows developers to integrate their Python applications seamlessly with Amazon Web Services. By following the step-by-step guide provided in this article, you can quickly set up Boto3 and leverage its capabilities to interact with a multitude of AWS services. Remember to review the FAQs section for answers to common questions about Boto3 installation. Happy coding with Boto3 and AWS!
Aws Credentials
In the world of cloud computing, security remains a top concern for organizations. With the rise in cyber threats, it has become increasingly important to protect sensitive data stored in the cloud. Amazon Web Services (AWS), the leading cloud service provider, takes security seriously and offers robust measures to safeguard customer resources. One crucial aspect of securing your AWS environment is managing the credentials used to access your cloud resources. In this article, we will dive deep into AWS credentials, understanding their significance, types, best practices, and frequently asked questions.
Understanding AWS Credentials:
AWS credentials are essential for authenticating and authorizing access to AWS services and resources. They are used to validate the identity of users, applications, and other entities that interact with AWS services. Without proper credentials, unauthorized access to your cloud resources may occur, potentially leading to data breaches or unauthorized modifications.
Types of AWS Credentials:
AWS offers multiple types of credentials to suit different use cases and environments:
1. Access Key ID/Secret Access Key: This is the most common type of AWS credentials. Access Key ID and Secret Access Key are long-term credentials used to access AWS services via APIs, command-line tools, and SDKs. It is important to keep these credentials secure, as anyone with access to them can perform actions on your behalf.
2. X.509 Certificates: X.509 certificates are used for secure communication over SSL/TLS protocols. They are typically used with AWS Identity and Access Management (IAM) roles to establish secure connections between resources.
3. IAM Roles: IAM roles provide a secure way to delegate permissions to entities within your AWS account. Roles are associated with specific permissions, making it easier to manage access control and reducing the need for static credentials like access keys.
Best Practices for Managing AWS Credentials:
To ensure the secure management of your AWS credentials, follow these best practices:
1. Use AWS Identity and Access Management (IAM): IAM allows you to manage access to AWS resources securely. Create individual IAM user accounts for each person or entity that requires access, enabling you to assign permissions and enforce security policies.
2. Enable Multi-Factor Authentication (MFA): Enabling MFA adds an extra layer of security to AWS accounts. It requires users to provide a unique authentication code, typically generated by a mobile app or hardware device, in addition to their password.
3. Regularly Rotate Access Keys: Routinely rotate access keys for your IAM users to reduce the risk of unauthorized access. AWS provides options for automatic access key rotation, simplifying the process.
4. Follow the Principle of Least Privilege: Grant users and applications only the permissions necessary to perform their required tasks. Avoid granting overly broad permissions that may increase the risk of accidental or intentional misuse.
5. Securely Store Access Keys: Store access keys securely, using services like AWS Secrets Manager or AWS Key Management Service (KMS). Avoid hard-coding keys into applications, scripts, or source code repositories.
FAQs:
Q1: What is the difference between IAM users and IAM roles?
A: IAM users represent individuals or entities, while IAM roles are authentication and authorization mechanisms used to delegate permissions to entities within your AWS account. IAM roles are often used to grant temporary access to external entities or services.
Q2: Can I use IAM roles with EC2 instances?
A: Yes, you can assign IAM roles to EC2 instances during launch or later. IAM roles attached to EC2 instances provide secure access to other AWS services without the need for explicit access keys or credentials.
Q3: Can I restrict access to specific AWS resources with IAM?
A: Yes, IAM allows you to define fine-grained access control policies, restricting access to specific AWS resources, services, or actions.
Q4: Can I track API calls made using AWS credentials?
A: Yes, AWS CloudTrail provides a comprehensive audit trail of API calls made within an AWS account. It records details such as the identity of the caller, time, source IP, and actions performed.
Q5: How can I mitigate the risk of unauthorized access to my AWS resources?
A: Implementing the best practices mentioned earlier, such as using IAM, enabling MFA, regularly rotating access keys, and following the principle of least privilege, can significantly reduce the risk of unauthorized access.
In conclusion, AWS credentials play a vital role in ensuring the security of your cloud resources. By implementing secure practices and necessary precautions, organizations can minimize the risk of unauthorized access, data breaches, or potential misuse. Following AWS’s best practices and utilizing the provided security tools and services help maintain a robust security posture, allowing businesses to leverage the full potential of the AWS cloud securely.
Images related to the topic botocore.exceptions.nocredentialserror unable to locate credentials

Found 41 images related to botocore.exceptions.nocredentialserror unable to locate credentials theme



Article link: botocore.exceptions.nocredentialserror unable to locate credentials.
Learn more about the topic botocore.exceptions.nocredentialserror unable to locate credentials.
- Boto3 Error: botocore.exceptions.NoCredentialsError: Unable …
- Resolving the Boto3 NoCredentialsError in Python – Rollbar
- Botocore.Exceptions.NoCredentialsError: Unable to Locate …
- How to Fix botocore.exceptions.NoCredentialsError: Unable to …
- Resolve “Unable to locate credentials” error in Amazon S3
- AWS CLI Unable To Locate Credentials | A Quick Fix – Bobcares
- fatal error: unable to locate credentials – AI Search Based Chat – You.com
- Python, Boto3, and AWS S3: Demystified
- unable to locate credentials – AI Search Based Chat – You.com
- dynamodb botocore.exceptions.nocredentialserror unable to …