This Combination Of Host And Port Requires Tls
[Solved] How To Fix Tls Error Problem (100% Working)
What Does This Combination Of Host And Port Requires Tls Mean?
When it comes to internet communication, security is of paramount importance. The use of Transport Layer Security (TLS) has become an essential requirement to ensure the encryption and integrity of data transmitted between client and server. In some cases, you may come across a specific combination of host and port that requires TLS. This article aims to explain the concept of TLS, how it works, and why certain combinations may require it.
Understanding Transport Layer Security (TLS)
Transport Layer Security (TLS) is a protocol that provides secure communication over the internet. It is an upgraded version of the Secure Sockets Layer (SSL), which became obsolete due to security vulnerabilities. TLS establishes an encrypted connection between a client (for example, a web browser) and a server (such as a website). This encryption prevents unauthorized users from intercepting and tampering with the data transmitted between the two parties.
TLS operates on the Transport Layer of the internet protocol suite, ensuring data integrity, confidentiality, and authenticity. It achieves this by using a combination of symmetric and asymmetric encryption algorithms, digital certificates, and secure key exchange mechanisms.
The Importance of TLS in Web Communication
In the context of web communication, TLS is commonly used to protect sensitive data, such as login credentials, personal information, and financial transactions. It ensures that data is securely transmitted over the internet and remains confidential.
When you visit a website that requires TLS, your web browser and the server negotiate a secure connection. This negotiation involves the exchange of digital certificates issued by trusted certificate authorities. These certificates verify the authenticity of the server, guaranteeing that you are connecting to the intended website and not a fraudulent one.
Combination of Host and Port That Requires TLS
Not all web connections require TLS. However, certain combinations of host and port do mandate the use of this protocol. For instance, when connecting to a secure website, commonly identified by URLs starting with “https://” rather than “http://,” a specific combination of host (domain name) and port (a numerical value) must be configured to require TLS.
The most common port for secure web communication is 443. When a website specifies its URL as “https://example.com:443,” it indicates that the server expects a TLS-secured connection on port 443. It’s important to note that browsers typically default to port 443 for HTTPS connections, so you don’t need to explicitly include it in the URL.
Other combinations of host and port may also require TLS, depending on the specific application or service. For example, email servers usually require encrypted connections on port 465 or 587, whereas secure file transfer may utilize port 22 (SSH) or port 990 (FTPS).
TLS Frequently Asked Questions (FAQs)
Q: What happens if I try to connect to a host and port without TLS when it is required?
A: If TLS is required, attempting to connect without it would typically result in an error or a connection refusal.
Q: How can I tell if a website or service requires TLS?
A: Websites that require TLS typically have URLs starting with “https://” instead of “http://”. Additionally, specific ports, such as 443 for HTTPS, are commonly associated with secure connections. However, it’s always best to refer to the website or service documentation for any specific requirements.
Q: What are the advantages of using TLS?
A: TLS ensures the encryption of data during transmission, preventing unauthorized users from intercepting and understanding the information being exchanged. It also verifies the authenticity of the server, reducing the risk of connecting to malicious websites or servers.
Q: Does TLS completely guarantee the security of my data?
A: While TLS provides a strong level of encryption and authentication, it is not an absolute guarantee. Other security measures, such as secure coding practices on websites and regularly updating software, are also essential for maintaining overall data security.
Q: Can I disable TLS on my web browser?
A: It is generally not recommended to disable TLS on your web browser, as it would prevent you from accessing websites that require secure connections. It is crucial to keep TLS enabled to ensure safe browsing and protection of your data.
Conclusion
The combination of host and port requiring TLS indicates a specific configuration that ensures secure connections on the internet. TLS plays a vital role in protecting sensitive data during transmission, ensuring its confidentiality and integrity. By using TLS, you can have peace of mind knowing that your online communication remains private and secure.
What Requires Tls?
Transport Layer Security (TLS) is a protocol that ensures secure communication between two devices over a network, commonly the internet. With the increasing prevalence of cyber threats and data breaches, employing TLS has become vital to protect sensitive information. It encrypts data, verifies the authenticity of the communicating parties, and ensures the integrity of the transmitted data. This article will explore what requires TLS, highlighting its significance across various industries and services.
1. E-commerce:
TLS is a crucial component for e-commerce websites as it secures the transmission of personal and financial information during online transactions. Any website that collects credit card details or asks for personal information like addresses, names, or phone numbers must implement TLS to safeguard users’ data. Without TLS, these websites are vulnerable to interception and malicious attacks.
2. Financial institutions:
Banks, investment firms, and other financial institutions handle massive amounts of sensitive data on a daily basis. With regulations such as the Payment Card Industry Data Security Standard (PCI DSS), these entities are required to use TLS for secure data transfer. TLS helps protect account information, transaction details, and other critical financial data from being compromised by hackers.
3. Healthcare:
In the healthcare industry, securing patient data is paramount. Medical records, lab results, and personal health information must be protected to ensure patient privacy and comply with regulations like HIPAA (Health Insurance Portability and Accountability Act). TLS plays a significant role in safeguarding these important records during transmission from one healthcare provider to another.
4. Messaging and email:
With the increasing dependence on email for professional and personal communication, secure email transmission has become crucial. Encryption is necessary to protect emails from unauthorized access. TLS is employed in email servers to ensure secure communication between sender and recipient, preventing eavesdropping or tampering of sensitive emails.
5. Cloud services:
Cloud storage and computing have gained immense popularity, with businesses of all sizes relying on them for data storage and processing. TLS is required to maintain the security and privacy of data while it is being transferred or stored in the cloud. It prevents unauthorized access and ensures that data remains confidential throughout its lifecycle in the cloud environment.
6. Government and public sectors:
Government agencies and public sectors handle sensitive information, including citizen data, defense-related data, and classified information. TLS is mandatory to protect this data from unauthorized access and online threats. By utilizing TLS, governments can ensure the integrity and confidentiality of both citizen and national security information.
7. Social media and networking platforms:
With billions of users worldwide, social media platforms like Facebook, Twitter, and Instagram must ensure secure communication between users. TLS is used to secure login credentials, protect users’ private messages, and prevent unauthorized access to their personal information. Ensuring trust and privacy on these platforms is crucial in maintaining user confidence.
8. Online forms and authentication:
Whenever you fill out an online form requesting personal information, such as registration forms or surveys, TLS is necessary to keep your data secure. TLS encrypts the data during transmission, ensuring that it cannot be intercepted and accessed by malicious individuals. Similarly, authentication systems that require usernames and passwords also rely on TLS to securely transfer login credentials and protect user accounts from unauthorized access.
FAQs:
1. Is TLS the same as SSL?
TLS evolved from the Secure Sockets Layer (SSL) technology. While they serve the same purpose of securing data transmission, TLS is considered more secure and advanced. TLS should be preferred over SSL as it includes stronger encryption algorithms and improved authentication mechanisms.
2. Does TLS guarantee 100% security?
While TLS provides robust security measures, it is not immune to vulnerabilities or flaws. Implementation errors, outdated protocols, or compromised certificates can weaken the security provided by TLS. Regular updates and adherence to best practices are necessary to mitigate potential risks.
3. How can I check if a website is using TLS?
You can check if a website is using TLS by verifying the presence of a padlock icon in the browser’s address bar. Additionally, websites using TLS often have URLs starting with “https://” instead of “http://” – the extra “s” denotes a secure connection.
4. Can TLS protect against all cyber threats?
TLS primarily focuses on securing data during transmission, ensuring privacy and integrity. It does not provide comprehensive protection against all cyber threats, such as malware or phishing attacks. It is crucial to utilize additional security measures, such as firewalls, antivirus software, and user education, to enhance overall cybersecurity.
In conclusion, TLS is a critical component in ensuring secure communication and protecting sensitive data across various industries and services. From e-commerce to healthcare and government sectors, TLS helps safeguard personal, financial, and classified information from unauthorized access and cyber threats. Adopting TLS is essential for organizations and individuals alike to create a secure online environment and maintain data privacy.
Keywords searched by users: this combination of host and port requires tls bad request this combination of host and port requires tls. manageengine, TLS Spring Boot, Config SSL Tomcat 9, Install SSL ServiceDesk Plus, Spring Boot support both HTTP and HTTPS
Categories: Top 76 This Combination Of Host And Port Requires Tls
See more here: nhanvietluanvan.com
Bad Request This Combination Of Host And Port Requires Tls. Manageengine
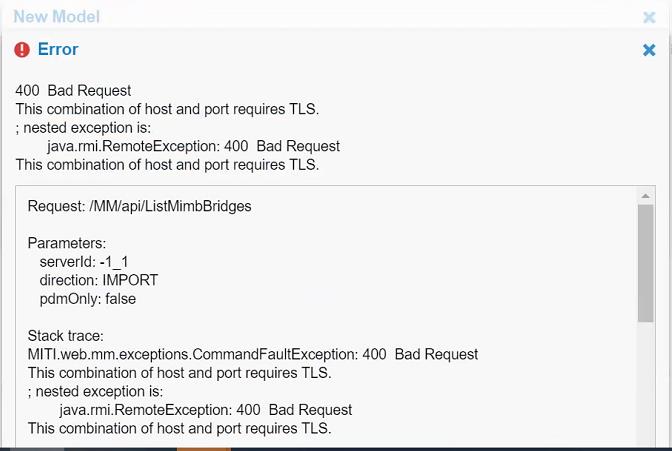
In today’s technologically advanced world, data security is of utmost importance. As companies and organizations strive to protect sensitive information from threats and attacks, implementing secure protocols such as TLS (Transport Layer Security) has become crucial. However, occasionally, users may encounter a frustrating error message that states “Bad Request: This Combination of Host and Port Requires TLS.” In this article, we will delve deeper into this error message and understand its implications, possible causes, and steps to resolve it.
Understanding the Error Message:
The error message “Bad Request: This Combination of Host and Port Requires TLS” is commonly seen when attempting to access a website or a web application. It means that the host and port combination used to access the resource requires a secure connection using TLS. If the user tries to establish a non-secure connection (HTTP) instead of a secure connection (HTTPS), the server will reject the request and display this error message.
Possible Causes of the Error:
1. SSL/TLS Misconfiguration: The error might occur due to an SSL/TLS misconfiguration on the server side. This misconfiguration may prevent the server from accepting non-secure connections or force the use of secure connections for specific host and port combinations.
2. Browser Settings: The error might also be due to the browser settings blocking non-secure connections or being configured to prefer secure connections. In such cases, the browser will automatically attempt to establish a secure connection (HTTPS), but if the server requires a non-secure connection (HTTP), the error message will be displayed.
Steps to Resolve the Error:
1. Verify the URL: Ensure that the URL entered is correct and doesn’t include any typographical errors. Pay attention to the protocol (HTTP vs. HTTPS) specified in the URL. If the error occurs when accessing a specific website, it is advisable to double-check the website’s URL and try accessing it again.
2. Try HTTPS instead of HTTP: If you are using HTTP in the URL, try replacing it with HTTPS. This change forces the browser to establish a secure connection, which may resolve the error if the resource requires TLS.
3. Clear Browser Cache and Cookies: Sometimes, caching issues can interfere with the connection. Clearing the browser’s cache and cookies can help eliminate any conflicts, enabling successful access to the resource requiring TLS.
4. Check Browser Settings: In certain cases, browser settings may be configured to prefer secure connections or block non-secure connections. Check your browser settings to ensure that it allows both secure (HTTPS) and non-secure (HTTP) connections.
5. Disable Browser Extensions: Some browser extensions might interfere with the connection and prevent the establishment of a secure connection. Temporarily disabling the browser extensions or trying to access the resource in an incognito window can help identify if any extensions are causing the error.
FAQs:
Q1. Why am I seeing the “Bad Request: This Combination of Host and Port Requires TLS” error message?
A1. This error message occurs when a server requires a secure connection (HTTPS) for a specific host and port combination but receives a non-secure connection request (HTTP) instead.
Q2. Can I bypass the requirement for TLS to access the resource?
A2. Bypassing the requirement for TLS might compromise the security of the resource. It is essential to ensure that the connection is secure (HTTPS) when accessing sensitive information or when the server mandates a secure connection.
Q3. Why would a server require TLS for specific host and port combinations?
A3. Requiring a secure connection for specific host and port combinations enhances data security. It ensures that sensitive information transmitted between the client and server is encrypted and protected from unauthorized access.
Q4. What should I do if the error persists despite following the resolution steps?
A4. If the error continues after following the steps mentioned above, contact the website or application administrator for further assistance. They may be able to provide specific instructions or insights into the issue.
In conclusion, the “Bad Request: This Combination of Host and Port Requires TLS” error message signifies the server’s requirement for a secure connection using TLS for a specific host and port combination. By understanding the causes of this error and following the resolution steps, users can overcome the issue and ensure the secure transmission of sensitive information online. Remember, maintaining data security should always be a top priority in today’s increasingly connected world.
Tls Spring Boot
TLS in Spring Boot:
Spring Boot provides a comprehensive set of features to enable TLS in applications. It integrates with the underlying Java security infrastructure to handle the complexities of TLS encryption and decryption. With Spring Boot, developers can easily configure TLS settings using properties, annotations, or programmatically.
To enable TLS in a Spring Boot application, the first step is to obtain a certificate from a trusted certificate authority (CA) or generate a self-signed certificate. A certificate contains information about the identity of the server and is used to establish a secure connection with clients. Once the certificate is obtained, it needs to be configured in the Spring Boot application.
Spring Boot allows developers to configure TLS settings using properties defined in the application.properties or application.yml file. For example, to configure the server to use TLS, the following properties can be set:
“`
server.ssl.enabled=true
server.ssl.key-store-type=PKCS12
server.ssl.key-store=classpath:keystore.p12
server.ssl.key-store-password=password
“`
In this example, the server.ssl.enabled property is set to true to enable TLS. The server.ssl.key-store-type property specifies the type of keystore (PKCS12 in this case), and the server.ssl.key-store property specifies the path to the keystore file. The server.ssl.key-store-password property specifies the password to access the keystore.
Apart from configuring TLS settings using properties, Spring Boot also provides annotations and programmatic options. Developers can use the @EnableEncryptableProperties annotation to enable encryption of properties using a configured key store. They can also use the SslStoreProvider interface to programmatically specify the keystore and truststore used for TLS.
Spring Boot also offers support for mutual TLS (mTLS), where both the server and the client authenticate each other using certificates. In mTLS, the server presents its certificate to the client, and the client also presents its certificate to the server. This provides an extra layer of security in ensuring the identity of both parties.
To enable mTLS in Spring Boot, the server needs to be configured to request client certificates. The following properties can be set to enable mTLS:
“`
server.ssl.client-auth=need
server.ssl.trust-store-type=PKCS12
server.ssl.trust-store=classpath:truststore.p12
server.ssl.trust-store-password=password
“`
In this example, the server.ssl.client-auth property is set to need to require client certificates. The server.ssl.trust-store-type property specifies the type of truststore (PKCS12 in this case), and the server.ssl.trust-store property specifies the path to the truststore file. The server.ssl.trust-store-password property specifies the password to access the truststore.
FAQs:
1. Why is TLS important in Spring Boot?
TLS is important in Spring Boot as it ensures secure communication between applications over a network. It protects sensitive data from unauthorized access or tampering during transmission, providing confidentiality and integrity. TLS is crucial in scenarios where sensitive information such as passwords, personal data, or credit card details are transmitted.
2. How does TLS work in Spring Boot?
TLS in Spring Boot works by encrypting and decrypting data transmitted between the server and clients. It uses certificates to establish a secure connection between the two endpoints. The server presents its certificate to the client, ensuring the client is communicating with the intended server. TLS also supports mutual authentication, where the client presents its certificate to the server for additional security.
3. Can I use a self-signed certificate in Spring Boot?
Yes, Spring Boot allows the use of self-signed certificates. A self-signed certificate is a certificate generated by the server itself instead of a trusted CA. While self-signed certificates do not offer the same level of trust as certificates from trusted CAs, they can still provide encryption and secure communication between the server and clients.
4. How can I test TLS-enabled applications in Spring Boot?
To test TLS-enabled applications in Spring Boot, you can use tools like cURL or Postman. These tools allow you to send secure requests to the server using HTTPS. You can also configure the tools to use client certificates for testing mTLS scenarios. Additionally, Spring Boot provides support for embedded servers, making it easy to write integration tests for TLS-enabled applications.
5. Can I use different TLS versions in Spring Boot?
Yes, Spring Boot supports different TLS versions. By default, Spring Boot uses the TLS version supported by the underlying Java runtime. However, developers can configure the TLS version by setting the server.ssl.protocol property. For example, to use TLS 1.3, the property can be set as server.ssl.protocol=TLSv1.3.
In conclusion, TLS is an essential component for ensuring secure communication in Spring Boot applications. It provides encryption, data integrity, and authentication, protecting sensitive information from unauthorized access or tampering. Spring Boot simplifies the configuration of TLS settings, allowing developers to focus on building secure applications. By leveraging the power of TLS in Spring Boot, developers can enhance the security of their applications and protect their users’ data.
Config Ssl Tomcat 9
Ensuring the security and confidentiality of data transmitted over the internet is crucial in today’s digital world. To protect sensitive information from unauthorized access, it is essential to implement secure communication channels between the server and clients. One widely adopted method is through the use of SSL (Secure Sockets Layer) certificates. In this article, we will delve into the process of configuring SSL in Tomcat 9, a popular open-source web server and servlet container, and provide a comprehensive guide to help you secure your web applications.
1. Introduction to SSL
SSL is a protocol that establishes an encrypted link between a web server and a client, typically a web browser, to ensure secure communication. It uses cryptographic algorithms to encrypt data, preventing eavesdropping and tampering during transmission. SSL also authenticates the server’s identity, providing confidence to clients that they are connecting to the intended server rather than an imposter.
2. Why Configure SSL in Tomcat 9?
Tomcat 9 is widely recognized for its robustness and versatility in hosting Java-based web applications. When it comes to securing web applications, enabling SSL in Tomcat ensures the confidentiality and integrity of sensitive data transmitted over the network. SSL configuration allows users to access the application using an HTTPS connection, indicating a secure connection and providing peace of mind to both the server owners and end-users.
3. Prerequisites
Before diving into configuring SSL in Tomcat 9, there are a few prerequisites that need to be met:
a. Tomcat 9: Ensure that Tomcat 9 is properly installed and running on your system.
b. Java keystore: Generate or obtain an SSL certificate and convert it into a Java keystore (.jks) format. The SSL certificate can be obtained from a trusted Certificate Authority or self-signed for development and testing purposes.
4. Configuration Steps
Now let’s walk through the steps of configuring SSL in Tomcat 9:
a. Place the SSL certificate in the appropriate directory: Copy the Java keystore file containing the SSL certificate to a preferred location accessible by the Tomcat server. By convention, it is often placed in the conf directory under the Tomcat installation directory.
b. Modify server.xml: Open the server.xml configuration file located in the conf directory. Locate the Connector, which handles incoming connections, and add the following attributes to configure SSL:
i. protocol: Set the protocol as “org.apache.coyote.http11.Http11NioProtocol” to use the NIO connector.
ii. SSLEnabled: Set it to “true” to enable SSL.
iii. keystoreFile: Specify the path to the SSL certificate (e.g., ${catalina.base}/conf/your_keystore.jks).
iv. keystorePass: Provide the keystore password to access the SSL certificate.
v. keystoreType: Set it to “JKS” to indicate the Java keystore type.
5. Restart Tomcat
Once the configuration changes are made, restart the Tomcat server to apply the SSL configuration. After restarting, Tomcat will listen for secure connections on the configured SSL port (default: 8443).
FAQs:
Q1. How can I generate a self-signed SSL certificate for testing purposes?
A: For testing purposes, you can generate a self-signed SSL certificate using the Java keytool utility. Here’s an example command:
keytool -genkey -keyalg RSA -alias your_alias -keystore your_keystore.jks -validity 365 -keysize 2048
Q2. Can I use a purchased SSL certificate from a Certificate Authority?
A: Absolutely! If you have purchased an SSL certificate from a trusted Certificate Authority, you can use that certificate by converting it into the Java keystore format.
Q3. How can I configure Tomcat 9 to enforce HTTPS by default?
A: To enforce HTTPS by default, modify the web.xml file of your web application. Add the following code within the web-app tag:
Q4. Can I configure multiple SSL certificates for different domains in Tomcat 9?
A: Yes, Tomcat 9 supports configuring multiple SSL certificates using the Server Name Indication (SNI) extension. This extension allows the server to determine which SSL certificate to present based on the requested domain.
Conclusion
Configuring SSL in Tomcat 9 is a vital step in securing web applications and safeguarding sensitive data. By following the steps outlined in this article, you can easily enable SSL and establish secure connections, ensuring the confidentiality and integrity of transmitted information. Whether for development, testing, or production environments, SSL configuration in Tomcat 9 is an essential practice for every web application owner.
Images related to the topic this combination of host and port requires tls
![[SOLVED] How to Fix TLS Error Problem (100% Working) [SOLVED] How to Fix TLS Error Problem (100% Working)](https://nhanvietluanvan.com/wp-content/uploads/2023/07/hqdefault-95.jpg)
Found 28 images related to this combination of host and port requires tls theme





Article link: this combination of host and port requires tls.
Learn more about the topic this combination of host and port requires tls.
- Bad Request – This combination of host and port requires TLS …
- Solving ‘This Combination of Host and Port Requires TLS’ Error
- What is Transport Layer Security (TLS)? – Cloudflare
- What is SSL/TLS Encryption? – F5 Networks
- Bad request – This combination of host and port requires TLS.
- Solving ‘This Combination of Host and Port Requires TLS’ Error
- This combination of host and port requires TLS
- Bad Request This combination of host and port requires TLS.
- Bad Request. This combination of host and port requires TLS.
- Bad Request This combination of host and port requires TLS.
- ‘combination of host and port requires TLS’ when running …
See more: nhanvietluanvan.com/luat-hoc