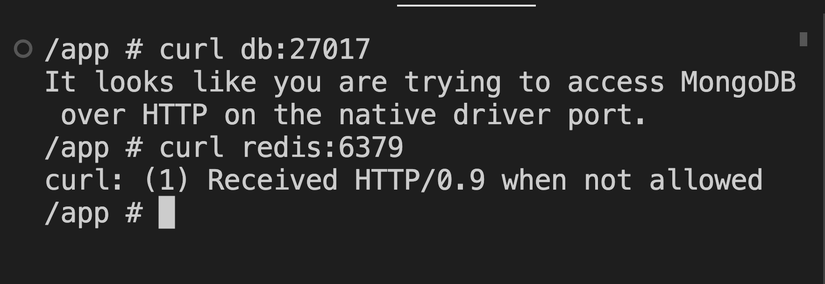
Received Http/0.9 When Not Allowed
Warning: Binary output can mess up your terminal. Use “–output -” to write output to stdout.
The Hypertext Transfer Protocol (HTTP) is a protocol used for communication between web browsers and web servers. It allows for the transfer of various types of media such as HTML, images, videos, and more. HTTP/0.9 is the first version of the protocol, and while it is no longer in use, its remnants can still be found in some instances. This article will delve into the concept of receiving HTTP/0.9 when not allowed, exploring its implications, reasons for disallowance, common errors, potential security risks, strategies for handling requests, best practices for prevention, the importance of keeping web servers updated, and the impact of HTTP/0.9 requests on web performance and user experience.
Definition and Explanation of HTTP/0.9
HTTP/0.9, also known as the Simple Hypertext Transfer Protocol, was introduced by Sir Tim Berners-Lee in 1991 as a simpler version of the protocol. It was designed specifically for retrieving HTML documents, with no support for complex functionality such as headers, status codes, or multiple media types. HTTP/0.9 follows a simple structure where a client sends a request to a server using the GET method, and the server responds by sending the requested document directly without any additional information.
Implications of Receiving HTTP/0.9 When Not Allowed
Receiving HTTP/0.9 requests when not allowed can have several implications for both web servers and clients. For servers, it can create compatibility issues, as modern servers are built to handle higher versions of HTTP, which often involve more complex requests and responses. Not allowing HTTP/0.9 ensures that servers can focus on handling newer versions of the protocol and avoid potential vulnerabilities associated with older versions.
For clients, receiving HTTP/0.9 responses indicates that the server does not support advanced functionality, limiting the features that can be utilized. This can result in a poor user experience, as clients may not be able to access and interact with various elements on a website that rely on newer versions of the protocol.
Reasons for Not Allowing HTTP/0.9
There are several reasons why web administrators may choose not to allow HTTP/0.9 on their servers. Firstly, as mentioned earlier, HTTP/0.9 lacks many features and functionalities that are essential for modern web development and communication. Allowing HTTP/0.9 could limit the capabilities of a server and its ability to handle complex requests efficiently.
Additionally, HTTP/0.9 is more vulnerable to security risks compared to newer versions of the protocol. It does not support secure communication through encryption, making it easier for hackers to intercept and manipulate data transmitted between clients and servers. By disallowing HTTP/0.9, administrators can mitigate potential security breaches and protect the integrity of their systems.
Common Errors that Lead to Receiving HTTP/0.9
Receiving HTTP/0.9 requests can often be a result of misconfigurations or errors within a server setup. One common error is when the server is not updated to support newer versions of the protocol. This can occur when server administrators overlook regularly updating their systems, leading to outdated configurations that still allow HTTP/0.9 requests.
Another common error is incorrect server configuration, where HTTP/0.9 is mistakenly allowed or not properly disabled. This can happen due to human error or inadequate knowledge of the server’s settings and configurations.
Potential Security Risks of Allowing HTTP/0.9
Allowing HTTP/0.9 requests can pose various security risks. As mentioned earlier, HTTP/0.9 does not support encryption, leaving data transmission vulnerable to interception and manipulation. This can potentially lead to unauthorized access, data breaches, or injection of malicious code into the server’s responses.
Furthermore, HTTP/0.9 lacks support for essential security features such as authentication and secure cookies. This makes it easier for attackers to impersonate users or hijack sessions, compromising the security of both server and client.
Strategies for Handling HTTP/0.9 Requests
When a server receives an HTTP/0.9 request, there are a few strategies that can be employed to handle it effectively. One approach is to redirect the request to a new URL using an HTTP status code such as 301 or 302. This allows the server to inform the client that the requested resource can be found elsewhere, ideally using a more recent version of the protocol.
Another strategy is to inform the client about the lack of support for HTTP/0.9 and provide guidance on how to proceed. This can be achieved through an HTML response that displays an error message or a page explaining the server’s requirements for newer versions of the protocol.
Best Practices for Preventing HTTP/0.9 Requests
To prevent receiving HTTP/0.9 requests, it is crucial to follow best practices for server configuration and maintenance. Regularly updating the server software and associated modules ensures that the latest versions of HTTP are supported, while older and outdated versions are disabled.
Furthermore, configuring the server to explicitly disallow HTTP/0.9 requests can help prevent compatibility issues and security vulnerabilities. This can be achieved through the server’s configuration files or by utilizing specific security modules or plugins.
Importance of Keeping Web Servers Updated to Avoid HTTP/0.9 Issues
Keeping web servers updated is crucial to avoid HTTP/0.9 issues. Regular updates ensure that servers remain compatible with newer versions of the protocol, allowing for enhanced functionality and improved security. By staying updated, server administrators can ensure a smooth user experience and minimize the risks associated with older versions of HTTP.
Impact of HTTP/0.9 Requests on Web Performance and User Experience
HTTP/0.9 requests can have a detrimental impact on web performance and user experience. As mentioned earlier, HTTP/0.9 lacks support for advanced features and functionalities, limiting the capabilities of both servers and clients. This can result in slower loading times, limited interactivity, and a less engaging user experience.
Additionally, when a server receives HTTP/0.9 requests, it may need to undertake additional processing to handle and respond appropriately. This can increase server load and degrade performance, leading to potential bottlenecks and slower response times.
In conclusion, receiving HTTP/0.9 requests when not allowed can have various implications for web servers and clients. It is crucial for server administrators to ensure that their systems are properly updated and configured to disallow HTTP/0.9. By staying informed and implementing best practices, administrators can minimize security risks, optimize web performance, and provide users with a seamless and secure browsing experience.
FAQs
Q: What is HTTP/0.9?
A: HTTP/0.9 is the first version of the Hypertext Transfer Protocol, which was introduced in 1991. It is a simpler version of the protocol that only supports basic features for retrieving HTML documents.
Q: Why is receiving HTTP/0.9 when not allowed a problem?
A: Receiving HTTP/0.9 requests when not allowed can create compatibility issues, limit server capabilities, pose security risks, and result in a poor user experience.
Q: How can HTTP/0.9 requests be handled effectively?
A: HTTP/0.9 requests can be handled by redirecting to newer versions of the protocol or providing informative error messages to the client.
Q: What are the security risks of allowing HTTP/0.9?
A: Allowing HTTP/0.9 requests can lead to potential data interception, manipulation, unauthorized access, and compromised sessions due to the lack of encryption and security features.
Q: How can HTTP/0.9 requests be prevented?
A: Preventing HTTP/0.9 requests involves keeping web servers updated, explicitly disallowing HTTP/0.9, and following best practices for server configuration and maintenance.
Q: What is the impact of HTTP/0.9 requests on web performance and user experience?
A: HTTP/0.9 requests can result in slower loading times, limited interactivity, increased server load, and a degraded user experience due to the lack of advanced features and functionalities.
What Is Http/0.9 Request? (2 Solutions!!)
Keywords searched by users: received http/0.9 when not allowed Warning: Binary output can mess up your terminal use output -” to tell, CURLOPT_NOBODY
Categories: Top 52 Received Http/0.9 When Not Allowed
See more here: nhanvietluanvan.com
Warning: Binary Output Can Mess Up Your Terminal Use Output -” To Tell
In the world of programming and computer systems, binary is the backbone of information representation. While it is a highly efficient way to store and process data, working with binary output can be a daunting task, especially when it comes to handling it in your terminal.
Binary output refers to data that is encoded in a series of 0s and 1s. This form of representation is the basis of how computers store and manipulate information. While it may seem like a far cry from our everyday understanding of numbers and text, binary is a fundamental component of computer systems.
When dealing with binary output, you typically encounter it in the form of binary files. These files contain data that is not intended for direct human consumption, but rather for the computer to interpret and process. Examples of binary files include executables, compressed archives, and image files.
So, what’s the issue with binary output and your terminal? Well, terminals are primarily designed to handle human-readable text and interpret it accordingly. When you encounter binary output in your terminal, it can lead to a wide array of problems, ranging from displaying gibberish characters to potentially crashing your terminal program.
When you mistakenly output binary data to your terminal, it tries to interpret the sequence of 0s and 1s as characters according to the default character encoding. The characters generated can be invalid or unprintable, causing your terminal to display strange symbols or garbled text. Furthermore, if the binary output contains control characters, they can interfere with the terminal’s behavior, resulting in unexpected effects or even causing the terminal to freeze.
The easiest way to avoid these issues is to simply refrain from outputting binary data to your terminal. However, if you do need to check the contents of a binary file or inspect binary output, there is a convention commonly used in programming languages to denote binary data.
By convention, the empty string, denoted by ”, is often used to indicate binary output. When you encounter this in documentation or programming languages, it serves as a visual cue to warn you that the output is not meant to be directly displayed in your terminal but instead used for further processing or inspection.
To demonstrate how the empty string convention works, let’s consider a simple example using the Python programming language:
“`
binary_data = b’\x48\x65\x6c\x6c\x6f\x2c\x20\x77\x6f\x72\x6c\x64′
print(binary_data.decode(‘utf-8’))
“`
In this example, we have a binary string `binary_data` that contains the hexadecimal representation of the phrase “Hello, world.” To display the actual text in our terminal, we explicitly decode it using the UTF-8 encoding. This way, we ensure that the binary output is correctly interpreted and rendered as intended.
Now, let’s move on to some frequently asked questions about handling binary output in terminals:
Q: Can I simply copy and paste binary data into my terminal?
A: No, copying and pasting binary data directly into your terminal is not recommended. It can lead to unexpected results and potentially harm your system’s stability. Instead, opt for using appropriate tools or programming languages to handle binary data.
Q: Can binary output harm my terminal or computer?
A: Binary output itself does not pose a direct threat to your terminal or computer. However, mishandling it can cause unintended consequences, such as freezing your terminal or rendering it unusable temporarily. Always exercise caution and use the appropriate means to handle binary data.
Q: I accidentally output binary data to my terminal and now it is displaying strange characters. What should I do?
A: If you encounter garbled or strange characters due to binary output, your terminal might be in an inconsistent state. In such cases, it is recommended to close and reopen your terminal program to restore normal functionality.
In conclusion, binary output can wreak havoc on your terminal, making it challenging to interpret and potentially affecting its stability. By avoiding outputting binary data directly, understanding the convention of using the empty string (”) to denote binary output, and employing proper encoding techniques when necessary, you can safely navigate the binary world without compromising your terminal experience.
Curlopt_Nobody
cURL, an acronym for “Client for URLs”, is a powerful command-line tool and library used for performing various operations involving URLs. It supports a wide range of protocols such as HTTP, HTTPS, FTP, SMTP, and many more. One of the key functionalities offered by cURL is retrieving information from remote servers. When doing so, you can choose to obtain the entire response, including the response body, or only the response headers. In this article, we will dive deep into CURLOPT_NOBODY, an option offered by cURL that allows you to fetch only the headers and not the response body, reducing unnecessary data transfer and improving performance.
Understanding CURLOPT_NOBODY:
CURLOPT_NOBODY is an option provided by cURL that allows you to configure a request to retrieve only the response headers. When CURLOPT_NOBODY is set to 1, cURL eliminates the transfer of the response body, resulting in a substantially smaller amount of data transfer. This can be particularly useful in scenarios where you are more interested in the metadata of a response, such as information about the server, content type, response status code, or cookies, rather than the actual content of the response.
Usage of CURLOPT_NOBODY:
To utilize CURLOPT_NOBODY in cURL, you need to set the CURLOPT_NOBODY option to 1 using the curl_easy_setopt() function. Let’s take a look at an example demonstrating how to fetch only the response headers using cURL in C++:
“`
#include
int main() {
CURL* curl = curl_easy_init();
if (curl) {
curl_easy_setopt(curl, CURLOPT_URL, “https://example.com”);
curl_easy_setopt(curl, CURLOPT_NOBODY, 1);
CURLcode res = curl_easy_perform(curl);
if (res != CURLE_OK) {
fprintf(stderr, “curl_easy_perform() failed: %s\n”, curl_easy_strerror(res));
}
curl_easy_cleanup(curl);
}
return 0;
}
“`
In this example, we first initialize a cURL session using `curl_easy_init()`. Then, we provide the URL we want to fetch headers from using `CURLOPT_URL`. By setting `CURLOPT_NOBODY` to 1, cURL ensures it fetches only the headers without the response body. Finally, we call `curl_easy_perform()` to execute the request. If any errors occur, we handle them appropriately. After performing the request, we clean up the cURL session using `curl_easy_cleanup()`.
Benefits and Use Cases:
Using CURLOPT_NOBODY provides several benefits. Firstly, it reduces the amount of data transfer between the client and server. If you’re dealing with large files or bandwidth-constrained environments, fetching only the response headers can significantly optimize your application’s performance and efficiency. Additionally, it can save both time and server resources when you don’t actually need the response body. Secondly, by obtaining only the headers, you can extract essential information provided by the server, such as the content type, content length, or server version. This metadata enables you to make informed decisions, process the headers efficiently, and handle various scenarios accordingly.
Frequently Asked Questions (FAQs):
Q: Are there any limitations or drawbacks when using CURLOPT_NOBODY?
A: While CURLOPT_NOBODY can be beneficial in reducing unnecessary data transfer, it has a few limitations. It’s important to note that when using this option, you won’t have access to the response body, which could be problematic if you later require the content. Additionally, some servers may not support fetching only headers and may send the entire response anyway.
Q: How does CURLOPT_NOBODY affect the response time?
A: In most cases, using CURLOPT_NOBODY will reduce the response time since it eliminates the transfer of the response body. It becomes particularly noticeable when dealing with large files or slower network connections.
Q: Can CURLOPT_NOBODY be used with protocols other than HTTP?
A: Yes, CURLOPT_NOBODY is protocol-agnostic and can be used with various protocols supported by cURL, including HTTPS, FTP, SMTP, and more.
Q: How can I access the response headers obtained using CURLOPT_NOBODY?
A: With cURL, you can utilize the CURLOPT_HEADERFUNCTION option and pass a callback function to process the headers received. In the callback function, you can extract and handle the headers accordingly.
Q: Can I use CURLOPT_NOBODY in combination with other cURL options?
A: Yes, you can use CURLOPT_NOBODY in conjunction with other cURL options to customize your request according to your needs. For example, you can set additional headers, add custom user agents, or handle cookies alongside CURLOPT_NOBODY.
In conclusion, CURLOPT_NOBODY is a valuable option offered by cURL that allows you to fetch only the response headers and eliminate unnecessary data transfer. By understanding and utilizing CURLOPT_NOBODY effectively, you can optimize your application’s performance, reduce bandwidth usage, and process essential metadata provided by the server.
Images related to the topic received http/0.9 when not allowed

Found 19 images related to received http/0.9 when not allowed theme





Article link: received http/0.9 when not allowed.
Learn more about the topic received http/0.9 when not allowed.
- cURL Received HTTP/0.9 when not allowed, but nghttp2 is …
- PHP Curl – Received HTTP/0.9 when not allowed
- Error “curl: (1) Received HTTP/0.9 when not allowed” (SOLVED)
- Error “Received HTTP/0.9 when not allowed” when using Data …
- Received HTTP/0.9 when not allowed – RStudio Community
- received HTTP/0.9 when not allowed – CSPro Users Forum
- How to monitor a HTTP/0.9 server – ZABBIX Forums
- CURLOPT_HTTP09 – allow HTTP/0.9 response
See more: nhanvietluanvan.com/luat-hoc